Channelization Protocols Explained
Last updated: March 18, 2024
- Network Protocols

1. Introduction
In this tutorial, we’ll explain the channelization protocols used in the media access control (MAC) sub-layer of the datalink layer in the OSI model to coordinate data transmission by multiple users through a channel.
2. Channelization and Channelization Protocols
We must constantly develop and enhance methods by which more users can connect and transmit information via a link, also known as a channel, without colliding or interfering.
According to the OSI model, the data link layer (DLL) transmits data through a network channel from one node to another. We subdivided the DLL into the logical link control (LLC) layer and the media access control (MAC) layer, each with its own set of protocols.
We employ the LLC sub-layer when using a dedicated link to send data from one node to another. In contrast, multiple users would attempt to use the available channel to send data concurrently if dedicated channels were unavailable. This could result in a collision. To coordinate this kind of data transmission, we employ the MAC sub-layer.
Channelization is the process by which we coordinate the transmission of data in non-dedicated channels to prevent collision and crosstalk, and channelization protocols are the MAC protocols we employ to coordinate this transmission.
Channels are communication resources we assign to a user to establish communication with other users in the network. These resources include frequency, time, code, space, bandwidth , and so on. We name each channelization protocol based on the kind of channel resources we employ for channelization. These protocols are:
- Frequency division multiple access (FDMA)
- Time division multiple access (TDMA)
- Code division multiple access (CDMA)
- Space division multiple access (SDMA)
- Orthogonal Frequency division multiple access (OFDMA)
Now let’s explain each protocol one by one.
3. Frequency Division Multiple Access (FDMA) Protocol
We design the FDMA protocol by utilizing the channel resource of frequency. By dividing the channel’s bandwidth into non-overlapping frequency bands or slices, we allocate each user a distinct band for exclusive transmission and reception . This enables the concurrent operation of multiple users within a single communication channel. To mitigate interference and crosstalk during data transmission, we equip each user with a customized bandpass filter complemented by a small guard band.
The following figure depicts the FDMA protocol scenario:
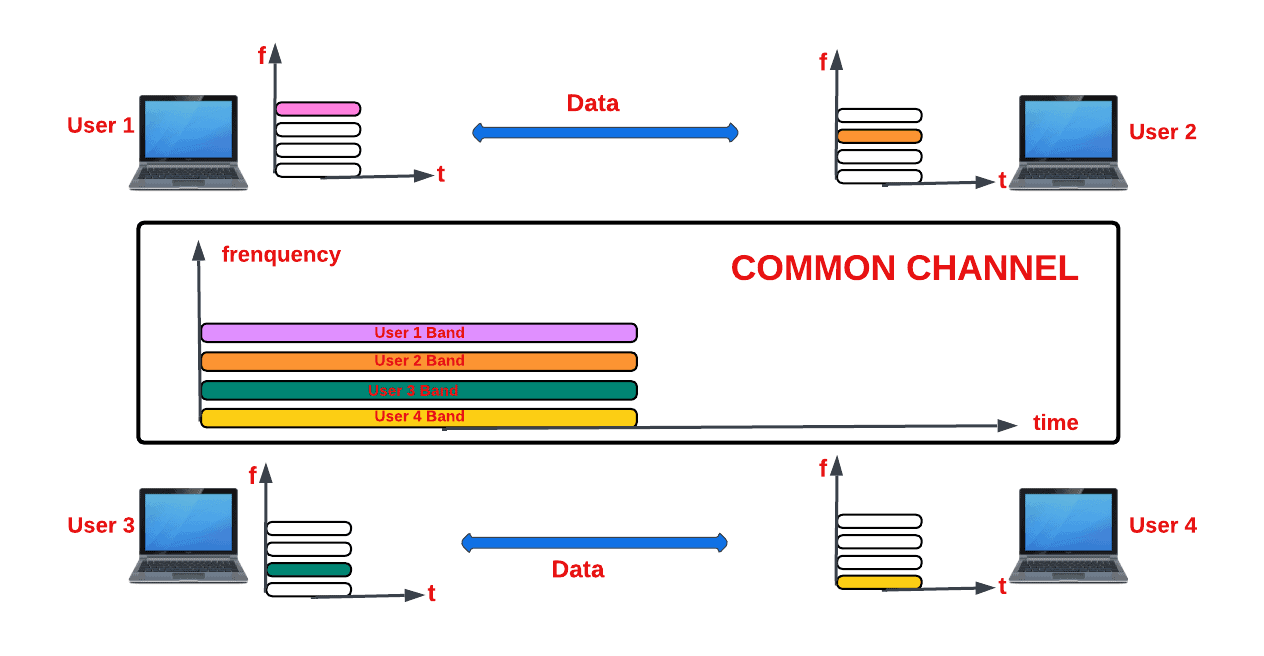
As seen in the above diagram, four users are attempting to access the same channel. To accommodate the four users without interfering with one another, we utilize FDMA to split the channel into four frequency bands.
3.1. Merits and Limitations of FDMA Protocols
Some notable merits which FDMA protocols offer us are:
- enable simultaneous transmission through the same frequency channel, with each user operating at a single frequency
- using frequency as the channel resource eliminates timing-related issues often encountered in TDMA protocols
- FDMA effectively resolves the near-far problem inherent in CDMA protocols by implementing bandpass filtering
- as we assign users frequency slots, this allows for distinct transmission and reception at different frequencies
However, the FDMA protocol does come with two significant limitations:
- the design of high-performing hardware filters proves to be a challenging task
- despite the inclusion of guard bands, FDMA remains susceptible to crosstalk, potentially leading to interference and transmission disruptions
3.2. Frequency Allocation Schemes in FDMA Protocols
Regarding frequency slot assignment within the FDMA protocol, we employ two common methods, which are:
- Fixed assignment multiple access (FAMA)
- Demand assignment multiple access (DAMA)
We use FAMA to allocate frequency slots to users whether they utilize it or not, ensuring a fixed allocation scheme. On the other hand, we use DAMA to assign frequency slots to users only upon their explicit request, offering a more dynamic and efficient resource allocation approach.
4. Time Division Multiple Access (TDMA) Protocol
Time serves as the channel resource for this protocol. Using the TDMA protocol, we divide each user’s signal into a different time slot and assign each time slot to a different user . This technique enables numerous users to share and use the same frequency channel. The global system of mobile communication (GSM) system, a 2G cellular system, is one significant application where we have used the TDMA protocol.
A typical TDMA protocol looks like this:
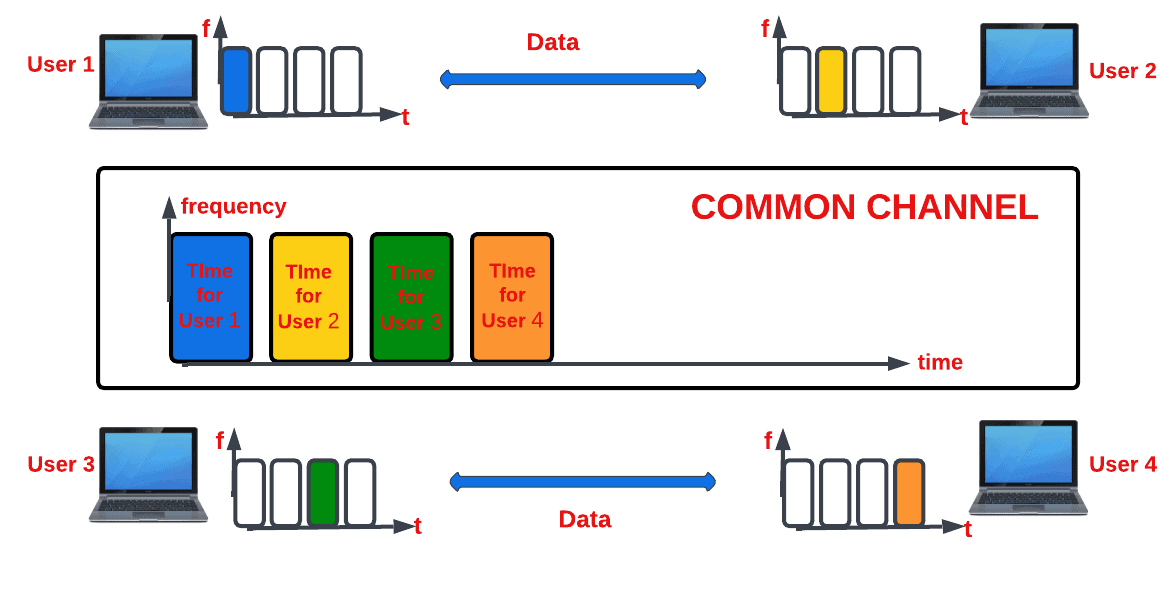
Synchronizing the various users of the channel is one of the biggest challenges we face when utilizing the TDMA protocol. To achieve synchronization, we ensure each user knows their respective slots’ start and endpoints. This is difficult to achieve, especially if the users are spread over a large area. To minimize this challenge, we insert guard times to each user channel.
Another significant drawback we encounter when utilizing TDMA systems is the potential for causing interference at a frequency that closely adjoins another user’s active time slot. This interference manifests as the buzzing sound we occasionally hear when a TDMA phone is near a radio or speakers.
Just like in the FDMA protocol, there are two methods we use to administer time slots to users:
- Fixed time division multiple access (F-TDMA)
- Dynamic time division multiple access (D-TDMA)
While we use F-TDMA for fixed allocation of time slots to users, we use D-TDMA to assign time slots to users based on the traffic demand of the channel.
5. Code Division Multiple Access (CDMA) Protocol
The channel resource for this protocol is code. I n the CDMA protocol, we allow multiple users to simultaneously transmit their data signals over the entire bandwidth of the common channel by assigning unique spreading codes to each user . This technique helps us utilize the channel more effectively.
Let’s see what a CDMA protocol looks like:
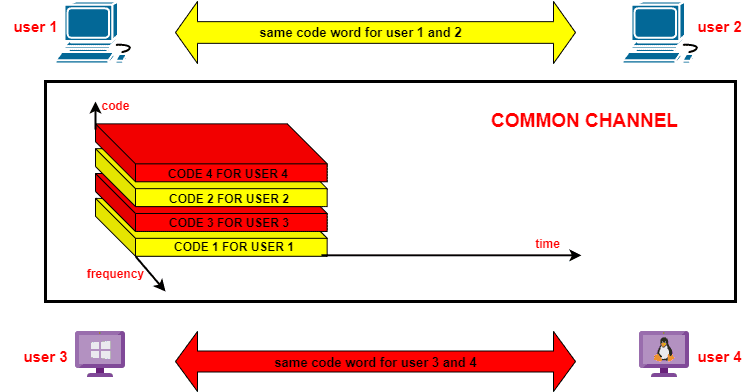
The beauty of this protocol is that we don’t share the frequency as we do in FDMA, and neither do we share time as we do in TDMA. In CDMA, we employ both time and frequency for users to send their data over the entire bandwidth of the channel with a unique spreading code allotted to the user. Only receivers having this unique code can receive the sent messages.
In CDMA, we use the spread spectrum principle to utilize unique transmission codes . Let us discuss this principle more in-depth.
5.1. Spread Spectrum
Spread spectrum is a technique that enables us to transfer signals via communication channels by purposefully extending the signal’s bandwidth beyond what is necessary for transmission . We expand the signal bandwidth in order to keep transmission interference to a bare minimum. To offset the waste of bandwidth due to overspreading, we allow multiple users to access the channel.
We implement the spread spectrum in two ways:
- Direct sequence spread spectrum (DSSS)
- Frequency hopping spread spectrum (FHSS)
Let’s now discuss each method.
In DSSS, we multiply the message signal with a locally generated spreading pseudorandom noise (PN) code, which we refer to as chips, to widen the signal’s bandwidth . By multiplying the signal, we broadcast at the receiver by a locally produced copy of the PN code sequence, and we can decode the information. We have incorporated DSSS into GPS and Wi-Fi networks.
To spread the message signal in FHSS, we transmit it with rapidly changing carrier frequencies among several frequencies occupying a large bandwidth . We control the “frequency hopping” of the message signal by a PN code known to the sender and receiver. In this way, we send and receive data without interference and eavesdropping.
We employ two strategies to manage CDMA protocols based on spread spectrum technologies:
- Direct sequence code division multiple access (DS-CDMA)
- Frequency hopping code division multiple access (FH-CDMA)
Based on the same logic as their spread spectrum counterparts, we apply these techniques.
5.2. Advantages and Disadvantages of CDMA
CDMA offers several advantages over other communication technologies, such as FDMA and TDMA. Firstly, CDMA significantly increases user capacity compared to FDMA and TDMA. Moreover, it allows for simultaneous voice and data communication, which is impossible with TDMA and FDMA.
Another significant advantage of CDMA is its high level of security in transmitting information. In CDMA, we employ a unique code for each user, making accessing information difficult for unauthorized users. Additionally, the probability of interference is minimal in CDMA, providing reliable communication.
Furthermore, CDMA enables us to use the entire spectrum, offering more flexibility in communication. With CDMA, we can take advantage of the entire bandwidth available, which is impossible with FDMA or TDMA.
Despite its advantages, CDMA also has some significant drawbacks that must be considered. Firstly, the system’s operation is highly complex, making it difficult to set up and maintain.
Moreover, In CDMA, we use orthogonal codes for both the sender and the receiver in a synchronous manner to recover the original data accurately. If this requirement is unmet, the system experiences self-jamming, making communication challenging.
6. Space Division Multiple Access (SDMA)
In this protocol, we utilize space as the channel resource. We allocate the same frequency to users that are separated by a certain distance, which we refer to as the reuse distance . To accomplish this, we employ a smart and highly directional antenna that directs a beam of radio waves to a specific location in space where a user is located.
To enable the reuse of the same channel, we use another smart and highly directional antenna to beam his signal to a different location in the same space where other users are located. This smart antenna system is known as a Multiple Input Multiple Output (MIMO) system.
A typical SDMA protocol looks like this:
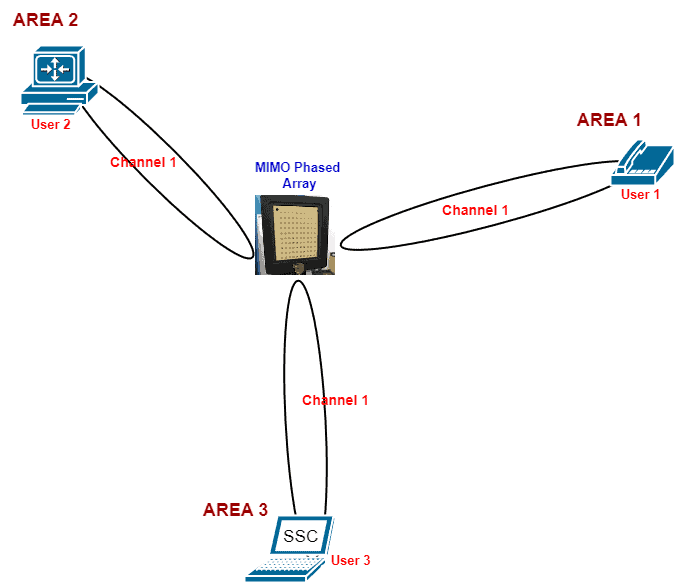
From the figure, we see that the same channel-1 is reused to send data to three different users because a reuse distance separates them.
By using a highly directional beam, we can minimize interference and improve the quality of communication for users in the network. Additionally, the MIMO system can increase the network’s capacity by allowing multiple users to communicate simultaneously without affecting each other’s signals.
This protocol provides us with some merits:
- it helps us to optimize the use of power and minimize the wastage of energy
- we are able to save the channel bandwidth and utilize it more effectively
- it helps us reduce interference to near zero
- we can control and regulate the energy we radiate to the receiver
To achieve the full potential of the SDMA protocol, we must carefully design it, which we always find very tedious.
7. Orthogonal Frequency Division Multiple Access (OFDMA)
As the world is witnessing an increasing demand for individual data consumption, we recognize the necessity to enhance the existing protocol standards to meet this demand. To address this, we devised a solution that merged the benefits of FDMA and TDMA protocols in an orthogonal fashion, thereby preventing interference.
This innovation led to the emergence of the OFDMA protocol. To accomplish this, we utilized the channel resource by combining frequency and time in an orthogonal manner. Now, let’s delve into the functionality of the OFDMA protocol:
The OFDMA protocol actively takes a channel and partitions it into smaller frequency units which we know as resource units (RUs). We then allocate these RUs to users according to their respective data consumption demands .
For instance, if a user intends to send an email, we assign a small RU due to the minimal data requirement. Conversely, a user aiming to video call their boss receives a larger RU allocation.
To ensure interference avoidance, we divide the RUs in an orthogonal manner. Subsequently, we employ a single access point (AP) to aggregate all assigned users to their respective RUs, facilitating the delivery of their messages to the intended recipients.
Thanks to the dynamic efficiency we embedded in the design of the OFDMA protocol, we can assign receivers RUs based on the data size they expect to receive.
This is a typical OFDMA protocol layout:
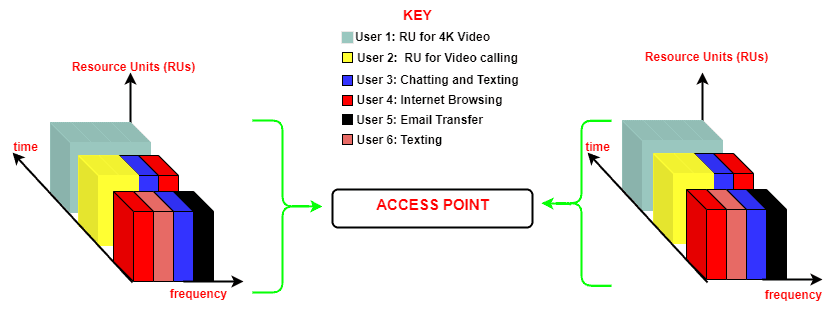
The OFDMA protocol significantly mitigates the unpredictability experienced by users in highly congested areas by enabling more users to connect concurrently to a single access point (AP). In doing so, OFDMA effectively addresses congestion issues.
Furthermore, this protocol exemplifies exceptional efficiency by seamlessly allocating either the entirety of a channel or dividing it to accommodate multiple users, depending on the specific traffic demands.
8. Conclusion
In this article, we discussed how channelization protocols play a critical role in optimizing the utilization of communication channels in various systems. We showed that each protocol possesses unique advantages and challenges tailored to specific requirements and environments.
Open Access is an initiative that aims to make scientific research freely available to all. To date our community has made over 100 million downloads. It’s based on principles of collaboration, unobstructed discovery, and, most importantly, scientific progression. As PhD students, we found it difficult to access the research we needed, so we decided to create a new Open Access publisher that levels the playing field for scientists across the world. How? By making research easy to access, and puts the academic needs of the researchers before the business interests of publishers.
We are a community of more than 103,000 authors and editors from 3,291 institutions spanning 160 countries, including Nobel Prize winners and some of the world’s most-cited researchers. Publishing on IntechOpen allows authors to earn citations and find new collaborators, meaning more people see your work not only from your own field of study, but from other related fields too.
Brief introduction to this section that descibes Open Access especially from an IntechOpen perspective
Want to get in touch? Contact our London head office or media team here
Our team is growing all the time, so we’re always on the lookout for smart people who want to help us reshape the world of scientific publishing.
Home > Books > Wireless Mesh Networks - Efficient Link Scheduling, Channel Assignment and Network Planning Strategies
Channel Assignment Schemes Optimization for Multi-Interface Wireless Mesh Networks Based on Link Load
Submitted: 16 December 2011 Published: 14 August 2012
DOI: 10.5772/46100
Cite this chapter
There are two ways to cite this chapter:
From the Edited Volume
Wireless Mesh Networks - Efficient Link Scheduling, Channel Assignment and Network Planning Strategies
Edited by Andrey V. Krendzel
To purchase hard copies of this book, please contact the representative in India: CBS Publishers & Distributors Pvt. Ltd. www.cbspd.com | [email protected]
Chapter metrics overview
2,079 Chapter Downloads
Impact of this chapter
Total Chapter Downloads on intechopen.com
Total Chapter Views on intechopen.com
Author Information
Stefan pollak, vladimir wieser.
*Address all correspondence to:
1. Introduction
In recent years, wireless mesh networks (WMNs) were deployed as a type of next generation wireless broadband networks. WMNs provide wireless broadband accessibility to extend the Internet connectivity to the last mile and improve the network coverage. WMN consists of a set of mesh routers and mesh clients ( Fig. 1) . Mesh routers are usually stationary and form multi-hop wireless backbone network (i.e. mesh routers are interconnected with each other via wireless medium). Some or all of the mesh routers also serve as access points for mobile users ( mesh clients ) under their coverage. Usually one or more mesh routers have direct connections to wired network and serve as Internet gateways for the rest of the network. These nodes are called mesh gateways . Compared to traditional wireless LANs, the main feature of WMNs is their multi-hop wireless backbone capability ( Conti et al., 2007 ).
Traditionally, wireless networks are equipped with only one IEEE 802.11 radio interface. However, a single-interface inherently restricts the whole network by using only one single channel ( Fig. 3a) . In order to communicate successfully, two neighboring routers have to build a logical link which operates on a common channel. Due to that, all wireless nodes have to use only one radio interface, all logical links in network must use the same channel. If two neighboring links operate on the same channel and transfer data simultaneously, then they definitely interfere with each other. The network capacity and the performance may degrade significantly because of the interference ( Gupta & Kumar, 2000 ). The key factor for reducing the effect of interference is the using of non-overlapping channels (standard IEEE 802.11b/g provides 3 and standard IEEE 802.11a up to 12 non-overlapping channels) ( Ramachandran et al., 2006 ). In practice, IEEE 802.11b/g defines 11 communication channels (number of communication channels varies due to regulations of different countries) but only 3 of them are non-overlapping ( Fig.2) .

WMN architecture

Channel spectrum occupation in IEEE 802.11b/g
Using multiple non-overlapping channels in single interface network disconnects the subset of nodes using one channel from other nodes that are not using the same channel ( Fig. 3b) . For this reason this approach generally requires MAC layer modification and per packet channel switching capability for radio interfaces ( Marina & Das, 2005 ). Before every data transmission a channel selection mechanism evaluates the available channels and selects a channel to transmit. There are also some problems introduced with channel switching mechanism. These problems include multi-channel hidden terminal problem, broadcast problem, deafness problem and channel deadlock problem ( Raniwala et al., 2004 ).
One of the most promising approaches lies in using multiple radio interfaces and multiple non-overlapping channels ( Fig. 3c) . This solution is better than previous one, because of providing the effective usage of given frequency spectrum ( Conti et al., 2007 ). This architecture overcomes deficiencies of single interface solution. It allows using of multiple interfaces per node to allow the simultaneous transmission and reception on different radio interfaces tuned to different channels, which can essentially improve network capacity. However, the number of radio interfaces is always much higher than the number of effective channels, which causes an existence of many different links between mesh routers operating on the same channel. For this reason, the suitable channel assignment method is needed to maintain the connectivity between mesh nodes and to minimize the effect of interference ( Raniwala et al., 2004 ).
The channel assignment (CA) in a multi-interface WMN consists of a task to assign channels to the radio interfaces by such a way to achieve efficient channel utilization and to minimize the interference. The problem of optimally assigning channels in an arbitrary mesh topology has been proved to be NP-hard (non-deterministic polynomial-time hard) based on its mapping to a graph-coloring problem. Therefore, channel assignment schemes predominantly employ heuristic techniques to assign channels to radio interfaces belonging to WMN nodes.
The channel assignment algorithms can be divided into three main categories: fixed, dynamic and hybrid, depending on the frequency with which it is modified by the channel assignment scheme. In a fixed scheme, the CA is almost constant, while in a dynamic one it is continuously updated to improve performance. A hybrid scheme applies a fixed scheme for some radio interfaces and dynamic one for the others ( Yulong Chen et al., 2010 ).

Different types of WMNs
The main objective of this chapter is to give to reader the compact information about problems connected with optimal using of radio interfaces and radio channels in wireless mesh networks. The optimal using is computed from several different points of view, e.g. network topology, number of data flows, number of nodes by comparison of selected QoS parameters. In the second part of the chapter, the new proposed centralized channel assignment concept called First Random Channel Assignment algorithm (FRCA) is compared with two other channel assignment techniques (CCA, LACA) by the same QoS parameters.
The rest of this chapter is organized as follows. In section 2, the related work is summarized. In section 3, the methods and simulation results to find the optimal number of radio interfaces per node are introduced. In section 4 the mathematical background and graph based mathematical model is described and in the next section different types of channel assignment methods based on links load are analyzed. Section 6 concludes the chapter.
2. Related work
There exist a large number of studies which address the channel assignment problem in wireless mesh networks. Several works have proposed MAC protocols for utilizing multiple channels ( So & Vaidya, 2004 , Gong & Midkiff, 2005 ), but these multi-channel protocols require changes to existing standards and therefore cannot be deployed by using existing hardware. In ( Adya et al., 2004 ) was proposed a link-layer solution for transmitting data over multiple radio interfaces, but this approach is designed for scenario where the number of radio interfaces is equal to the number of channels. In ( Gupta & Kumar, 2000 ) the performance of multi-channel ad-hoc networks was studied, where each channel was assigned to an interface. In ( Draves et al., 2004 ) several methods for increasing the performance in single-channel per interface were proposed. The most studies is focused only to one problem - to find the efficient channel assignment method, but did not suggest the optimal number of radio interfaces per node. In ( Husnain et al., 2004 ) were compared different static centralized algorithms, but for evaluation of optimal number of radio interfaces was used only one parameter - total interference (number of links in conflict graph). ( Raniwala et al., 2004 ) proposed centralized channel assignment and routing method, where results about number of radio interfaces were shown but only for network cross-section goodput. In (C hi Moon Oh et al., 2008 ) the study of optimal number of radio interfaces was created but only for grid network, using simple channel assignment method and for one QoS parameter (throughput).
3. The study of optimal number of radio interfaces
In this section several simulations were created to find the optimal number of radio interfaces for static WMN. In this study we focus only to one problem - to find the optimal number of radio interfaces for different conditions therefore, for channel assignment we used simple CCA approach (section 5.1).
Nowadays the availability of the cheap off-the-shelf commodity hardware also makes multi-radio solutions economically attractive. This condition provides the using much more radio interfaces per node, which shows the investigating of optimal number of interfaces as a reasonable argument.
We have included in our simulations several QoS parameters, data flows, number of nodes and network topologies to find the optimum number of radio interfaces for services which required the real time transmission (e.g. video conference).
3.1. Simulation environment
A simulation WMN model was developed in NS-2 network simulator, with additional function to support multi-channel and multi-interface solution ( Calvo & Campo, 2007 ). Each mesh node used the number of interfaces between 1 to 8 and the same number of channels. Two different network topologies were created. The first one was grid topology, which consisted of 25 static wireless mesh nodes placed in an area of 1000 x 1000 meters. Transmission range for each node was set to 200 meters ( Fig.4a) . The second topology consists of 25 nodes, which were randomly placed in an area of 1000 x 1000 meters ( Fig.4b) . For simulation evaluations, ten random topologies and computed average values of chosen QoS parameters were studied. We have used the WMN with 25 nodes, because of the typical number of mesh nodes in WMN (25 to 30) ( Skalli et al., 2006 ). For traffic generation, 5 CBR (Constant Bit Rate) flows were used and the packet size was set to 512 bytes. The same radio default parameters as in ( ns-2, 2008 ) were used, except that we set the channel data rate to 11 Mbit/s. Simulation parameters are summarized in Table 1 .
| Test Area | 1000x1000 m |
| Mac protocol | IEEE 802.11 |
| Propagation model | Two ray ground |
| Routing protocol | AODV |
| Antenna type | Omni-directional |
| Traffic type | CBR |
| Packet size | 512 bytes |
| Simulation time | 100 seconds |
Simulation parameters

Grid (a) and random (b) topology of static WMN created in NS-2 simulator
3.2. Simulation results
In this section results of experiments are presented. The purpose of simulation was to determine the optimal number of radio interfaces for different WMN topologies, different number of data flows and different number of nodes to achieve the network capacity increasing expressed in enhancement of QoS parameters.
We chose four QoS parameters for simulation evaluation:
Average End-to-end Delay : The average time taken for a packet to reach the destination. It includes all possible delays in the source node and in each intermediate host, caused by queuing at the interface queue, transmission at the MAC layer, routing discovery, etc. Only successfully delivered packets are counted.
Average Throughput : The sum of data packets delivered to all nodes in the network in a given time unit (second).
Packet Loss : Occurs when one or more packets being transmitted across the network fail to arrive at the destination.
Average Jitter : The delay variations between all received data packets.
3.2.1. Different network topologies
In this simulation we created two different network topologies of WMN (grid topology and random topology). Ten random topologies were created and average values of chosen QoS parameters were computed.

Average values of end-to-end delays for various radio interfaces and different network topologies
Figure 5 shows the average values of end-to-end delay for various numbers of radio interfaces and two different network topologies. From results it is obvious that the highest value of end-to-end delay (0.92 sec) was reached in the grid WMN with one radio interface. The lowest value of delay (0.0097 sec) was achieved in grid WMN with seven radio interfaces. In WMN with random topology, the lowest value of delay (0.049 sec) was achieved in WMN with six radio interfaces. The best values of average delay were achieved in WMN with random topology, but differences between values of random and grid topologies were small for higher number of radio interfaces. From results it may be concluded that optimal number of radio interfaces which guarantee the maximum allowable average delay 150 ms ( ITU-T, 2003 ) for both network topologies is five, because more than five interfaces improved value of end-to-end delay only slightly, but the complexity of node is increased considerably.
Figure 6 shows the average values of network throughput for various numbers of radio interfaces and two different network topologies. The lowest value of average throughput was achieved in grid WMN, where nodes have used for transmission only one radio interface. In this case, the value of average throughput was 504.28 kbps. In the case where WMN with random topology and one radio interface was used, the lowest value of average throughput (739.3 kbps) was achieved. The highest value of throughput (2019.9 kbps) reaches the grid WMN with seven radio interfaces. The best value of average throughput in random WMN topology (1964.2 kbps) was achieved by WMN with seven radio interfaces. Again, the optimal number of interfaces for both network topologies was chosen as five.

Average values of throughput for various radio interfaces and different network topologies
As we can see from Fig.7 , the highest value of packet loss (75.1%) was reached in grid WMN with one radio interface. The lowest value of packet loss was achieved in WMN with seven radio interfaces. This value was 3.5% for the random topology and 2.5% for grid topology. As in the previous case, we can conclude the optimal number of radio interfaces as five, where grid topology achieved 9.8% of packet loss and 7.6% for random topology.
Figure 8 shows the average values of time jitter for different types of topologies and various number of radio interfaces. From results it is obvious that the highest value of average jitter was reached in the network with one radio interface. For the random topology this value was 0.7 sec and for grid topology it was 0.8 sec. On the other hand the lowest values of average jitter were achieved in grid WMN with seven interfaces (0.3 sec) and in random WMN with six interfaces (0.05 sec). As an optimal number of radio interfaces, the number of six was selected with average jitter value 0.11 sec for random topology and 0.14 sec for grid topology.

Values of packet loss for various radio interfaces and different network topologies

Average values of jitter for various radio interfaces and different network topologies
3.2.2. Different number of data flows
Simulation model consisted of 25 static wireless mesh nodes placed in grid in area 1000x1000 m ( Fig.4a) . Transmission range for each node was set to 200 m. As traffic transmission, the 5, 10, 15 and 20 CBR flows were simulated and packet size of 512 bytes was used. Data flows were created between random chosen node pairs.
Figure 9 shows the average values of end-to-end delay for different number of data flows. From results it is obvious that the best performance was achieved in multi-interface WMN with six interfaces, when the number of flows changed. The highest value of average end-to-end delay (for all data flows) was reached by WMN with one radio interface. For small number of data flows (5), WMN with 5 interfaces reached the best performance, whilst for 10 data flows the best performance was reached by 6 interfaces. For more data flows (15 and 20) the system performance is unsatisfactory regardless of number of interfaces.

Average values of end-to-end delay for various radio interfaces and different number of data flows
Figure 10 shows the simulation results of average values of network throughput for the 5, 10, 15 and 20 data flows. The lowest value of average throughput was achieved in grid WMN with only one radio interface. From results it is obvious that the highest value of average throughput was reached in the multi-interface WMN with six radio interfaces. In the WMN with more than six interfaces the network performance is decreasing.

Average values of throughput for various radio interfaces and different number of data flows
As we can see from Figure 11 , the best value of packet loss was reached in multi-interface WMN with six radio interfaces. The highest value of packet loss was reached in WMN, where nodes used for transmission one radio interface.
Figure 12 shows the average values of jitter for the different number of data flows. The highest values were achieved in WMN, where nodes have used for transmission only one radio interface. The best value of average jitter for all data flows was achieved in WMN with five or six radio interfaces.

Values of packet loss for various radio interfaces and different number of data flows

Average values of jitter for various radio interfaces and different number of data flows
3.2.3. Different number of nodes
In this simulation the static grid WMN was used ( Fig. 4a), but with changing number of nodes. Six different N x N grid networks were created, where N was changed from five to ten. Transmission range for each node was set to 200 meters. For traffic transmission, 15 CBR flows were used and the packet size 512 bytes was set. Data flows were created between random chosen node pairs.
Results from previous sections (3.1.1 and 3.1.2) shows that the best values for almost all QoS parameters were achieved in WMN with six radio interfaces. For this reason the simulation model for different number of nodes only for WMN with six radio interfaces was created. Figure 13 shows the average values of end-to-end delay for six radio interfaces and six different network topologies. The best value of average end-to-end delay was reached in multi-interface WMN with 25 nodes (5x5). The highest value of average end-to-end delay was achieved by WMN with 100 nodes (10x10). Results show that increasing number of nodes increase value of end to end delay.

Average values of end-to-end delay for different number of nodes
The lowest value of average throughput ( Fig. 14) was achieved in WMN with 100 static nodes. The best values of throughput were reached in configuration 6x6 and 7x7 nodes.

Average values of network throughput for different number of nodes
The highest values of packet loss ( Fig. 15) were achieved in WMN with 10x10 nodes. The lowest value of packet loss was achieved in the WMN with 6x6 nodes.

Values of packet loss for different number of nodes
As we can see from figure 16 the best value of average jitter was achieved WMN with 25 nodes and the highest value was reached in 9x9 grid network.

Average values of jitter for different number of nodes
These simulations showed unacceptable values for almost all simulated QoS parameters. Average delay combined with average jitter achieved in all networks (from 25 to 100 nodes) doesn’t allow using several CBR services running simultaneously. This conclusion is certified by enormous packet loss in networks (over 55 % in the best solution).
3.3. Results summary
The results show the benefits of using multiple radio interfaces per node. This solution can improve the capacity of WMN. Simulation results show that by increasing the number of interfaces it is possible to increase network capacity by enhancing of QoS parameters. For all simulations of WMN with common channel assignment method, the number of six radio interfaces appears as an optimum solution, because further increasing of the number of interfaces improved the capacity of WMN only slightly and using more than seven radio interfaces decreased the network performance. These results can be used as a base to another research channel assignment methods, where using of suitable CA algorithm can additionally improve network performance.
4. Theoretical background
Optimal channel assignment in WMNs is an NP-hard problem (similar to the graph coloring problem). For this reason, before we present the channel assignment problem in WMNs, let us first provide some mathematical background about graph coloring problem.
4.1. Graph coloring
The graph coloring theory is used as a base for the theoretical modeling of channel assignment problem. At the beginning we must define two related terms: communication range and interference range . Communication range is the range in which a reliable communication between two nodes is possible. The interference range is the range in which transmission from one node can affect the transmission from other nodes on the same or partially overlapping channels. The interference range is always larger than the communication range ( Fig. 17) ( Prodan & Mirchandani, 2009 ).

Communication range and interference range
Consider an undirected graph G(V, E) that models the communication network. A graph G, is defined as a set of vertices V and a set of edges E. Each vertex in graph represents a mesh router and each edge between two vertices represents a wireless link between two mesh routers. The color of each vertex represents a non-overlapping channel and the goal of the channel assignment is to cover all vertices with the minimum number of colors such that no two adjacent vertices use the same channel (Husnain Mansoor Ali et al., 2009).
4.2. Connectivity graph
The vertices set V consists of the network nodes, which may have multiple radio interfaces (not necessarily the same), while the edges/links set E includes all the communication links in the network. A link e between a pair of nodes (v i , v j ) ; where v i , v j є V exists if they are within the communication range of each other and are using the same channel. The graph G described above is called the Connectivity graph ( Fig. 5) . The links presented in the network topology are referred to as the logical links ( Husnain Mansoor Ali et al., 2009 ).
4.3. Interfering edges
To include the interference in network model, we introduce the concept of Interfering edges. Interfering edges for an edge e (IE( e )) are defined as the set of all edges which are using the same channel as edge e but cannot use it simultaneously in active state together with edge e . All edges are competing for the same channel hence the goal of channel assignment algorithm is to minimize the number of all edges e thereby increasing capacity (Husnain Mansoor Ali et al., 2009).
4.4. Conflict graph
In this subsection the concept of conflict graph is introduced. A conflict graph G c ( V c , E c ) consist of the set of edges E c and the set of vertices V c . The vortices V c have a one relation with the set of edges E c of the connectivity graph (i.e. for each edge e ∈ E c , there exists a v c ∈ V c ). As for the set E c of the conflict graph, there exists an edge between two conflict graph vertices v ci and v cj if and only if the corresponding edges e i and e j of the connectivity graph, are in IE( e ) set of each other. Hence, if two edges interfere in the connectivity graph, then there is an edge between them in the conflict graph. The conflict graph can now be used to represent any interference model. For instance, we can say that two edges interfere if they use the same wireless channel and they are within interference range. If we want use any other interference model based on signal power, then that can also be easily created by just defining the conditions of interference. Total interference can now be described as the number of links in the conflict graph (i.e. the cardinality of E c ).
The above mentioned concepts of connectivity graph, interfering edges and conflict graph are illustrated in Fig.18 . For a graph G ( V, E ), we find the IE for all the links and then create the conflict graph G c ( V c , E c ) ( Husnain Mansoor Ali et al., 2009 ).

Connectivity graph, interfering edges and conflict graph
5. Channel assignment algorithms for WMN
As has been already mentioned, CA in a multi-interface WMN consists of assigning channels to the radio interfaces in order to achieve efficient channel utilization for minimizing interference and to guarantee an adequate level of connectivity. Nowadays, there exist many approaches to solve the channel assignment problem. These approaches can be divided into three main categories ( Conti et al., 2007 ):
Fixed (static) channel assignment approaches – channels are statically assigned to different radio interfaces. The main concern includes the enhancement of efficiency and guaranteeing of the network connectivity.
Dynamic channel assignment approaches – a radio interfaces are allowed to operate on multiple channels, implying that a radio interfaces can be switched from one channel to another one. This switching depends on channel conditions, such as the value of interference. The basic issues are the switching delay and the switching synchronization.
Hybrid channel assignment approaches – in this approach the radio interfaces are divided into two groups, the first is fixed for certain channels and the second is switchable dynamically while deploying the channels.
In this section several channel assignment approaches are compared by QoS parameters mentioned in the previous section.
5.1. Common channel assignment
The Common channel assignment (CCA) is a simplest fixed channel assignment approach ( Adya et al., 2004 ). In this CA approach all radio interfaces of each node were tuned to the same set of channels. For example, if every node has two radio interfaces then each node uses the same two channels ( Fig. 19) . The main benefit of this approach is the network connectivity. The connectivity is the same as that of a single interface approach, while the using of multiple radio interfaces can improve network throughput. However, if the number of non-overlapping channel is much higher than the number of radio interfaces, the gain of the CCA may be limited. CCA scheme presents a simplest channel assignment approach but it fails to account for the various factors affecting CA in a WMN. This solution will decrease the utilization of network resources ( Yulong Chen et al., 2010 ).

Example of common channel assignment approach
5.2. Load aware channel assignment
Load aware channel assignment (LACA) represents a dynamic centralized channel assignment and routing algorithm, where traffic is mainly directed toward gateway nodes ( Raniwala et al., 2004 ), assuming that the offered traffic load on each virtual link is known. Algorithm assigns channels by such a way to ensure the network connectivity while takes into account the bandwidth limitation of each link. At the beginning, LACA estimates the total expected load on each virtual link based on the load imposed by each traffic flow. In the next step CA algorithm visits each virtual link in decreasing order of expected traffic load and greedily assigns it a channel. The algorithm starts with an initial estimation of the expected traffic load and iterates over channel assignment and routing until the bandwidth allocated on each virtual link matches its expected load. While this CA approach presents a method for CA that incorporates connectivity and flow patterns, the CA scheme on links may cause a “ ripple effect ”, whereby already assigned links have to be revisited, thus increasing the time complexity of the scheme.
An example of node revisiting is illustrated in Fig. 20 . In this example each node has two radio interfaces. The channel list of node A is [1, 6] and channel list of node B is [2, 7]. Because nodes A and B have no common channel, a channel re-assignment is required. Link between nodes A and B needs to be assigned one of the channels from [1, 2, 6, 7]. Based on the channel expected loads, link between nodes A and B is assigned channel 6, and channel 7 assigned already to link between nodes B and D is reassigned to channel 6 ( Raniwala et al., 2004 , Yulong Chen et al., 2010 ).

An example of channel revisit in LACA approach
5.3. First random channel assignment
The First Random Channel Assignment algorithm (FRCA) is a dynamic and centralized load aware channel assignment and routing algorithm for multi-interface multi-channel WMN ( Pollak, Wieser, 2012 ). This approach takes into account the network traffic profile. FRCA algorithm assigns radio channels to links considering their expected loads and interference effect of other links, which are in interference range and which are tuned to the same radio channel.
FRCA algorithm consists of two basic phases:
Initial phase
Optimization phase
In the first phase, algorithm estimates initial loads on all links based on the initial routes created by routing algorithm. After load estimation, FRCA randomly assigns channels to all nodes for each radio interface.
In the second phase, FRCA algorithm uses similar steps as in the first phase, but channel assignment and routing iterations are based on results from the first phase. If some of the link load is higher than link capacity, the algorithm goes back and tries to find better solution. Algorithm’s iterations end when no further improvement is possible. In optimization phase, FRCA uses greedy load-aware channel assignment algorithm similar to the one used in LACA algorithm ( Raniwala et al., 2004 ). In this algorithm virtual links are visited in decreasing order of the link expected load. To find routes between nodes, FRCA uses shortest path routing based on minimum hop count metric ( Kaabi et al., 2010 ).
5.3.1. Link load estimation
This approach is based on the concept of load criticality. The method assumes perfect load balancing across all acceptable paths between each communicating pair of nodes. Let P ( s, d ) denote the number of acceptable paths between pair of nodes ( s, d ), P l ( s, d ) is the number of acceptable paths between ( s, d ) which pass a link l . And finally, let B(s, d) be the estimated load between node pair ( s, d ). Then the expected traffic load Φ l on link l is calculated as ( Raniwala et al., 2004 ):
This equation implies that the initial expected traffic on a link is the sum of the loads from all acceptable paths, across all possible node pairs, which pass through the link. Because of the assumption of uniform multi-path routing, the load that an acceptable path between a pair of nodes is expected to carry is equal to the expected load of the pair of nodes divided by the total number of acceptable paths between them. Let us consider the logical topology as shown in Fig. 21 and assume that we have three data flows reported in table 2 .

Multi-interface and multi-channel WMN
Because we have three different communications node pairs, we have
| Source (s) | Destination (d) | γ (Mbps) |
| a | g | 0.9 |
| i | a | 1.2 |
| b | j | 0.5 |
Traffic profile with three data flows
| (source, destination) | (a, g) | (i, a) | (b, j) |
| Possible paths | a-c-g | i-e-a | b-f-j |
| a-c-d-g | i-e-d-a | b-f-i-j | |
| a-d-g | i-d-a | b-e-i-j | |
| a-d-c-g | i-d-c-a | b-e-i-f-j | |
| a-d-h-g | i-d-e-a | b-e-d-i-j | |
| a-d-i-h-g | i-d-g-c-a | ||
| a-e-d-g | i-h-d-a | ||
| a-e-i-h-g | i-h-g-c-a | ||
| P (source, destination) | P(a, g) = 8 | P(i, a) = 8 | P(b, j) = 5 |
Possible data flows between communicating nodes
In the next step we calculate P ( s, d ) for each flow. We need to determine all the possible paths between source and destination. Table 3 shows all possible paths between communication node pairs for the WMN topology in Fig. 21 . Values P ( s, d ) and the corresponding link traffic load ( Φ l ) is calculated using equation (2) . Results are shown in table 4 . Based on these calculations, we can estimate the load between each neighboring nodes. The result of calculation Φ l is the expected traffic load of link l (i.e. the amount of traffic expected to be carried over a specific link) ( Badia et al., 2009 , Conti et al., 2007 , Raniwala et al., 2004 ).
| l | P (a, g) | P (i, a) | P (b, j) | Φl (Mbps) |
| a-c | 2 | 3 | 0 | 0.675 |
| c-g | 2 | 2 | 0 | 0.525 |
| c-d | 2 | 1 | 0 | 0.375 |
| d-g | 2 | 1 | 0 | 0.375 |
| a-d | 4 | 3 | 0 | 0.9 |
| g-h | 0 | 1 | 0 | 0.15 |
| d-h | 1 | 1 | 0 | 0.2625 |
| a-e | 2 | 2 | 0 | 0.525 |
| d-e | 1 | 2 | 1 | 0.5125 |
| d-i | 1 | 3 | 1 | 0.6625 |
| h-i | 2 | 2 | 0 | 0.525 |
| e-i | 1 | 2 | 2 | 0.6125 |
| b-e | 0 | 0 | 3 | 0.3 |
| b-f | 0 | 0 | 2 | 0.2 |
| f-i | 0 | 0 | 2 | 0.2 |
| i-j | 0 | 0 | 2 | 0.2 |
| f-j | 0 | 0 | 2 | 0.2 |
The results of calculation Φ l on specific link l
5.3.2. Link capacity estimation
The link capacity (channel bandwidth available to a virtual link) is determined by the number of all virtual links in its interference range that are also assigned to the same radio channel. So when estimating the usable capacity of the virtual link, we should consider all traffic loads in its interference range. According to the channel assignment rules, the higher load a link is expected to carry, the more bandwidth it should get. On the other side, the higher loads its interfering links are expected to carry, the less bandwidth it could obtain. Thus, the link capacity should be proportional to its traffic load, and be inversely proportional to all other interfering loads. Thus, the capacity bw (i) assigned to link i can be obtained using the following equation:
where Φ i is the expected load on link i , Intf(i) is the set of all virtual links in the interference range of link i (i.e. links i and j operates on the same channel). C ch is the sustained radio channel capacity ( Badia et al., 2009 , Conti et al., 2007 , Raniwala et al., 2004 ).
5.4. Simulation results
In this section, the performance of proposed FRCA concept is evaluated and compared with CCA ( Adya et al., 2004 ), LACA ( Raniwala et al., 2004 ) and a single interface architecture by using NS-2 simulator (ns-2, 2008). Simulation model consisted of 25 static wireless mesh nodes placed in an area of 1000 x 1000 m ( Fig.4a) . The distance between nodes was set to 200 m. The capacity of all data links was fixed at 11Mbps. All nodes have the same transmission power and the same omni-directional antenna. The transmission range was set to 200 m and interference range was set to 400 m. For traffic generation, 25 CBR (Constant Bit Rate) flows with packet size 1000 bytes were used. Flows were created between randomly chosen node pairs. For simulation evaluation, the same metrics like in section 3.1 was used.
5.4.1. Different number of radio interfaces
From previous sections the conclusion about optimal number of six radio interfaces was gained. This conclusion was based on simple common channel assignment scheme CCA, which was used in simulations. With using more sophisticated channel assignment scheme it is possible to expect that the same results in QoS parameters may be reached with less number of interfaces. So the performance evaluation of chosen CA schemes was based on changing number of radio interfaces (between 2 to 8 radio interfaces for each node).
Figure 22 shows the average values of end-to-end delay for various number of radio interfaces. From results it is obvious that the highest value of delay (792.64 ms) was reached in WMN with CCA scheme. Lowest value (101.42 ms) reached WMN with FRCA algorithm for 4 radio interfaces. For CCA scheme the optimal number of radio interfaces was 6, but FRCA and LACA reached the best performance with only 4 radio interfaces. Results show that further increasing of number of radio interfaces didn’t increase the network performance, so the optimal number of radio interfaces for LACA and FRCA algorithm is 4.

Average values of end-to-end delay for various radio interfaces and different CA schemes
Figure 23 shows the average values of network throughput. The lowest value of average throughput for all radio interfaces was achieved in WMN with CCA scheme. This approach reached the best results for 6 radio interfaces. Others CA algorithms (FRCA and LACA) achieved the best performance with only 4 radio interfaces, with FRCA slightly outperformed LACA algorithm.

Average values of network throughput for various radio interfaces and different CA schemes
As we can see from figure 24 the highest value of packet loss for all number of interfaces was reached in WMN with CCA approach, with the best value reached for 6 radio interfaces (63.56 %). The best result (5.86 %) reached FRCA algorithm for 4 radio interfaces, whereas algorithm LACA with the same number of radio interfaces reached value 9.47%.
Figure 25 shows average values of average jitter. The best values of average jitter were again reached with FRCA algorithm for 4 radio interfaces (124.8 ms). CCA algorithm reached the best value for 6 radio interfaces (601.25 ms) and LACA approach for 4 radio interfaces (167. 27 ms).

Values of packet loss for various radio interfaces and different CA schemes

Average values of jitter for various radio interfaces and different CA schemes
6. Conclusion
In this chapter, the study of optimal number of radio interfaces and new channel assignment approach was presented (FRCA). The study of optimal number of radio interfaces was created for two different topologies (grid and random), different number of data flows and different number of nodes. The study was based on increasing number of radio interfaces (1 to 8) for each mesh nodes. The results show that by increasing the number of interfaces it is possible to increase network capacity by enhancing of QoS parameters. For all simulations of WMN with common channel assignment method CCA, the number of six radio interfaces appears as an optimum solution, because the further increasing of the number of interfaces improved the capacity of WMN only slightly and using more than seven radio interfaces decreased the network performance.
For further increasing of network performances more sophisticated channel assignment algorithms were used. The new channel assignment approach called First random channel assignment (FRCA) was compared with existing channel assignment algorithms (CCA, LACA). The results show that by using the suitable CA algorithm it is possible to further increase the network capacity. From all results it can be concluded that the multi interface approach with suitable CA algorithm can dramatically increase the whole network performance. In that case, if it is used the simplest CA approach (CCA), we need to assign for each node up to 6 radio interfaces to maximize network performance, but by using suitable dynamic CA algorithm (e.g. FRCA or LACA), the network performance may be maximized with only 4 radio interfaces.
Acknowledgement
This work was supported by the Slovak Scientific Grant Agency VEGA in the project No. 1/0704/12.
- 4. Chi Moon Oh; Hwa Jong Kim; Goo Yeon Lee & Choong Kyo Jeong 2008 A Study on the Optimal Number of Interfaces in Wireless Mesh Network, In International Journal of Future Generation Communication and Networking, IJFGCN 1 1 59 66 Dec. 2008
- 9. Husnain Mansoor Ali; Anthony Busson & Véronique Vèque 2009 Channel assignment algorithms: a comparison of graph based heuristics, In: Proceedings of the 4th ACM workshop on Performance monitoring and measurement of heterogeneous wireless and wired networks, 120 127 October 26-26, 2009, Tenerife, Canary Islands, Spain
- 10. ITU-T 2003 ITU-T Recommendation G.114, 2003.
- 13. ns-2 2008 The Network Simulator ns-2, http://www.isi.edu/nsnam/ns/
- 20. Wei Yahuan; Taoshen Li & Zhihui Ge 2011 A Channel Assignment Algorithm for Wireless Mesh Networks Using the Maximum Flow Approach. In: Journal of networks, 6 6 June 2011
- 21. Yulong Chen; Ning Xie; Gongbin Qian & Hui Wang 2010 Channel assignment schemes in Wireless Mesh Networks, In: Mobile Congress (GMC), 2010 Global, vol., no., 1 5 Oct. 2010
© 2012 The Author(s). Licensee IntechOpen. This chapter is distributed under the terms of the Creative Commons Attribution 3.0 License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
Continue reading from the same book
Wireless mesh networks.
Edited by Andrey Krendzel
Published: 14 August 2012
By Fawaz Bokhari and Gergely Záruba
2584 downloads
By Sangsu Jung
2260 downloads
By Thomas Olwal, Moshe Masonta, Fisseha Mekuria and K...
1604 downloads
IntechOpen Author/Editor? To get your discount, log in .
Discounts available on purchase of multiple copies. View rates
Local taxes (VAT) are calculated in later steps, if applicable.
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
What is channel allocation in computer network?
When there are more than one user who desire to access a shared network channel, an algorithm is deployed for channel allocation among the competing users. The network channel may be a single cable or optical fiber connecting multiple nodes, or a portion of the wireless spectrum. Channel allocation algorithms allocate the wired channels and bandwidths to the users, who may be base stations, access points or terminal equipment.
Channel Allocation Schemes
Channel Allocation may be done using two schemes −
Static Channel Allocation
Dynamic channel allocation.
In static channel allocation scheme, a fixed portion of the frequency channel is allotted to each user. For N competing users, the bandwidth is divided into N channels using frequency division multiplexing (FDM), and each portion is assigned to one user.
This scheme is also referred as fixed channel allocation or fixed channel assignment.
In this allocation scheme, there is no interference between the users since each user is assigned a fixed channel. However, it is not suitable in case of a large number of users with variable bandwidth requirements.
In dynamic channel allocation scheme, frequency bands are not permanently assigned to the users. Instead channels are allotted to users dynamically as needed, from a central pool. The allocation is done considering a number of parameters so that transmission interference is minimized.
This allocation scheme optimises bandwidth usage and results is faster transmissions.
Dynamic channel allocation is further divided into centralised and distributed allocation.

Related Articles
- Static Channel Allocation in computer network
- Dynamic Channel Allocation in computer network
- What is a static channel allocation in computer networks?
- What is a Dynamic channel allocation in computer networks?
- Multiplexing (Channel Sharing) In Computer Network
- What is Computer Network?
- What is Star Network Topology in Computer Network?
- What is Ring Network Topology in Computer Network?
- What is Tree Network Topology in Computer Network?
- What is Bus Network Topology in Computer Network?
- What is MultiDrop Network Topology in Computer Network?
- Assumptions for Dynamic Channel Allocation
- What is multicasting in Computer Network?
- What is Broadcasting in Computer Network?
- What is Firewall in Computer Network?
Kickstart Your Career
Get certified by completing the course
Channel Assignment Strategies in Mobile Communication Explained
Mohammad Jamiu
Engineering Contents
Read Time 🕠 - 3mins
Table of Contents ↬
What are channel assignment strategies.
Channel assignment strategies in mobile communication are used to allocate available radio channels to mobile users in a way that maximizes spectrum utilization and minimizes interference.
This is important because the radio spectrum is a limited resource, and there is a growing demand for mobile communication services.
Types of Channel Assignment Strategies
There are three main types of channel assignment strategies:
Fixed channel assignment (FCA)
Dynamic channel assignment (dca), hybrid channel assignment (hca).
In fixed channel assignment, each cell is allocated a fixed or predetermined set of channels (voice channels).
If all channels in a cell are occupied, the call from a mobile user is blocked and the user won’t receive service.
This strategy is simple to implement, but it can lead to inefficient spectrum utilization and increased interference if the traffic load is not evenly distributed across the cells.
Advantages of FCA:
- Simple to implement and manage
- Reduces co-channel interference
Disadvantages of FCA:
- Can lead to inefficient spectrum utilization
- Can lead to increased call blocking if traffic load is not evenly distributed across the cells
In dynamic channel assignment, channels are assigned to cells on demand, based on the current traffic load. i.e., there is no allocation of predetermined set of channels (voice channels).
This strategy is more efficient than FCA, but it is also more complex to implement.
Advantages of DCA:
- Improves spectrum utilization
- Reduces likelihood of blocking since all available channels are accessible to all cells
Disadvantages of DCA:
- More complex to implement and manage than FCA
- Can lead to increased call blocking if traffic load is high
HCA is a combination of FCA and DCA. In HCA, each cell is allocated a fixed set of channels, but additional channels can be dynamically assigned to cells if needed.
This strategy offers a good balance between simplicity and efficiency.
Advantages of HCA:
- Improves spectrum utilization compared to FCA
- Simpler to implement and manage than DCA
Disadvantages of HCA:
- Can be more complex to implement than FCA
- Can lead to increased co-channel interference compared to DCA
Channel Borrowing
Channel borrowing is a technique that can be used with any channel assignment strategy.
In channel borrowing, a cell can borrow a channel from a neighboring cell if all of its own channels are occupied.
This process is carried out by the Mobile Switching Center (MSC) which supervises the borrowing procedures and ensures that the borrowing of a channel does not interrupt or interfere with any of the calls in progress in the donor cell.
This technique can help to reduce call blocking and improve spectrum utilization.
Advantages of channel borrowing:
- Reduces call blocking
Disadvantages of channel borrowing:
- Can increase co-channel interference
Comparison of Channel Assignment Strategies (FCA, DCA and HCA)
| Fixed channel assignment (FCA) | Simple to implement and manage | Can lead to inefficient spectrum utilization, increased call blocking if traffic load is not evenly distributed across the cells |
| Dynamic channel assignment (DCA) | Improves spectrum utilization, reduces co-channel interference | More complex to implement and manage, can lead to increased call blocking if traffic load is high |
| Hybrid channel assignment (HCA) | Improves spectrum utilization compared to FCA, simpler to implement and manage than DCA | Can be more complex to implement than FCA, can lead to increased co-channel interference compared to DCA |
More For You ☄
- Skip to content
- Skip to search
- Skip to footer
Radio Resource Management White Paper
Bias-free language.
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Radio Resource Management
- Radio Resource Management Concepts
- RRM Data Collection Activities
- RF Grouping
- Flexible Radio Assignment (FRA) and Redundant Radios
Dynamic Channel Assignment (DCA)
- Transmit Power Control (TPC) Algorithm
- Coverage Hole Detection and Mitigation Algorithm
- RF Profiles

Chapter: Dynamic Channel Assignment (DCA)
What does dynamic channel assignment do, the dynamic channel assignment (dca) algorithm, dca sensitivity threshold, dca modes of operation, dca, the obss and constructive coexistence, flex dfs - flexible dynamic frequency selection, persistent device avoidance.
Dynamically manages channel assignments for an RF group.
Evaluates the assignments on a per AP per radio basis
Makes decisions using an RSSI based cost metric function which evaluates performance based on interference for each available channel
Dynamically adjusts the channel plan to maintain performance of individual radios
Actively manages 20/40/80/160 MHz bandwidth OBSS’s
Can dynamically determine best bandwidth for each AP (DBS v.8.1)
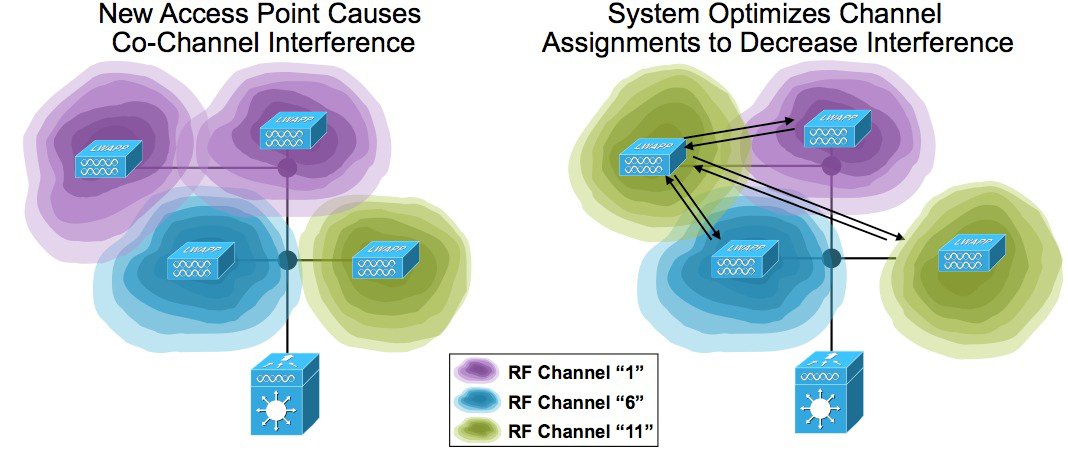
DCA's job is to monitor the available channels for the RF group and track the changing conditions. Optimizing the RF separation between AP's (minimizing co-channel interference) by selecting channels that are physically diverse which maximizes RF Efficiency. DCA monitors all available channels and develops the Cost Metric (CM) that will be used to evaluate various channel plan options. The CM is an RSSI value comprised of interference, noise, a constant (user sensitivity threshold), and load (if enabled). The Cost Metric equates to a weighted SNIR (Signal to Noise Interference Ratio). See RRM Data Collection Activities above for a complete discussion.
Competitive Note - our competitors radio management systems also must monitor off channel in order to develop information used for decisions. Cisco's RRM implementation has consistently tested as the least disruptive. Conducting throughput testing can validate this; Cisco AP's maintain fluid information flows. Competitor's products typically show distinct drops in throughput when subjected to the same test suites. Aruba by default requires a 110 ms dwell off channel. Off Channel scans are used for many things, implementation of wIDS/wIPS typically requires extensive off channel scanning, not just on DCA channels but typically on Country Channels which is a much larger list to visit. Turning off RRM, disables these off channel scans - but it also eliminates wIDS and rouge detection as well.
DCA uses all of these measurements and sums them up into an RRSI based Cost Metric that will be used in the equation. The cost function is a single numeric value expressed as RSSI that represents the overall goodness of a given channel option.
Changing the channel of an AP is potentially disruptive. Care must be taken in the evaluation of apparent improvements. This is where next generation DCA excels. Determining if an AP's performance can be improved without negatively impacting neighbors in the neighborhood is a multi-step process.
The Group Leader maintains the neighbor lists for all AP's in the RF Group, and organizes these neighbors into RF Neighborhoods. The following metrics are also tracked for each AP in the RF Group.
Same Channel Contention —other AP's/clients on the same channel - also known as Co-Channel interference or CCI
Foreign Channel - Rogue —Other non RF Group AP's operating on or overlapping with the AP's served channel
Noise —Non-Wi-Fi sources of interference such as Bluetooth, analog video, or cordless phones - see CleanAir for useful information on using CleanAir to detect noise sources
Channel Load —through the use of industry standard QBSS measurements - these metrics are gathered from the Phy layer - very similar to CAC load measurements.
DCA Sensitivity —A sensitivity threshold selectable by the user that applies hysteresis to the evaluation on channel changes
The impact of each of these factors is combined to form a single RSSI based metric known as the Cost Metric (CM). The CM then represents complex SNIR of a specific channel and is used to evaluate the throughput potential of one channel over another. The goal is to be able to select the best channel - for a given AP/Radio while minimizing interference . Using the CM, the Group Leader is able to evaluate every AP and every channel for maximum efficiency. Of course conditions change in RF, so these statistics are dynamically collected and monitored 24 hours 7 days per week.
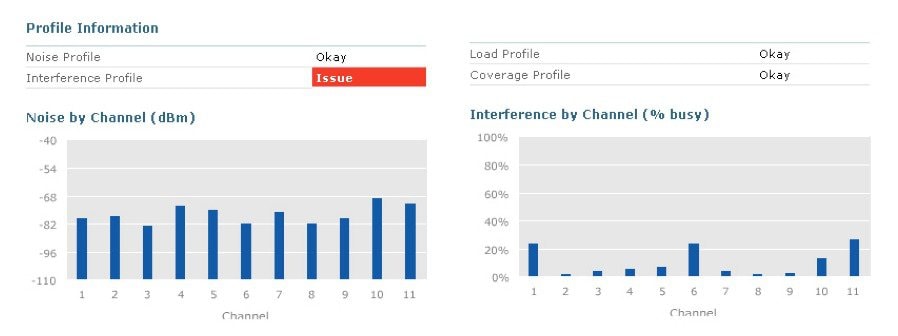
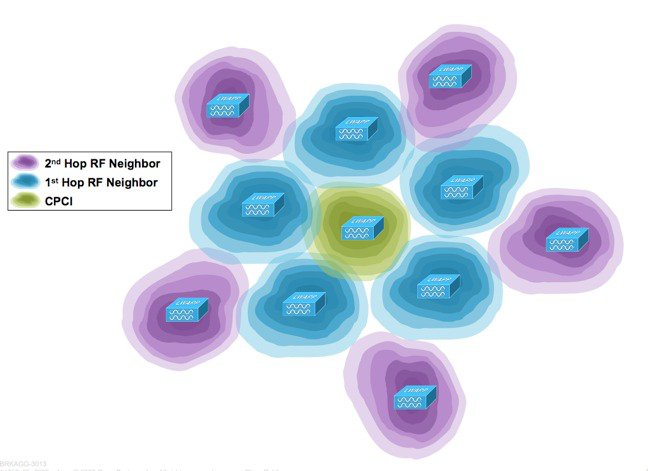
Using the CM for the currently served local channels on the AP's, the RF group leader develops a list stack ranked worst to best. This becomes the CPCI list (Channel Plan Change Initiator) which indicates which AP's are suffering the worst performance in the RF Group. For simplicity - lets take a quick look at a single AP and what DCA does - then we'll apply that concept to the more complicated job of an entire RF group with channel bonding and multiple AP capabilities.
DCA in a Nutshell
A DCA run starts with selecting a CPCI - by default, DCA will always pick the AP with the worst CM to start with, and alternate for successive iterations between a random AP and then the next worst on the remaining list. DCA takes the CPCI, along with all of it's 1st hop and 2nd hop neighbors as a group to see if a channel plan can be calculated that provides a better selection for the current CPCI.
A first hop neighbor is any AP our CPCI knows about through direct observation (neighbor relation), a second hop neighbor is an AP that is in our neighborhood and we know about because our first hop friends know them. In the evaluation, channels for the CPCI and all first hop neighbors may be changed to achieve a solution. Channels for second hop neighbors - while evaluated for impact, cannot be changed. This allows isolation of local groups of AP's and prevents the possibility of a change impacting AP's across the entire RF group.
Once the calculations are complete the result is often several possible channel plans which will improve the CPCI. Each channel plan, which yields improvement, is subjected to another gating feature known as the NCCF (normalized cumulative cost function). This non-RSSI based function evaluates the resulting channel plans for overall CPCI group goodness, in other words the CPCI must see an improved CM, but only if it's neighbors, as a group, either improve or stay the same for the channel plan to be recommended.
Once the calculation is complete, the CPCI and its first hop neighbors are removed from the CPCI list, and the next iteration begins with a random selection out of the remaining AP's on the list. The DCA process will alternate between worst and random selections until the entire CM list is empty. In this way - all AP's are evaluated in the context of every other AP that can hear them. DCA completes when the CM list is empty, NCCF is completed and channel changes are processed.
Wi-Fi is a bursty medium, meaning that things can look really bad for a short period of time, but over all be pretty good. Since changing the channel of an AP is potentially disruptive care is taken to ensure that if a change is made - it is for a non trivial performance improvement and not a knee jerk response to a short term trend. A user selectable sensitivity threshold is provided that allows dampening of the channel change algorithm. The default value is medium (10 dB), and essentially says that in order for a channel change to be made, the new channel must have a CM of 10 dB better in order for it to be recommended. The low sensitivity value is 20 dB and the medium value is 10-15 dB depending on band. NCCF will process this threshold since it has final say on a recommended channel plan. Any channel plans not meeting that criteria will not be processed at the AP.
| Band | Low | Medium | High |
|---|---|---|---|
| 2.4 GHz | 20 dB | 10 dB | 5 dB |
| 5 GHz | 20 dB | 15 dB | 5 dB |
The evaluation is simple. NCCF asks, is the Delta between current and proposed channel cost metrics equal to, greater than or less than DCA sensitivity threshold value? If equal or greater than, then the channel change is recommended. This serves to dampen temporary or short term gains and thrashing of channels in response to loads which can have a bad effect on client connectivity.
Scheduled DCA
DCA operates by default every 10 minutes (600 seconds) in steady state once it has been initialized unless some other interval is defined and DCA is running in Scheduled mode. Scheduled DCA allows customers to plan around potential disruptions associated with channel changes, however it should be noted that the DCA algorithm will only run at this selected time and may not be evaluating the users environment at peak loads. The same environment when loaded with clients could be significantly different. To increase the effectiveness it is recommended that customers select the highest sensitivity level which will maximize the changes made during off peak hours. It's also a good idea to periodically re-evaluate the environment for its tolerance to channel changes. As clients are refreshed this will improve and most modern clients do just fine managing a channel change.
Start-up Mode
Any time that a controller in the RF Group enters or departs the RF group (a reboot for instance) Start-up mode is assumed. This means that if the controller was the RF Group Leader and it returns as the RF Group leader then DCA will run startup mode - regardless of the user settings- every 10 minutes for the next 100 minutes. Now, obviously this is something that should be considered before rebooting a controller, however it's not as bad as it may seem. If the network was previously at steady state, then the AP's channel assignments should already be optimized. If the controller is a new addition, and you've added AP's then DCA will need to run to optimize the new channel assignments required. Plan accordingly.
Start up mode is aggressive and ignores NCCF and the user sensitivity threshold. It will produce a channel plan that maximizes the RF Distance between AP's without regard to the dampening mechanisms designed to slow the rate of change in a live network.
Since version 7.3 of code, there is a command line argument for initializing DCA startup mode. It is present on all controllers in an RF Group - but will only affect the DCA mode of the controller whom is the RF Group Leader. Running the command config 802.11a/b channel global restart from the command line of the Group leader will re-initialize RRM's DCA and provide an optimal answer based on measured values over the air.

Steady State Mode
DCA runs by default every 10 minutes. If the user schedules DCA with an Anchor time and interval - DCA runs on the scheduled intervals. Cisco recommends a minimum of 2 intervals per day - even though it is possible to run only 1. See Scheduled DCA above for additional considerations.
Over time, and especially with changes in the network architecture the user sensitivity threshold (dampening) can lead to sub optimal channel assignments. Most network architectures change over time, and DCA's rules assume a steady state network. If AP's have been added or removed, or channel bandwidths have been changed network wide, it's very possible that you could have AP's that could see a 9 dB improvement in the cost metric, but because the hysteresis is 10 dB (default) a change is not made.
When making changes to the architecture it is a best practice to restart the DCA algorithm by placing it into Startup Mode which suspends all user settings (the sensitivity threshold) and the NCCF functions and permits an aggressive channel search for a good baseline on the new architecture.
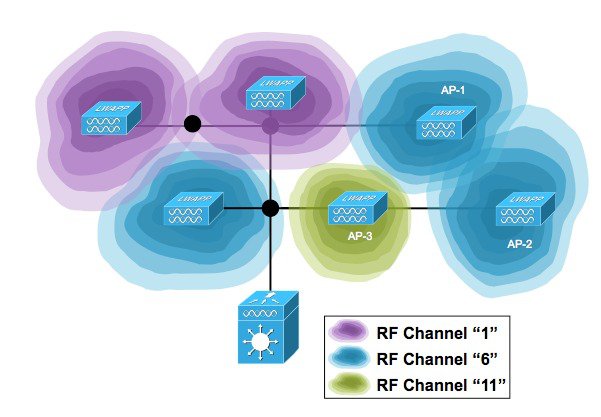
Using Figure 12 above, lets suppose that AP-1 is on channel 6 and has the worst CM for the group at -60 dBm (Remember, less is more. The lower the CM the lower the noise floor and the better the throughput).
DCA Evaluates Channels 1 and 11 for AP-1’s location and determines that the CM could be -80 dBm on channel 11
This represents a potential Δ(CM) = 20 dB if we change channel 6 to channel 11 for AP-1
DCA would change the channel if sensitivity set to High or Medium or Low (5,15,20) are all = to or < 20).
If the CM for Channel 11 where -75, then the delta would be 15 dBm and a change would only be made if the sensitivity threshold where High or Medium (5 or 15 dBm) but not low as 15 dB does not meet the 20 dB hysteresis.
Additionally, if the new channel plan results in neighbor changes and the neighbors CM will be driven lower – NCCF will NOT Recommend the channel plan for implementation
Without diving heavily into the math, NCCF provides a normalization of the CM data for the CPCI and it's first hop neighbors and prevents making a channel change if the CPCI would negatively impact it's neighbors. Think of NCCF as an overall "goodness" rating of the change for the group. This breaks down like this.
NCCF is applied as such to each radio being affected by the recommended change (CPCI and it's 1st and 2nd hop neighbors)
+1 - if CM improves by +5 dBm or better
0 - If CM =/- 4 dBm
-1 - If CM worsens by 5 dBm or better
If NCCF evaluates the recommended change as being beneficial for the CPCI and it's neighbors then the change is implemented.
DCA 20, 40, 80, and 160 MHz support
Keeping in mind that everything that is evaluated by RRM is based on actual over the air observations. How then does RRM handle coexistence and the challenges of 20/40/80/160 MHz OBSS channel selections. What if we are deploying a mixture of 802.11a/n/ac (or perhaps we have 802.11a radios as neighbors) how does RRM's DCA address this? Things have become complicated for sure, but the goal of DCA is always to create a channel plan that favors constructive coexistence. Constructive coexistence doesn't mean we can eliminate the other radios in the air, they are usually there and have a legal right to be, but rather make a decision that reinforces a complementary plan and supports everyone's contention needs and provides equal - shared - access to the medium.
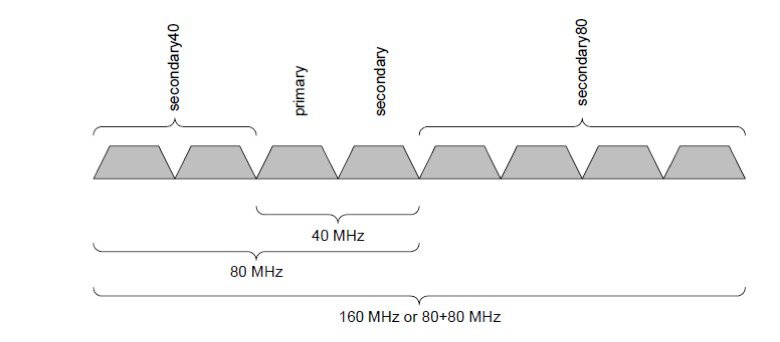
The OBSS or Overlapping BSS became a reality with the introduction of 802.11n and continues with 802.11ac. Both of these protocols allow for dynamically linking multiple 20 MHz channels together to form a wider channel in which more data can be transmitted simultaneously. Channel positions within the bonded channel are important, as not all channels behave the same.
| Abbreviation | Proper Name | Function and Notes |
|---|---|---|
| P20 | Primary Channel | All management and signaling frames, HT and VHT headers are on the P20 only |
| S20 | Secondary 20 | added to the primary for additional capacity to form a 40 MHz channel - may be +/- of the primary channel position |
| S40 | Secondary 40 | Added to an P20 and S20 to make an 80 MHz channel. Bonded channels must in the same band ( Unii 1,2,2e,3 ) |
| S80 | Secondary 80 | Added to an P20 and S20 to make an 80 MHz channel. Bonded channels must in the same band ( Unii 1,2,2e,3 ) |
For the purposes of this discussion we will focus on 5 GHz. It is legal to have an 802.11n BSS use a 40 MHz channel in 2.4 GHz, however Cisco does not support this. There are simply not enough channels in 2.4 GHz spectrum for this to be effective. 802.11ac - ONLY operates in 5 GHz spectrum.
802.11a clients do not understand 802.11n HT headers, and both 802.11a and 802.11n don't understand 802.11ac's VHT header. In order to maintain backward compatibility and satisfy all three protocols requirements - all 3 share the primary channel architecture and definition as a common signaling channel using the 802.11a protocol. Both 802.11n and 802.11ac add an additional headers (HT and VHT) to the standard 802.11a frame format used to advise 802.11n and 802.11ac clients on specifics such as channels and selected bandwidth as well as supported data rates for each protocol. All management (broadcast) traffic will use the 802.11a protocol on the primary channel. To an 802.11a device - it's all 802.11a.
Wi-Fi is contention based. Each station listens to the channel to determine when it is quiet (listen before talk or LBT). However, not all 20 MHz segments are treated equally in within a bonded channel. Secondary channels have less contention to ensure that when the primary channel is clear, the secondary(s) have a higher probability of also being clear. For this reason it is important to understand the impact this can have in a design where multiple protocols are being supported (at a minimum today you will have 802.11n and 802.11ac AP’s present either as infrastructure or rogue neighbors).
In the table below, CCA thresholds example, the RSSI values are the thresholds at which the receiver must listen to determine if the channel is busy or idle. CCA assessment is done by segment, and the first not clear segment suspends checking the rest of the channel segments and reports not clear to the host. Energy at or above the threshold indicates a carrier busy or not clear - and no TX will happen. Any energy falling below the threshold, represents a distant station and we consider the channel idle and we can clear the next segment or transmit if all are completed.
Note that all three protocols share the same value for the primary channel - this makes them equal with regards to contention -they will all get fair access to the medium. You can also see that the values for the Secondary 20, and all other secondary's are more generous (in that the threshold is higher representing less contention - and with a higher probability of winning contention than a station that is listening at a lower value.
|
| ||||
| Protocol | P20 | S20 | S40 | S80 |
| 802.11a | -82 | — | — | — |
| 802.11n | -82 | -62 | — | — |
| 802.11ac | -82 | -72 | -76/-79 | -76/-79 |
DCA's job is to provide a channel plan accounting for the variables, as they exist, in the air around each individual AP. Critical to this is the overall number of available channels, and that changes based on both the regulatory of the equipment and the channel width selected. An 80 MHz channel is 4x20 MHz channels so depending on your regulatory; you can chew through channels pretty quickly and leave yourself without enough spectrum to build an efficient network. We also have to make these decisions in a way that promotes and supports a constructive coexistence between different specifications or someone will go wanting.
For instance, referencing the table above for CCA thresholds, If I place an 802.11n 40 MHz P20 channel on an 802.11ac (or 802.11n for that matter) S20 channel, I am forcing the 802.11n AP to compete for airtime against a stacked deck - since the 802.11n AP will need to wait until the channel is quiet at -82 dBm to win contention - while the 802.11ac AP only has to clear the same channel down to -72 dBm. This sets up a very unfair match in which the 802.11ac AP can starve the 802.11n AP for access - simply because every time they both need the channel - the 802.11ac AP will likely win. This assumes that the two AP's are close enough to hear one another at the affected range say -74 dBm (there will be plenty of these close enough in a moderately dense network).
The graphic below shows two RF Coverage plots made using average device (client) power of 10 dBm. The AP listening at -82 dBm (CCA for a P20), is in contention with every station within the -82 dBm plot area. The coverage area for -76 dBm (CCA for an S20 channel) is much smaller - and represents a lot less stations to compete with.
DCA's algorithms are looking for 3 possible solutions to work out compromises, each for both our AP's and neighbors or rogues. In order of preference, if there are no free channels available DCA
Primary channels aligned = P20 to P20 = BEST
Primary Channel aligned Secondary 40 or 80 = P20 to S40/S80 = OK
Primary Channel aligned with Secondary 20 = P20 to S20 = Better than nothing
After that, DCA runs as normal - seeking to resolve the channel plan with the given mix of radios. Assignments with someone's 20 MHz channel as a secondary channel are given a higher cost metric to lessen the likelihood of their selection as a valid assignment for any radio in the domain.
In RRM, you may select either 20/40/80 MHz channels from the DCA dialogue, however if the radio is an 802.11a Radio, it can only support a 20 MHz channel - and that is all it will receive. Likewise for 802.11n radios, if you select 80 MHz - they will be assigned a 40 MHz channel.
Is there any benefit to running the 802.11n or 802.11ac protocol even if you choose to not support 40 or 80 MHz channels? Certainly, Higher Data Rates, better multipath immunity, and Client Link are three examples of big benefits that can be enjoyed by legacy as well as 802.11n/ac clients. There is all upside and no downside to implementing 802.11n or ac regardless of the clients operating on the infrastructure - that's pretty rare in networking.
Dynamic Bandwidth Selection–DBS
The DBS feature was introduced in version 8.0 of the code and represents a flexible and intelligent way to allow RRM to assign bandwidth to AP's that have clients associated that can benefit from the additional bandwidth. This approach is dynamic, and since it is based on analysis of what the client capabilities are as well as what they are doing allows RRM to Right Size the network channels.
As previously discussed, the advantage to having a wider channel is obvious - more data with each transmission. However, this only holds true if we can balance this against contention needs and spectrum availability. Moving more data with every transmission is not better if I have to wait 3 times as long to send a single packet - the result could be worse than sending what I have more frequently, in smaller bits. Not all applications actually benefit from bonded channels; Voice for instance relies on small packets that are time sensitive (jitter). Video however benefits greatly - but still has a sensitivity to Jitter in some cases (real time video). Neither are the channels within the bonded channel equal in function. The Primary channel is the only one that will be transmitting signaling information where the other bonded channels will simply send payload associated with a packet defined on the signaling channel. Secondaries are less loaded than the primary's as a rule.
The Best Practice for most organizations today is to use no more than 40 MHz in enterprise deployments. However it really comes down to how many channels you have and how close your AP's are to one another. For this reason DBS relies on the tremendous amount of information available within RRM to dynamically adjust the channel width in conjunction with it's other duties.
DBS will evaluate:
Associated client capabilities and types
RF Neighbor Channel Widths
OBSS channel Overlap ratios
Channel Utilization
Non Wi-Fi Noise
Wi-Fi interference
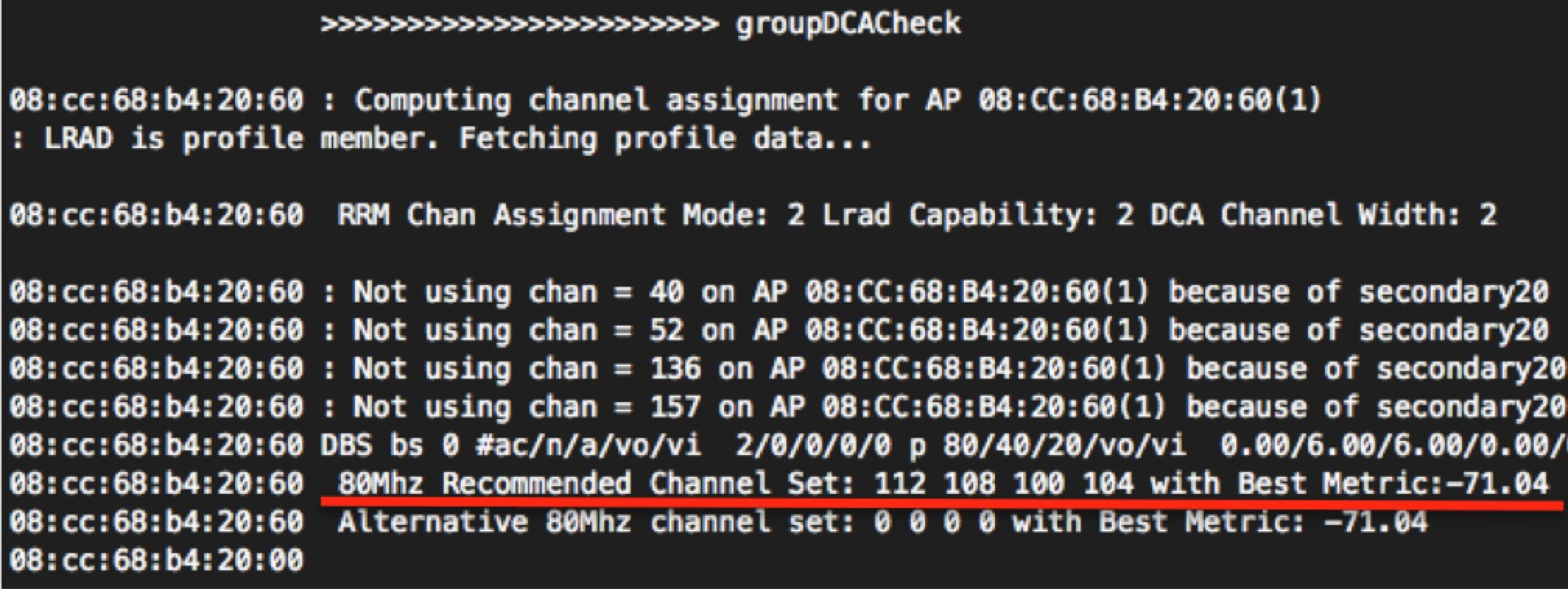
In the graphic above (output from debug airwave-director channel enable) note the DBS bs line ac/n/a/vo/vi = 802.11ac/802.11n/802.11a/voice/video 2 /0/0/0 /0 = 2 associated 802.11ac clients, no 802.11n, no 802.11a, no voice and no video.
Following this count we have the bias score –the bias is added to the cost metric for a particular bandwidth, more bias = less likely to choose.
P 80/40/20/vo/vi = 80 MHz/40 MHz/20 MHz/voice/video 0/6 /6 /0 /0 = no bias – against 80 MHz, bias against 40 and 20 MHz, no Bias for voice or video – this is RRM for – recommending an 80 MHz channel – because the only clients are 802.11ac capable. Does this mean I will get an 80 MHz channel–NO. However the likelihood is increased and we will have to weigh it against the other factors within the environment.
Looking at the whole network, a small one to be sure – the same debug and it’s recommendations for each radio look like extracted output as shown.
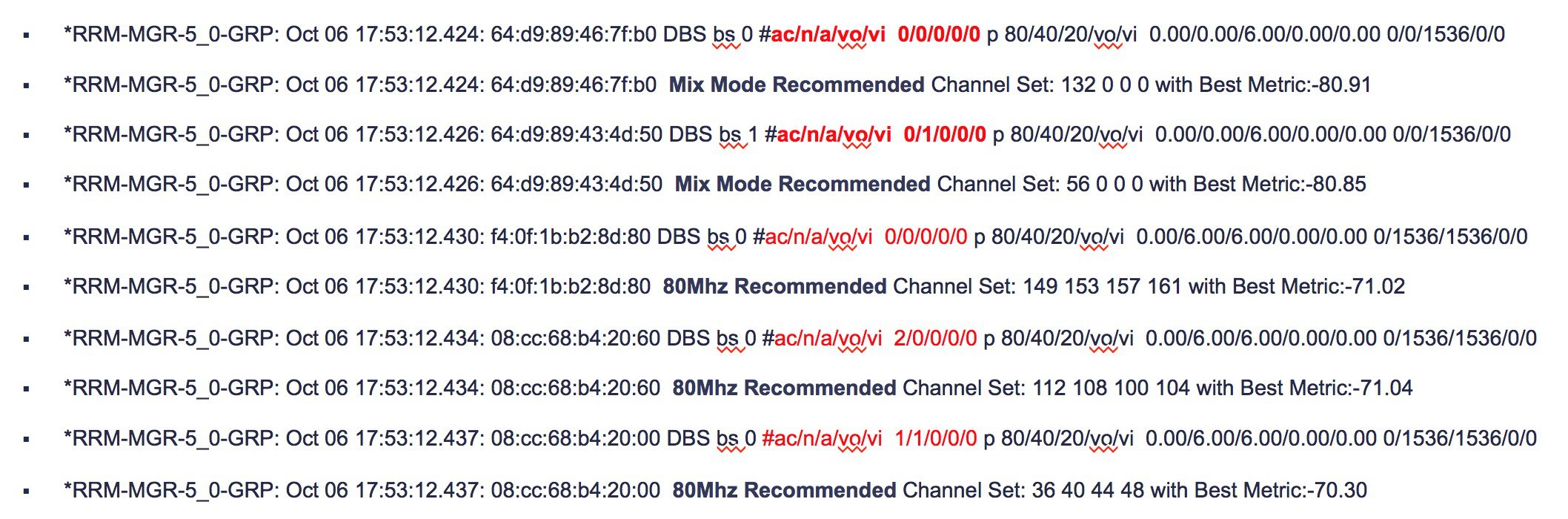
Other AP's in the configuration example above either have NO 802.11ac clients - or are split between a single 802.11ac and an 802.11n client. Bandwidth is set accordingly for the channels and AP's that are in use. Arguably - this is a simple configuration and things get more complex at scale - however the logic which is being used is good logic. It matches best practice recommendations that are based on - how many of what type of client are you supporting? If you set 80 MHz channels for everything, when most of your clients are still 802.11n then you are wasting a lot of bandwidth that 802.11n clients can not use. In fact - it is optional for 802.11n clients to support a bonded channel and most smartphones do not, this is something more commonly supported on laptops and upper end tablets only.
In practice, the main objection to this feature has been - "but I want an 80 MHz channel, and it wont give it to me here…..". You can still override this feature and set a manual bandwidth on the AP, however be warned that RRM didn't think it was a good idea, it is usually pretty right on these things.
With the inclusion of DBS, another challenge that is observed in the modern OBSS world is resolved as well. If the channel definition is 80 Mhz, comprised of 4x 20 MHz segments and we are using UNII 2 channels (DFS) then if a radar is detected on any of the 4 20 MHz segments forces abandonment of the entire channel by the AP and the users. Without DBS and Flex DFS this equates to an 80 MHz chunk of spectrum which is marked as unusable for 30 minutes. With DBS and Flex DFS - we simply mark the affected 20 MHz channel - and reconfigure the AP accordingly to use either the remaining 40 MHz channel or the 20 MHz channel, either way - the AP and clients no longer have to switch gears - the AP does not have to find space that is less optimal for it's position- and you only loose 20 MHz - not 80 MHz of spectrum.
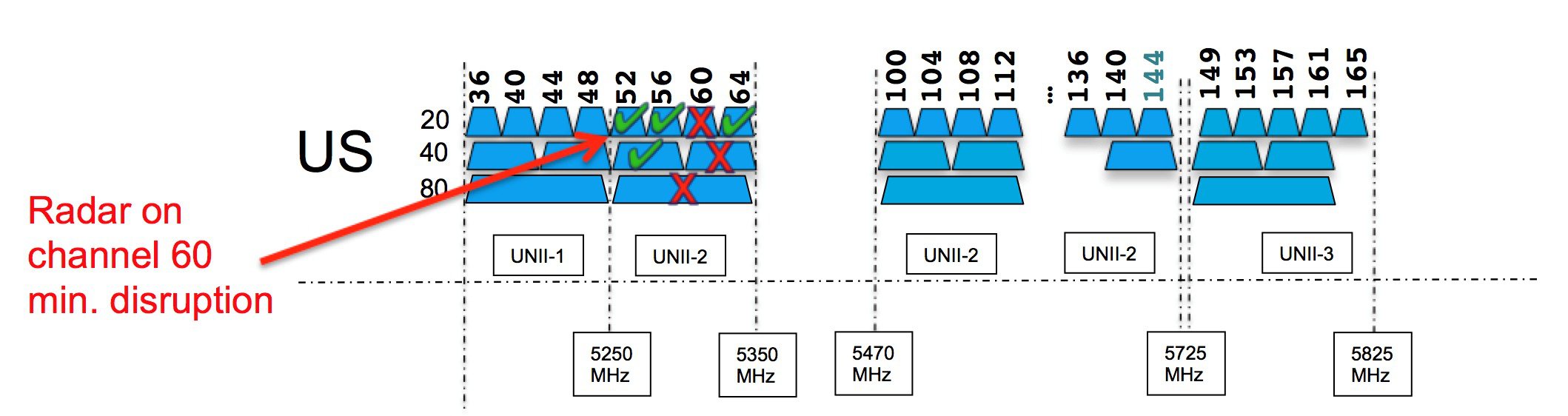
This seems like a simple thing - and it makes sense. However if I have told the system to only assign 80 MHz channels - this is what it will look to do. With DBS and Flex DFS we give the system the ability to do what makes the best sense while maintaining compliance.
Device Aware RRM
CleanAir shares information with RRM that normal Wi-Fi radios do not have access too at the physical layer. Non-Wi-Fi radio interference (known as noise to Wi-Fi) is actionable information for RRM in some instances. For instance, a Microwave oven, most offices have at least one - and it represents a significant source of noise for Wi-Fi. Thee are two CleanAir features that interact with RRM in different ways; we will discuss those here.
Persistent device avoidance identifies sources of Wi-Fi interference, which are frequently present within installations and some which are not. If present, these devices represent a factor, which, while perhaps not constant, will negatively impact any channel that they interfere with and as a result, should be avoided. RRM's normal data collection and action cycle will be aware of the interference and will avoid it. However, once the source goes quiet, the channel that was avoided will likely look good to RRM again and in that case RRM will likely re-assign the radio to the previously bad channel. Microwave Ovens, Outdoor Ethernet bridges are two classes of devices that qualify as persistent, since once detected, it is likely that these devices will continue to be a random problem and are not likely to move. For these types of devices we can tell RRM of the detection and Bias the affected channel so that RRM "remembers" that there is a high potential for client impacting interference for the Detecting AP on the detected channel.
Lets use a Microwave oven as an example. Most workplaces have at least one, and some have many. While in operation an MWO will impact the 2.4 GHz band with high duty cycle noise. MWO's operate anywhere from 700-1200 watts for consumer units, and can range higher for commercial grade units. MWO's are shielded to avoid harmful radiation leakage, but the concern here is for the humans, not the Wi-Fi and operating at a fraction of a watt, there is enough energy left over to seriously impact communications. MWO's operate anywhere within the 2.4 GHz spectrum, generally at the higher end (channel 11) but frequently impacting channel's 11,6 or even the entire band.
MWO's do not run continuously, generally first thing in the morning - on and off for a couple of hours around lunch - then again for the afternoon popcorn. Persistent Device Avoidance allows us to Mark and AP and it's detection channel so that RRM knows the device exists. PDA registers the interference, and then starts a countdown timer which refreshes with each new detection. If at the end of 7 days, no more detections where processed, the bias is removed and the PDA detection is reset.
Biasing an affected AP/Channel does not guarantee that RRM will not use that channel for that AP, but it decreases the likelihood by increasing the cost metric. The end result is up to DCA as even with the cost metric bias, this could still be the best channel available.
You can view an AP's PDA status on the controller under Wireless>802.11b/g/n (or 802.11a/n/ac)>details, at the bottom of the Details page is the current PDA devices being tracked with their last detection date.
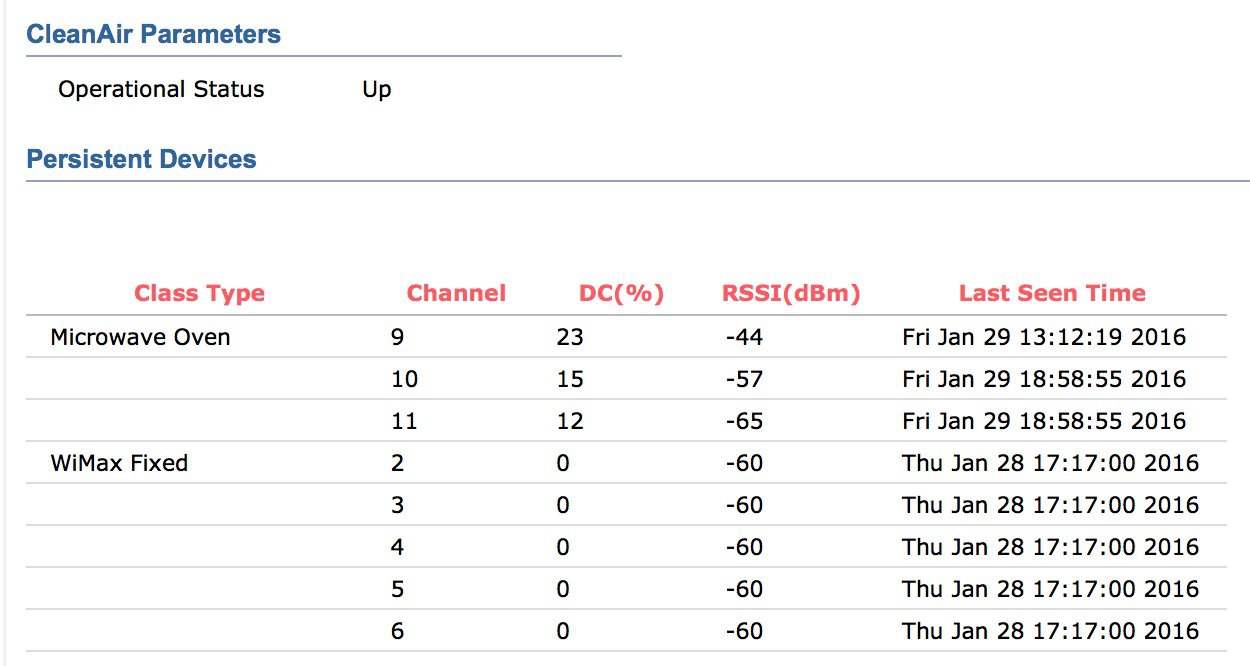
CleanAir PDA devices include:
Microwave Oven
WiMax Fixed
WiMax Mobile
Motorola Canopy
PDA is based on an actual device classification - so we know that this device exists, and we know which AP's could hear it at a level that was impacting. This allows RRM to work around these devices to come up with an alternate channel plan that works around the affected channels for the areas where there is an issue. PDA only affects the AP that detected the device.

This feature was created as a stopgap for customers use while implementing CleanAir AP's, it should not be used as part of a plan to mix some CleanAir AP's in with existing non-CleanAir AP's unless you are deeply familiar with CleanAir behaviors and understand the risks.
Channel Change traps related to PDA will have "Device Aware" as the reason code.
ED-RRM is not directly related to RRM, but will cause channel changes if invoked. ED-RRM stands for Event Driven-RRM and is intended to quickly resolve catastrophic interference events. Because Wi-Fi is Listen Before Talk (LBT) If there is energy on the channel above the CCA threshold - all stations will hold off using the channel until it has cleared. Certain non-Wi-Fi devices are classified as continuous, meaning 100% or near 100% duty cycle, in short they never turn off. An analogue video camera is an example of such a device. If this device is present, neither the AP or it's clients that hear it will ever attempt to transmit, since the energy is always present. This would be corrected by normal RRM DCA activities, however correction could take up to 10 minutes (DCA interval) or more if DCA timing has been changed.
CleanAir at the AP allows us to recognize such a device, and positively classify it as such a device (can not be confused with normal Wi-Fi Oversaturation). This is a distinct advantage, since we know for certain if this device exists, it will not yield the channel or get better on it's own unless disabled. We can however detect this very quickly at the AP interface, and allow the AP to make a temporary channel change to quickly avoid this energy and restore service. Following that change a normal DCA cycle will find a better permanent home for the AP that avoids the now unusable channel in that location.
ED-RRM is based entirely on the Air Quality metric on the AP. Air Quality or AQ for short is entirely comprised of CleanAir classified non-Wi-Fi interference metrics, so can not be driven by unclassified or normal Wi-Fi related noise. Simply relying on noise for this would be very bad since Wi-Fi noise can have very high short duration peaks followed by relative calm - this is quite normal. However relying on the AQ metric avoids all of this since we know for certain that it is a problem that is not just going to go away.
In version 8.0 a new component was included in ED-RRM functionality. Rogue Contribution, which allows ED-RRM to trigger based on identified Rogue Channel Utilization, which is completely separate from CleanAir metrics. Rogue Duty Cycle comes from normal off channel RRM metrics, and allows us to invoke a channel change based on neighboring rogue interference as well. Because this comes from RRM metrics and not CleanAir, the timing - assuming normal 180 second off channel intervals - would be within 3 minutes or 180 seconds worst case. It is configured separately from CleanAir ED-RRM and is disabled by default. This allows the AP to become reactive to Wi-Fi interference that is not coming from our own network and is measured at each individual AP. Other than the source trigger, Rogue Contribution in ED-RRM follows the same rules as CleanAir contribution.
The AP calculates AQ on a 15 second rolling window, and any two consecutive AP level AQ threshold violations will trigger ED-RRM is configured (disabled by default). It also has the following protections:
Once triggered, the AP is desensitized for ED-RRM for 60 seconds on the new channel – to prevent immediate flapping
Once a channel has been identified with an ED-RRM trigger event – that channel is locked out for 60 minutes.
Using 2.4 GHz as an example, lets say that we trigger an ED-RRM channel change on Channel 1 and switch to channel 6. Lets assume that the interference covers the entire 2.4 GHz band, and we trigger again on channel 6 after a 60 second rest and move to channel 11. In our scenario channel 11 is also affected and so also triggers an ED-RRM alert in 60 seconds. At this point - there are no other channels to move too, since both channel 1 and 6 are now in a 60 minute lock out. The AP would continue to sit on channel 11 until such time that either the 60 minute timers are cleared - or the interference is disabled/corrected. This prevents flapping or a runaway condition.
Configuring ED-RRM is done through the Wireless>802.11a/b>DCA configuration dialogue .
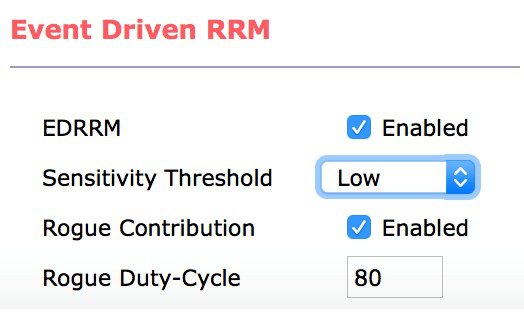
Configuration consists of enabling ED-RRM (disabled by default) and selecting the AQ threshold level:
Low sensitivity = AQ at 35%
Medium sensitivity = AQ at 50%
High sensitivity = AQ at 60%
Custom = custom - but be very careful here
Remember that AQ is a scale which shows the collective impact of all CleanAir classified Interferers, a good AQ is 100% and a very bad one is 0%.
To enable and use Rogue Contribution, ED-RRM must be enabled first, then enable Rogue Contribution, Rogue Duty cycle is just that - the default is 80 which means if Rogue devices are using 80% of the channels capacity, you should leave and find a better channel.
While neither of these triggers and responses are driven by DCA, they will be honored by DCA and channel changes to re-balance the surrounding AP's will likely happen after a trigger event. Channel Change traps resulting from ED-RRM triggers will include "Major AQ event" for the reason code.
Was this Document Helpful?

Contact Cisco
- (Requires a Cisco Service Contract )
Channel Assignment Techniques
Cite this chapter.

- Gordon L. Stüber 2
280 Accesses
First generation macrocellular systems typically use fixed channel assignment (FCA), where disjoint subsets of the available channels are permanently allocated to the cells in advance according to their estimated traffic loads. The cells are arranged in tessellating reuse clusters whose size is determined by the co-channel reuse constraint. For example, the North American AMPS system typically uses a 7-cell reuse cluster with 120° sectoring. The 12.5 MHz bandwidth allocation for AMPS can support a total of 416 two-way channels, 21 of which are control channels (one for each sector in a cluster), leaving a total of 395 traffic channels. This yields an allocation of 56 channels/cell with uniform FCA.
This is a preview of subscription content, log in via an institution to check access.
Access this chapter
Subscribe and save.
- Get 10 units per month
- Download Article/Chapter or Ebook
- 1 Unit = 1 Article or 1 Chapter
- Cancel anytime
- Available as PDF
- Read on any device
- Instant download
- Own it forever
Tax calculation will be finalised at checkout
Purchases are for personal use only
Institutional subscriptions
Unable to display preview. Download preview PDF.
Author information
Authors and affiliations.
Georgia Institute of Technology, USA
Gordon L. Stüber
You can also search for this author in PubMed Google Scholar
Rights and permissions
Reprints and permissions
Copyright information
© 1996 Springer Science+Business Media New York
About this chapter
Stüber, G.L. (1996). Channel Assignment Techniques. In: Principles of Mobile Communication. Springer, Boston, MA. https://doi.org/10.1007/978-1-4757-6268-6_11
Download citation
DOI : https://doi.org/10.1007/978-1-4757-6268-6_11
Publisher Name : Springer, Boston, MA
Print ISBN : 978-1-4757-6270-9
Online ISBN : 978-1-4757-6268-6
eBook Packages : Springer Book Archive
Share this chapter
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
- Find a journal
- Track your research
Is Cartoon Network shutting down? X post sparks rumors about channel’s closure
- Updated: Jul. 10, 2024, 7:52 a.m.
- | Published: Jul. 09, 2024, 12:19 p.m.

General view of the Cartoon Network studios on August 19, 2020, in Burbank, California. (AaronP/Bauer-Griffin/Getty Images) AaronP/Bauer-Griffin/Getty Images
- David Cifarelli | [email protected]
An Animation Workers Ignited post on X fueled rumors that Cartoon Network is closing. But the post was meant to raise awareness about layoffs in the animation industry.
“Cartoon Network would like to clarify that there is no truth to the speculation that the network or the studio are shutting down,” a statement from Warner Brothers sent to MassLive reads. “With a number of recently announced greenlights, we remain committed to continually investing in innovative content that entertains and inspires our viewers across the globe.”
More Entertainment Content:
- Springfield announces 2 more pickleball courts to be built
- Mass. State Lottery winner: Largest prize in 2024 won from $50 scratch ticket
- Mass. State Lottery winner: First $1 million a year for life prize won
- Billie Eilish tour: Buy tickets to sold-out show in Boston, MA this fall
If you purchase a product or register for an account through a link on our site, we may receive compensation. By using this site, you consent to our User Agreement and agree that your clicks, interactions, and personal information may be collected, recorded, and/or stored by us and social media and other third-party partners in accordance with our Privacy Policy.
Pac-12 Networks to go dark Sunday night after 12-year run
The demise of the pac-12 networks sunday night serves as another stark reminder of the wreckage of college football realignment..
The Pac-12 Networks launched in 2012 as a Pac-12 Conference media company that promised lots of programming – seven television channels that eventually produced about 850 live events per year with the help of about 150 full-time employees.
But now it’s all over. The Pac-12 Networks finally will go dark Sunday night at age 12 due to complications from a vexing national outbreak – college football realignment .
“Pac-12 Networks will end its signal for its seven linear television channels on June 30 at midnight,” the league said in an email Thursday. “We will no longer broadcast or program these seven linear TV channels.”
The networks’ killing had been planned for months. Yet as they disappear from cable channels Monday, their death still serves as a stark reminder of realignment’s wreckage and the uncertainty still looming about what remains of the “Conference of Champions.” Here’s a breakdown:
What will happen to those Pac-12 channels?
They won’t be there anymore – the main Pac-12 Network channel or the six regionalized channels, such as Pac-12 Los Angeles and Pac-12 Arizona.
“The networks will go down at 11:59PM PST (Sunday),” the Cox Communications cable and internet company said in an email Thursday. “The channel numbers will still be active for 2 weeks with a screen letting customers know the network is no longer in operation.”
Likewise, Charter Communications recently sent a notice to customers that said the Pac-12 channels will cease programming. But the notice also reminded customers that select former Pac-12 teams soon will be featured on the Big Ten Network or the Atlantic Coast Conference Network.
Why did the Pac-12 Networks die?
There were several causes. The networks never got the distribution they wanted, limiting their exposure with viewers, especially after failing to get a deal with DirecTV. The main Pac-12 Network only had an average of 12.4 million subscribers in 2023, compared to 46.4 million for the Southeastern Conference Network and 43.8 million for the Big Ten Network, according to estimates provided to USA TODAY Sports from S&P Global Market Intelligence.
This stemmed from a lack of demand. Cable providers only paid an average of 14 cents per subscriber per month for the Pac-12 Network, far below the 97 cents per subscriber per month for the SEC Network and 77 cents for Big Ten Network, according to the estimates from S&P Global Market Intelligence.
The 12 Pac-12 universities that owned the Pac-12 Networks also opted to keep full ownership instead of bringing in an equity partner such as ESPN to give them leverage and investment. By contrast, the Big Ten Network is jointly owned by the league (39%) and media company Fox (61%).
Ultimately, these and other revenue shortcomings led Pac-12 schools to leave the league in pursuit of more media rights revenue, bigger viewership and more stability – a realignment that sealed the Pac-12 Networks’ fate.
In 2022, the University of Southern California and UCLA announced they were leaving the Pac-12 for the Big Ten in 2024. Last summer, eight other Pac-12 teams announced they were leaving for the Big 12, Big Ten or ACC, leaving just two orphaned members in the Pac-12 who weren’t invited to other leagues – Oregon State and Washington State. Those moves become official in August.
What happens with the Pac-12 Network properties?
The two remaining schools in the Pac-12 will own the networks’ production facilities in San Ramon, Calif. That is part of a business called Pac-12 Enterprises, which now offers its broadcast production services to external clients, with profits flowing back to the two remaining schools.
It also will produce the telecasts for the 11 home football games that will air on The CW Network for Oregon State and Washington State in 2024.
In basketball and other sports, Oregon State and Washington State will compete as affiliate members of the West Coast Conference. Their home basketball games on the ESPN+ streaming service also will be produced by Pac-12 Enterprises, according to the Pac-12.
How will this help the two Pac-12 schools?
It’s an asset that could be used as a card to play in the shifting sands of any future realignment – a sports television and content business with a full suite of broadcast infrastructure and a track record of producing live sports events.
In the meantime, Oregon State and Washington State can operate as a two-team league for up to two years before deciding what to do next, such as possibly combining with the Mountain West Conference under the Pac-12 banner.
Under NCAA rules, leagues in the Football Bowl Subdivision are required to have at least eight members. But if they fall short of that, they are allowed a two-year grace period and will continue to use and own the Pac-12 name under commissioner Teresa Gould , who has a two-year contract.
How will they spend their final hours?
The last live event on the Pac-12 Network came May 24 with a baseball tournament game in Arizona. It has aired many reruns of previous games since then and is scheduled to televise the 1992 "Snow Bowl" football game between Washington State and Washington late Sunday night before going off air, according to the Cox cable guide.
On Friday, Gould posted a thread on social media site X to note the passing of an era.
“Normally around this time we are celebrating the accomplishments of the academic year & preparing for the next. Instead, today we are saying goodbye to the final group of loyal @pac12 & @Pac12Network staff that are departing an organization they love,” Gould wrote.
She ended the thread with a nod to an uncertain future. There are only about 30 employees left in the Pac-12, including Pac-12 Enterprises, according to the league.
“For the small number of us that are continuing, we will continue to fight for the @pac12, for the Beavs and the Cougs, and for all of you,” she wrote. “We hope to make you proud.”
Follow reporter Brent Schrotenboer @Schrotenboer . Email: [email protected]
- High Schools
- SportsbookWire
- USA TODAY Sports
What channel is Phillies vs. Dodgers game on Wednesday? How to watch, stream, Apple TV+

The Philadelphia Phillies continue a three-game series against the Los Angeles Dodgers on Wednesday at Citizens Bank Park in Philadelphia.
Did the Phillies win last night?
Phillies 10, dodgers 1.
Following the return of Bryce Harper and Kyle Schwarber, the Phillies hammered Dodgers starter Bobby Miller for 9 runs on their way to a 10-1 win. Shortstop Trea Turner had the big blow with a grand slam in the fourth inning.
What time do the Phillies play today?
Philadelphia faces Los Angeles at 7:05 p.m. Wednesday at Citizens Bank Park in Philadelphia. Philadelphia right-hander Cristopher Sánchez (6-4, 2.96 ERA) will face Los Angeles right-hander Gavin Stone (9-2, 3.03 ERA).
What channel is the Phillies game on tonight?
The game will be on ESPN. The radio broadcast will be on 94WIP and WDEL 101.7 FM/1150 AM.
How can I stream tonight's Phillies game?
Every Phillies game is streamed on MLB.com with the MLB TV package , which you have to pay for. You can also stream the radio broadcasts with MLB audio.
When do the Phillies play on Apple TV+ this season?
At this point, the Phillies aren't scheduled for another game on "Friday Night Baseball" on Apple TV+ . However, Apple's schedule is only announced through July. The Phillies could be on Apple TV+ again in August or September.
How can I watch the Phillies on Apple TV+?
You'll need a subscription to Apple TV+ if you want to watch it. A monthly subscription to Apple TV+ is $9.99 . However, Apple TV+ is offering a free trial with the requirement of an email or Apple ID.

The Daily Show Fan Page

Explore the latest interviews, correspondent coverage, best-of moments and more from The Daily Show.
The Daily Show
S29 E70 • July 10, 2024
New York Times reporters Elizabeth Dias and Lisa Lerer discuss their new book “The Fall of Roe” with hosts Jordan Klepper and Desi Lydic.
Extended Interviews

The Daily Show Tickets
Attend a Live Taping
Find out how you can see The Daily Show live and in-person as a member of the studio audience.
Best of Jon Stewart

The Weekly Show with Jon Stewart
New Episodes Thursdays
Jon Stewart and special guests tackle complex issues.
Powerful Politicos

The Daily Show Shop
Great Things Are in Store
Become the proud owner of exclusive gear, including clothing, drinkware and must-have accessories.
About The Daily Show
- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture
Computer Network Tutorial
Basics of computer network.
- Basics of Computer Networking
- Introduction to basic Networking Terminology
- Goals of Networks
- Basic Characteristics of Computer Networks
- Challenges of Computer Network
- Physical Components of Computer Network
Network Hardware and Software
- Types of Computer Networks
- LAN Full Form
- How to Set Up a LAN Network?
- MAN Full Form in Computer Networking
- MAN Full Form
- WAN Full Form
- Introduction of Internetworking
- Difference between Internet, Intranet and Extranet
- Protocol Hierarchies in Computer Network
- Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter)
- Introduction of a Router
- Introduction of Gateways
- What is a network switch, and how does it work?
Network Topology
- Types of Network Topology
- Difference between Physical and Logical Topology
- What is OSI Model? - Layers of OSI Model
- Physical Layer in OSI Model
- Data Link Layer
- Session Layer in OSI model
- Presentation Layer in OSI model
- Application Layer in OSI Model
- Protocol and Standard in Computer Networks
- Examples of Data Link Layer Protocols
- TCP/IP Model
- TCP/IP Ports and Its Applications
- What is TCP (Transmission Control Protocol)?
- TCP 3-Way Handshake Process
- Services and Segment structure in TCP
- TCP Connection Establishment
- TCP Connection Termination
- Fast Recovery Technique For Loss Recovery in TCP
- Difference Between OSI Model and TCP/IP Model
Medium Access Control
- MAC Full Form
- Channel Allocation Problem in Computer Network
- Multiple Access Protocols in Computer Network
- Carrier Sense Multiple Access (CSMA)
- Collision Detection in CSMA/CD
- Controlled Access Protocols in Computer Network
SLIDING WINDOW PROTOCOLS
- Stop and Wait ARQ
- Sliding Window Protocol | Set 3 (Selective Repeat)
- Piggybacking in Computer Networks
IP Addressing
- What is IPv4?
- What is IPv6?
- Introduction of Classful IP Addressing
- Classless Addressing in IP Addressing
- Classful Vs Classless Addressing
- Classless Inter Domain Routing (CIDR)
- Supernetting in Network Layer
- Introduction To Subnetting
- Difference between Subnetting and Supernetting
- Types of Routing
- Difference between Static and Dynamic Routing
- Unicast Routing - Link State Routing
- Distance Vector Routing (DVR) Protocol
- Fixed and Flooding Routing algorithms
- Introduction of Firewall in Computer Network
Congestion Control Algorithms
- Congestion Control in Computer Networks
- Congestion Control techniques in Computer Networks
- Computer Network | Leaky bucket algorithm
- TCP Congestion Control
Network Switching
- Circuit Switching in Computer Network
- Message switching techniques
- Packet Switching and Delays in Computer Network
- Differences Between Virtual Circuits and Datagram Networks
Application Layer:DNS
- Domain Name System (DNS) in Application Layer
- Details on DNS
- Introduction to Electronic Mail
- E-Mail Format
- World Wide Web (WWW)
- HTTP Full Form
- Streaming Stored Video
- What is a Content Distribution Network and how does it work?
CN Interview Quetions
- Top 50 Plus Networking Interview Questions and Answers for 2024
- Top 50 TCP/IP Interview Questions and Answers 2024
- Top 50 IP Addressing Interview Questions and Answers
- Last Minute Notes - Computer Networks
- Computer Network - Cheat Sheet
- Network Layer
- Transport Layer
- Application Layer
A computer network is a collection of computers or devices connected to share resources. Any device which can share or receive the data is called a Node. Through which the information or data propagate is known as channels, It can be guided or unguided.
In this Computer network tutorial, you’ll learn basic to advanced concepts like the Basics of computer networks, data link layer, network layer, network security and cryptography, compression techniques, etc.
Recent Articles on Computer Networks
Table of Content
- Network Security and Cryptography
- Compression Techniques
- Network Experiments
- The Internet and the Web
- Internet and Web programming: Behind the scenes
- The New Internet | Internet of Everything
- Unknown facts of Networking
- Network goals
- Line Configuration in Computer Networks
- Transmission Modes in Computer Networks
- Types of Transmission Media
- Unicast, Broadcast and Multicast
- Introduction to basic Networking terminology
- Network Topologies
- Types of area networks – LAN, MAN and WAN
- Telecom Networks
- Access networks
- Layers of OSI Model
- Introduction to Active Directory Domain Service
- Advantages and Disadvantages of Computer Networking
Data Link Layer :
- Local Area Network (LAN) Technologies.
- Computer Network | Bridges (local Internetworking device)
- Internetworking
- Framing In Data Link Layer
- Introduction of MAC Address
- MAC Filtering
- Multiple Access Protocols
- Ethernet Frame Format
- EtherChannel
- Difference between Byte stuffing and Bit stuffing
- Implementing Byte stuffing using Java
- Circuit Switching
- Packet Switching and Delays
- Circuit Switching VS Packet Switching
- Differences between Virtual Circuits & Datagram Networks
- Switching techniques: Message switching
- Types of switches
- Maximum data rate (channel capacity) for noiseless and noisy channels
- Hot Spot 2.0
- Collision Avoidance in wireless networks
- Traditional wireless mobile communication
- Carrier sense multiple access (CSMA)
- Efficiency of CSMA/CD
- Back-off Algorithm for CSMA/CD
- Controlled Access Protocols
- Virtual LAN (VLAN)
- Inter VLAN Routing by Layer 3 Switch
- Computer Network | Private VLAN
- Computer Network | VLAN ACL (VACL)
- Access and trunk ports
- Role-based access control
- Port security
- Inter-Switch Link (ISL) and IEEE 802.1Q
- Dynamic Trunking Protocol (DTP)
- Sliding Window Protocol | Set 1 (Sender Side)
- Sliding Window Protocol | Set 2 (Receiver Side)
- Sliding Window protocols Summary
- Difference between Stop and Wait, GoBackN and Selective Repeat
- Manchester Encoding
- Error Detection
- Hamming Code
- Program to remotely Power On a PC over the Internet using the Wake-on-LAN protocol.
- Basics of Wi-Fi
- IEEE 802.11 Mac Frame
- Efficiency Of Token Ring
- Token Bus (IEEE 802.4)
- Multiplexing (Channel Sharing)
- Frequency division and Time division multiplexing
Network Layer :
- Integrated services digital network (ISDN)
- Introduction and IPv4 Datagram Header
- IP Addressing | Introduction and Classful Addressing
- IP Addressing | Classless Addressing
- IPv4 classless Subnet equation
- Supernetting
- Ipv4 Datagram Fragmentation and Delays
- Fragmentation at Network Layer
- Internet Protocol v6 | IPv6
- Internet Protocol version 6 (IPv6) Header
- Differences between IPv4 and IPv6
- Internet Control Message Protocol (ICMP)
- Longest Prefix Matching in Routers
- Routing v/s Routed Protocols
- Classes of routing protocols
- Types of routing
- Classification of Routing Algorithms
- Routing Protocols Set 1 (Distance Vector Routing)
- Route Poisoning and Count to infinity problem
- Redundant link problems
- Administrative Distance (AD) and Autonomous System (AS)
- Unicast Routing – Link State Routing
- Link state advertisement (LSA)
- Securing Routing Protocols
- Distance vector routing v/s Link state routing
- Routing Information Protocol (RIP)
- Routing Interface Protocol (RIP) V1 & V2
- Redistribution
- EIGRP fundamentals
- EIGRP Configuration
- Features of Enhanced Interior Gateway Routing Protocol (EIGRP)
- EIGRP cost calculation
- Open shortest path first (OSPF) protocol fundamentals
- Open shortest path first (OSPF) router roles and configuration
- Open shortest path first (OSPF) protocol States
- Open shortest path first (OSPF) – Set 2
- Probabilistic shortest path routing algorithm for optical networks
- Types of Spanning Tree Protocol (STP)
- Network address translation (NAT)
- Types of Network address translation (NAT)
- Static NAT (on ASA)
- Dynamic NAT (on ASA)
- VRRP(Virtual Router Redundancy Protocol) | Introduction and configuration
- Hot Standby Router Protocol (HSRP)
- Hot Standby Router Protocol (HSRP) and Virtual Router Redundancy Protocol (VRRP)
- Router on a stick | Introduction and Configuration
- What’s difference between Ping and Traceroute?
- ARP, Reverse ARP(RARP), Inverse ARP(InARP), Proxy ARP and Gratuitous ARP
- How ARP works?
- Packet flow in the same network
- Packet flow in different network
- Wifi protected access (WPA)
- Wifi protected setup (WPS)
- LiFi vs. WiFi
- Service Set Identifier (SSID)
- Access-lists (ACL)
- Context based access control (CBAC)
- Standard Access-list
- Extended access-list
- Reflexive Access-list
- Time based access-list
- AAA (Authentication, Authorization and Accounting)
- AAA (authentication) configuration (locally)
- Challenge Response Authentication Mechanism (CRAM)
- Synchronous Optical Network (SONET)
- TACACS+ and RADIUS
Transport Layer :
- TCP Sequence Number | Wrap Around Concept
- Transport Layer responsibilities
- Multiplexing and Demultiplexing in Transport Layer
- User Datagram Protocol (UDP)
- P2P(Peer To Peer) File Sharing
- Congestion Control
- Congestion control techniques
- Leaky Bucket Algorithm
- Error Control in TCP
- TCP | Services and Segment structure
- TCP Server-Client implementation in C
- TCP and UDP server using select
Application Layer :
- Protocols in Application Layer
- Simple Mail Transfer Protocol (SMTP)
- DNS (Domain Name Server)
- Why does DNS use UDP and not TCP?
- Address Resolution in DNS
- DNS Spoofing or DNS Cache poisoning
- Types of DNS Attacks and Tactics for Security
- What’s difference between http:// and https:// ?
- What’s difference between HTML and HTTP ?
- HTTP Non-Persistent & Persistent Connection | Set 1
- File Transfer Protocol (FTP)
- What are the differences between HTTP, FTP, and SMTP?
- Asynchronous Transfer Mode (ATM)
- What is Local Host?
- Dynamic Host Configuration Protocol (DHCP)
- DHCP Relay Agent
- How DHCP server dynamically assigns IP address to a host?
- What’s difference between The Internet and The Web ?
- Simple network management protocol (SNMP)
- Multipurpose Internet mail extension (MIME)
- Computer Network | MIME Media Types
- Quality of Service and Multimedia
- Web Caching and the Conditional GET Statements
Network Security and Cryptography :
- The CIA triad
- Introduction to Firewall
- Types of firewall and possible attacks
- Firewall methodologies
- Zone-based firewall
- Zone-based firewall (Configuration)
- How to setup firewall in Linux?
- Message Authentication Codes
- How message authentication code works?
- HMAC Algorithm
- Password authentication protocol (PAP)
- Basic Network Attacks
- Birthday attack
- Vishing (Voice Phishing)
- System security
- Private Browsing
- Threat Modelling
- DFD Based Threat modelling | Set 1
- DFD Based Threat Modelling | Set 2
- Types of Viruses
- Deniel of Service and Prevention
- Denial of Service DDoS attack
- RC4 Encryption Algorithm
- RSA Algorithm in Cryptography
- RSA Algorithm using Multiple Precision Arithmetic Library
- Weak RSA decryption with Chinese-remainder theorem
- How to solve RSA Algorithm Problems?
- Hash Functions in System Security
- DNA Cryptography
- RC5 Encryption Algorithm
- ElGamal Encryption Algorithm
- Caesar Cipher
- Cryptography Introduction
- Cryptography | Traditional Symmetric Ciphers
- Block cipher modes of operation
- Cryptography | Development of Cryptography
- Difference between AES and DES ciphers
- Transforming a Plain Text message to Cipher Text
- What is a cryptocurrency?
- Introduction to Crypto-terminologies
- Quantum Cryptography
- End to End Encryption (E2EE) in Computer Networks
- IP security (IPSec)
- What is Packet Sniffing ?
- Introduction to Sniffers
- Data encryption standard (DES) | Set 1
- End to End Encryption (E2EE) in Computer Network
- Types of Security attacks | Active and Passive attacks
- Types of Wireless and Mobile Device Attacks
- Types of Email Attacks
- Sybil Attack
- Malware and its types
Compression Techniques :
- LZW (Lempel–Ziv–Welch) Compression technique
- Data Compression With Arithmetic Coding
- Shannon-Fano Algorithm for Data Compression
Network Experiments :
- Let’s experiment with Networking
- Mobile Ad hoc Network
- Types of MANET
- Simple Chat Room using Python
- Socket Programming in Java
- C Program to find IP Address, Subnet Mask & Default Gateway
- Introduction to variable length subnet mask (VLSM)
- Extracting MAC address using Python
- Implementation of Diffie-Hellman Algorithm
- Java Implementation of Deffi-Hellman Algorithm between Client and Server
- Socket Programming in Python
- Socket Programming with Multi-threading in Python
- Cyclic Redundancy Check in Python
- Explicitly assigning port number to client in Socket
- Netstat command in Linux:
- nslookup command in Linux with Examples
- UDP Server-Client implementation in C
- C program for file Transfer using UDP
- Java program to find IP address of your computer
- Finding IP address of a URL in Java
- Program to calculate the Round Trip Time (RTT)
- Network configuration and trouble shooting commands in Linux
- Implementing Checksum Using Java
- C Program to display hostname and IP address
- Program to determine class, Network and Host ID of an IPv4 address
- Program to determine Class, Broadcast address and Network address of an IPv4 address
- Program for IP forwarding table lookup
- Wi-Fi Password of All Connected Networks in Windows/Linux
- Network Devices (Hub, Repeater, Bridge, Switch, Router and Gateways)
- Inside a Router
- Bridges (local Internetworking device)
- Switch functions at layer 2
- Collision Domain and Broadcast Domain
- Root Bridge Election in Spanning Tree Protocol
- Onion Routing
- Types of Server Virtualization
- Cloud Computing | Characteristics of Virtualization
- On-premises cost estimates of Virtualization
- Hardware Based Virtualization
- Operating system based Virtualization
- Digital Subscriber Line (DSL)
- Image Steganography
- Network Neutrality
- Basics of NS2 and Otcl/tcl script
- Voice over Internet Protocol (VoIP)
- Cisco router modes
- Cisco router basic commands
- Backing up Cisco IOS router image
- Basic configuration of adaptive security appliance (ASA)
- Adaptive security appliance (ASA) features
- Default flow of traffic (ASA)
- Cisco ASA Redistribution example
- Telnet and SSH on Adaptive security appliance (ASA)
- Near Field Communication (NFC)
- Relabel-to-front Algorithm
- Berkeley’s Algorithm
- Cristian’s Algorithm
- Universal Serial Bus (USB) in Computer Network
- Type-C Port in Computer Network
FAQs on Computer Networks
Q.1 what are the types of computer network.
PAN(Personal Area Network) : It is the network connecting computer devices for personal use within a range of 10 meters. LAN(Local Area Network) : It is a collection of computers connected to each other in a small area for example school, office, or building. WAN(Wide Area Network) : A Wide Area Network is a large area than the LAN. It is spread across the states or countries. MAN(Metropolitan Area Network) : A Metropolitan area network is the collection of interconnected Local Area Networks.
Q.2 What are link and node?
A link is a connection between two or more computers. Link can be wired or wireless between two nodes. A node is refer to any device in a network like computers, laptops, printers, servers, modems, etc.
Q.3 What is the network topology?
Network topology is the physical design of the network, It represents the connectivity between the devices, cables, computers, etc.
Q.4 What are different types of network topology?
There are different types of topology are given below: Bus Topology Star Topology Ring Topology Mesh Topology Tree Topology Hybrid
Quick Links :
- Last Minute Notes(LMNs)
- Quizzes on Computer Networks !
- ‘Practice Problems’ on Computer Networks !
Please Login to comment...
Similar reads, improve your coding skills with practice.
What kind of Experience do you want to share?
Advertisement
How to watch usa basketball vs canada, tv channel info, free live stream, share this article.
USA basketball begins its Pre-Olympic Tour on Wednesday, July 10 when they take on Canada.
Team USA did not exert its usual dominance in last year’s FIBA World Cup , and that has many fans excited to see how this version of the Dream Team will rebound.
With an absolutely stacked roster including LeBron James, Steph Curry , Joel Embiid, Kevin Durant, Jayson Tatum, Anthony Edwards and many more, USA basketball should be a heavy favorite to claim gold in Paris this summer.
WATCH : USA basketball vs. Canada FREE on Fubo
Here’s everything you need to know in order to watch tonight’s first game on the road to Paris.
USA vs. Canada basketball game info
- When : 10:30 p.m. on Wednesday, July 10
- Where : T-Mobile Arena in Las Vegas, Nev,
- TV channel : FS1 ( watch FREE on Fubo )
- Live stream : Fubo
Team USA basketball roster
- Bam Adebayo
- Devin Booker
- Stephen Curry
- Anthony Davis
- Kevin Durant
- Anthony Edwards
- Joel Embiid
- Tyrese Haliburton
- Jrue Holiday
- LeBron James
- Kawhi Leonard
- Jayson Tatum
We occasionally recommend interesting products and services. If you make a purchase by clicking one of the links, we may earn an affiliate fee. FTW operates independently, though, and this doesn’t influence our coverage.
Most Popular
Ranking all 32 nfl teams' primary helmet logos, from worst to best, 2025 nba mock draft 1.0: first-round predictions with cooper flagg to the nets, ace bailey to wizards, hard knocks cameras captured the awkward moment jayden daniels might have failed his giants combine interview, a yankees fan absolutely lasered a rafael devers home run ball back to the mound, caitlin clark joking that nobody reached out about her historic triple-double is amazingly on-brand, aliyah boston posted a very funny tiktok of caitlin clark and her fever teammates hitting the weight room, giant yukon grizzly bear provides riveting trail-cam moment.
Please enter an email address.
Thanks for signing up.
Please check your email for a confirmation.
Something went wrong.

IMAGES
VIDEO
COMMENTS
Channel Allocation means to allocate the available channels to the cells in a cellular system. When a user wants to make a call request then by using channel allocation strategies their requests are fulfilled. Channel Allocation Strategies are designed in such a way that there is efficient use of frequencies, time slots and bandwidth.
Channel allocation schemes. In radio resource management for wireless and cellular networks, channel allocation schemes allocate bandwidth and communication channels to base stations, access points and terminal equipment. The objective is to achieve maximum system spectral efficiency in bit/s/Hz/site by means of frequency reuse, but still ...
As traffic increases more channels are assigned and vice-versa. Difference between Fixed Channel Allocation (FCA) and Dynamic Channel Allocation (DCA): Fixed number of channels or voice channels are allocated to cells. Fixed number of channels are not allocated to cells. If all the channels are occupied and user make a call then the call will ...
Abstract. Channel assignment techniques are used extensively in frequency reuse systems to assign time-frequency resources to each user. There are many methods of allocating a channel upon a new call arrival or handoff attempt. A good channel allocation algorithm is the one that yields high spectral efficiency for a specified quality of service ...
The Channel Assignment (CA) is an efficient tool to exploit multiple non-overlapping channels to minimize interference and enhance the capacity of the wireless mesh network. Even though the CA can minimize the total network interference, its result may cause some design issues which influence the network performance.
The total number of available channels on a real-world network is in fact a scarce resource, and many assignment heuristics suffer from a clear lack of flexibility (this is the case of Fixed Channel Allocation), or from high computational and communication complexity (as with channel borrowing techniques).
contention are still major factors in such networks. Then, an e cient channel assignment scheme is required to enhance the overall throughput. In this paper, we present three mo-dels to evaluate network capacity associated to any channel assignment strategy. These models permit also to extract what we could obtain with an optimal centralized ...
S. Wu, C. Lin, Y. Tseng, and J. Sheu, "A new multi-channel MAC protocol with on- demand channel assignment for multi-hop mobile ad hoc networks," submitted to the International Symposium on Parallel Architectures, Algorithms, and Networks (ISPAN), 2000.
Channel Assignment (CA) is a mechanism which selects the best chan- nels for an individual wireless node or the entire network aiming to increase the capacity of the network.
Dynamic channel assignment combined with circuit-based technology (which has generally been the approach taken to date) can provide some benefits. However, it cannot provide large-capacity gains, because of the dynamics of interference in a mobile system as well as the difficulty in implementing rapid channel reassignment.
Channels are communication resources we assign to a user to establish communication with other users in the network. These resources include frequency, time, code, space, bandwidth, and so on. We name each channelization protocol based on the kind of channel resources we employ for channelization. These protocols are:
The channel assignment (CA) in a multi-interface WMN consists of a task to assign channels to the radio interfaces by such a way to achieve efficient channel utilization and to minimize the interference. The problem of optimally assigning channels in an arbitrary mesh topology has been proved to be NP-hard (non-deterministic polynomial-time hard) based on its mapping to a graph-coloring ...
What is channel allocation in computer network - When there are more than one user who desire to access a shared network channel, an algorithm is deployed for channel allocation among the competing users. The network channel may be a single cable or optical fiber connecting multiple nodes, or a portion of the wireless spectrum.
Channel assignment strategies in mobile communication are used to allocate available radio channels to mobile users in a way that maximizes spectrum utilization and minimizes interference. This is important because the radio spectrum is a limited resource, and there is a growing demand for mobile communication services.
In [1] and [9] some surprising channel assignment results are provided for uniform random placement of mobile units into a cellular network employing the cellular assignment results of this paper. The canonical structure and simplic-ity of our cellular assignment graphs for strong overlap seg-ments suggests that some deeper theoretical probabilistic re-sults may be accessible for associated ...
The Dynamic Channel Assignment (DCA) Algorithm. The Group Leader maintains the neighbor lists for all AP's in the RF Group, and organizes these neighbors into RF Neighborhoods. The following metrics are also tracked for each AP in the RF Group. Same Channel Contention—other AP's/clients on the same channel - also known as Co-Channel ...
Over time, and especially with changes in the network architecture the user sensitivity threshold (dampening) can lead to sub optimal channel assignments. Most network architectures change over time, and DCA's rules assume a steady state network.
The Partially Overlapped Channel Assignment (POCA) algorithm proposed by [20] considered network traffic to minimise total network interference but not considered distributed channel assignment.
In [2] the authors introduce a centralized channel as-signment algorithm, MCCA (Maxflow-based Centralized Channel Assignment), developed for multi-radio wireless mesh networks in order to maximize network capacity and reduce interference.
The channel assignment problem between sender and receiver can be easily transformed into Maximum Bipartite Matching (MBP) problem that can be solved by converting it into a flow network. Step 1: Build a Flow Network. There must be a source and sink in a flow network.
Networking assignment 15 configuring etherchannels this chapter describes how to configure etherchannels on layer or layer lan ports in cisco ios software
larger volume of handoff attempts in microcellular networks demand careful attention. Furthermore, a microcellular channel assignment strategy has to be fast, because the handoffs must be serviced quickly due to the small cell sizes and propagation anomalies such as the street corner effect.
An Animation Workers Ignited post on X fueled rumors that Cartoon Network is closing. But the post was meant to raise awareness about layoffs in the animation industry. "Cartoon Network would ...
The demise of the Pac-12 Networks Sunday night serves as another stark reminder of the wreckage of college football realignment.
The Phillies face the Los Angeles Dodgers today. Here's how to watch and stream the game.
More than 50 million people across the US are under heat alerts amid a brutal heat wave that has shattered records and caused multiple deaths across the West.
The source for The Daily Show fans, with episodes hosted by Jon Stewart, Ronny Chieng, Jordan Klepper, Dulcé Sloan and more, plus interviews, highlights and The Weekly Show podcast.
In this Computer network tutorial, you'll learn basic to advanced concepts like the Basics of computer networks, data link layer, network layer, network security and cryptography, compression techniques, etc.
USA Basketball begins its Pre-Olympic Tour on Wednesday, July 10 with an exhibition game against Canada in Las Vegas. Here's how to watch
The ABC News interview with President Joe Biden will now air "in its entirety as a primetime special" on Friday evening at 8:00 P.M. ET/PT, the network announced Wednesday evening.