Developing an Asynchronous Task Queue in Python
Share this tutorial.
- Hacker News
This tutorial looks at how to implement several asynchronous task queues using Python's multiprocessing library and Redis .

Queue Data Structures
Following along, multiprocessing pool, multiprocessing queue.
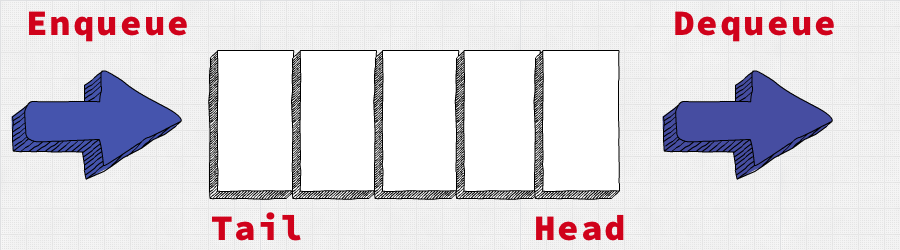
A queue is a First-In-First-Out ( FIFO ) data structure.
- an item is added at the tail ( enqueue )
- an item is removed at the head ( dequeue )
You'll see this in practice as you code out the examples in this tutorial.
Let's start by creating a basic task:
So, get_word_counts finds the twenty most frequent words from a given text file and saves them to an output file. It also prints the current process identifier (or pid) using Python's os library.
Create a project directory along with a virtual environment. Then, use pip to install NLTK :
Once installed, invoke the Python shell and download the stopwords corpus :
If you experience an SSL error refer to this article. Example fix: >>> import nltk >>> nltk.download ( 'stopwords' ) [ nltk_data ] Error loading stopwords: <urlopen error [ SSL: [ nltk_data ] CERTIFICATE_VERIFY_FAILED ] certificate verify failed: [ nltk_data ] unable to get local issuer certificate ( _ssl.c:1056 ) > False >>> import ssl >>> try: ... _create_unverified_https_context = ssl._create_unverified_context ... except AttributeError: ... pass ... else : ... ssl._create_default_https_context = _create_unverified_https_context ... >>> nltk.download ( 'stopwords' ) [ nltk_data ] Downloading package stopwords to [ nltk_data ] /Users/michael.herman/nltk_data... [ nltk_data ] Unzipping corpora/stopwords.zip. True
Add the above tasks.py file to your project directory but don't run it quite yet.
We can run this task in parallel using the multiprocessing library:
Here, using the Pool class, we processed four tasks with two processes.
Did you notice the map_async method? There are essentially four different methods available for mapping tasks to processes. When choosing one, you have to take multi-args, concurrency, blocking, and ordering into account:
| Method | Multi-args | Concurrency | Blocking | Ordered-results |
|---|---|---|---|---|
| No | Yes | Yes | Yes | |
| No | No | No | Yes | |
| Yes | No | Yes | No | |
| Yes | Yes | No | No |
Without both close and join , garbage collection may not occur, which could lead to a memory leak.
- close tells the pool not to accept any new tasks
- join tells the pool to exit after all tasks have completed
Following along? Grab the Project Gutenberg sample text files from the "data" directory in the simple-task-queue repo, and then add an "output" directory. Your project directory should look like this: ├── data │ ├── dracula.txt │ ├── frankenstein.txt │ ├── heart-of-darkness.txt │ └── pride-and-prejudice.txt ├── output ├── simple_pool.py └── tasks.py
It should take less than a second to run:
This script ran on a i9 Macbook Pro with 16 cores.
So, the multiprocessing Pool class handles the queuing logic for us. It's perfect for running CPU-bound tasks or really any job that can be broken up and distributed independently. If you need more control over the queue or need to share data between multiple processes, you may want to look at the Queue class.
For more on this along with the difference between parallelism (multiprocessing) and concurrency (multithreading), review the Speeding Up Python with Concurrency, Parallelism, and asyncio article.
Let's look at a simple example:
The Queue class, also from the multiprocessing library, is a basic FIFO (first in, first out) data structure. It's similar to the queue.Queue class, but designed for interprocess communication. We used put to enqueue an item to the queue and get to dequeue an item.
Check out the Queue source code for a better understanding of the mechanics of this class.
Now, let's look at more advanced example:
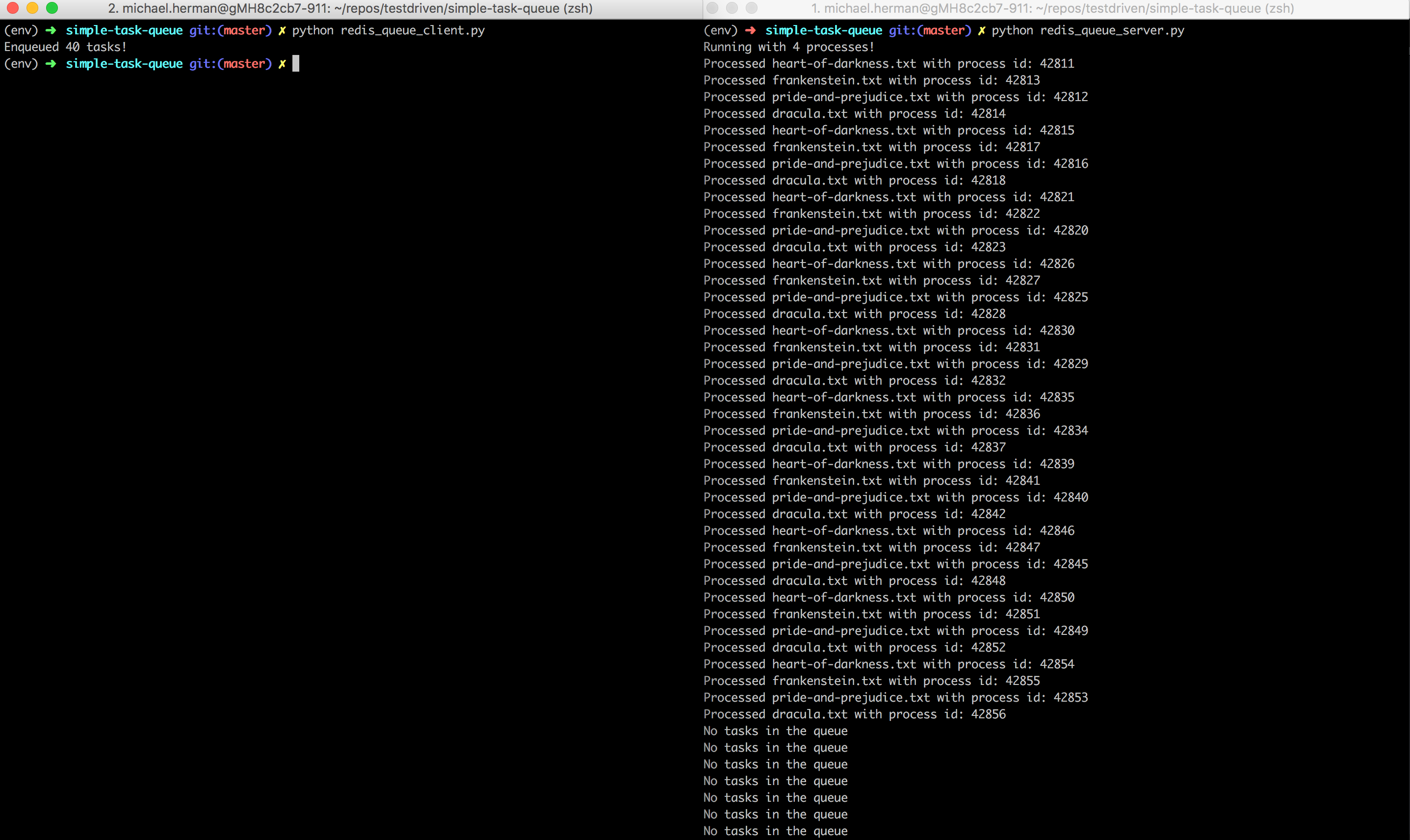
Here, we enqueued 40 tasks (ten for each text file) to the queue, created separate processes via the Process class, used start to start running the processes, and, finally, used join to complete the processes.
It should still take less than a second to run.
Challenge : Check your understanding by adding another queue to hold completed tasks. You can enqueue them within the process_tasks function.
The multiprocessing library provides support for logging as well:
To test, change task_queue.put("dracula.txt") to task_queue.put("drakula.txt") . You should see the following error outputted ten times in the terminal:
Want to log to disc?
Again, cause an error by altering one of the file names, and then run it. Take a look at process.log . It's not quite as organized as it should be since the Python logging library does not use shared locks between processes. To get around this, let's have each process write to its own file. To keep things organized, add a logs directory to your project folder:
Moving right along, instead of using an in-memory queue, let's add Redis into the mix.
Following along? Download and install Redis if you do not already have it installed. Then, install the Python interface : (env)$ pip install redis == 4 .5.5
We'll break the logic up into four files:
- redis_queue.py creates new queues and tasks via the SimpleQueue and SimpleTask classes, respectively.
- redis_queue_client enqueues new tasks.
- redis_queue_worker dequeues and processes tasks.
- redis_queue_server spawns worker processes.
Here, we defined two classes, SimpleQueue and SimpleTask :
- SimpleQueue creates a new queue and enqueues, dequeues, and gets the length of the queue.
- SimpleTask creates new tasks, which are used by the instance of the SimpleQueue class to enqueue new tasks, and processes new tasks.
Curious about lpush() , brpop() , and llen() ? Refer to the Command reference page. ( The brpop() function is particularly cool because it blocks the connection until a value exists to be popped!)
This module will create a new instance of Redis and the SimpleQueue class. It will then enqueue 40 tasks.
If a task is available, the dequeue method is called, which then de-serializes the task and calls the process_task method (in redis_queue.py ).
The run method spawns four new worker processes.
You probably don’t want four processes running at once all the time, but there may be times that you will need four or more processes. Think about how you could programmatically spin up and down additional workers based on demand.
To test, run redis_queue_server.py and redis_queue_client.py in separate terminal windows:
Check your understanding again by adding logging to the above application.
In this tutorial, we looked at a number of asynchronous task queue implementations in Python. If the requirements are simple enough, it may be easier to develop a queue in this manner. That said, if you're looking for more advanced features -- like task scheduling, batch processing, job prioritization, and retrying of failed tasks -- you should look into a full-blown solution. Check out Celery , RQ , or Huey .
Grab the final code from the simple-task-queue repo.
Full-text Search in Django with Postgres and Elasticsearch
Learn how to add full-text search to Django with both Postgres and Elasticsearch.
Recommended Tutorials
Stay sharp with course updates.
Join our mailing list to be notified about updates and new releases.
Send Us Feedback
Flask by Example – Implementing a Redis Task Queue
Table of Contents
Install Requirements
Set up the worker, update app.py, get results, what’s next.
This part of the tutorial details how to implement a Redis task queue to handle text processing.
- 02/12/2020: Upgraded to Python version 3.8.1 as well as the latest versions of Redis, Python Redis, and RQ. See below for details. Mention a bug in the latest RQ version and provide a solution. Solved the http before https bug.
- 03/22/2016: Upgraded to Python version 3.5.1 as well as the latest versions of Redis, Python Redis, and RQ. See below for details.
- 02/22/2015: Added Python 3 support.
Free Bonus: Click here to get access to a free Flask + Python video tutorial that shows you how to build Flask web app, step-by-step.
Remember: Here’s what we’re building—A Flask app that calculates word-frequency pairs based on the text from a given URL.
- Part One : Set up a local development environment and then deploy both a staging and a production environment on Heroku.
- Part Two : Set up a PostgreSQL database along with SQLAlchemy and Alembic to handle migrations.
- Part Three : Add in the back-end logic to scrape and then process the word counts from a webpage using the requests, BeautifulSoup, and Natural Language Toolkit (NLTK) libraries.
- Part Four: Implement a Redis task queue to handle the text processing. ( current )
- Part Five : Set up Angular on the front-end to continuously poll the back-end to see if the request is done processing.
- Part Six : Push to the staging server on Heroku - setting up Redis and detailing how to run two processes (web and worker) on a single Dyno.
- Part Seven : Update the front-end to make it more user-friendly.
- Part Eight : Create a custom Angular Directive to display a frequency distribution chart using JavaScript and D3.
Need the code? Grab it from the repo .
Tools used:
- Redis ( 5.0.7 )
- Python Redis ( 3.4.1 )
- RQ ( 1.2.2 ) - a simple library for creating a task queue
Start by downloading and installing Redis from either the official site or via Homebrew ( brew install redis ). Once installed, start the Redis server:
Next install Python Redis and RQ in a new terminal window:
Let’s start by creating a worker process to listen for queued tasks. Create a new file worker.py , and add this code:
Here, we listened for a queue called default and established a connection to the Redis server on localhost:6379 .
Fire this up in another terminal window:
Now we need to update our app.py to send jobs to the queue…
Add the following imports to app.py :
Then update the configuration section:
q = Queue(connection=conn) set up a Redis connection and initialized a queue based on that connection.
Move the text processing functionality out of our index route and into a new function called count_and_save_words() . This function accepts one argument, a URL, which we will pass to it when we call it from our index route.
Take note of the following code:
Note: We need to import the count_and_save_words function in our function index as the RQ package currently has a bug, where it won’t find functions in the same module.
Here we used the queue that we initialized earlier and called the enqueue_call() function. This added a new job to the queue and that job ran the count_and_save_words() function with the URL as the argument. The result_ttl=5000 line argument tells RQ how long to hold on to the result of the job for - 5,000 seconds, in this case. Then we outputted the job id to the terminal. This id is needed to see if the job is done processing.
Let’s setup a new route for that…
Let’s test this out.
Fire up the server, navigate to http://localhost:5000/ , use the URL https://realpython.com , and grab the job id from the terminal. Then use that id in the ‘/results/’ endpoint - i.e., http://localhost:5000/results/ef600206-3503-4b87-a436-ddd9438f2197 .
As long as less than 5,000 seconds have elapsed before you check the status, then you should see an id number, which is generated when we add the results to the database:
Now, let’s refactor the route slightly to return the actual results from the database in JSON:
Make sure to add the import:
Test this out again. If all went well, you should see something similar to in your browser:
In Part 5 we’ll bring the client and server together by adding Angular into the mix to create a poller , which will send a request every five seconds to the /results/<job_key> endpoint asking for updates. Once the data is available, we’ll add it to the DOM.
This is a collaboration piece between Cam Linke, co-founder of Startup Edmonton , and the folks at Real Python
🐍 Python Tricks 💌
Get a short & sweet Python Trick delivered to your inbox every couple of days. No spam ever. Unsubscribe any time. Curated by the Real Python team.
About The Team
Each tutorial at Real Python is created by a team of developers so that it meets our high quality standards. The team members who worked on this tutorial are:

Master Real-World Python Skills With Unlimited Access to Real Python
Join us and get access to thousands of tutorials, hands-on video courses, and a community of expert Pythonistas:
Join us and get access to thousands of tutorials, hands-on video courses, and a community of expert Pythonistas:
What Do You Think?
What’s your #1 takeaway or favorite thing you learned? How are you going to put your newfound skills to use? Leave a comment below and let us know.
Commenting Tips: The most useful comments are those written with the goal of learning from or helping out other students. Get tips for asking good questions and get answers to common questions in our support portal . Looking for a real-time conversation? Visit the Real Python Community Chat or join the next “Office Hours” Live Q&A Session . Happy Pythoning!
Keep Learning
Related Topics: databases flask web-dev
Keep reading Real Python by creating a free account or signing in:
Already have an account? Sign-In
Almost there! Complete this form and click the button below to gain instant access:

Free Flask Video Tutorial: Build a Python + Flask Web App, From Scratch
🔒 No spam. We take your privacy seriously.
Use Python to build your side business with the Python for Entrepreneurs video course!
Task queues
Task queues manage background work that must be executed outside the usual HTTP request-response cycle.
Why are task queues necessary?
Tasks are handled asynchronously either because they are not initiated by an HTTP request or because they are long-running jobs that would dramatically reduce the performance of an HTTP response.
For example, a web application could poll the GitHub API every 10 minutes to collect the names of the top 100 starred repositories. A task queue would handle invoking code to call the GitHub API, process the results and store them in a persistent database for later use.
Another example is when a database query would take too long during the HTTP request-response cycle. The query could be performed in the background on a fixed interval with the results stored in the database. When an HTTP request comes in that needs those results a query would simply fetch the precalculated result instead of re-executing the longer query. This precalculation scenario is a form of caching enabled by task queues.
Other types of jobs for task queues include
spreading out large numbers of independent database inserts over time instead of inserting everything at once
aggregating collected data values on a fixed interval, such as every 15 minutes
scheduling periodic jobs such as batch processes
Task queue projects
The defacto standard Python task queue is Celery. The other task queue projects that arise tend to come from the perspective that Celery is overly complicated for simple use cases. My recommendation is to put the effort into Celery's reasonable learning curve as it is worth the time it takes to understand how to use the project.
The Celery distributed task queue is the most commonly used Python library for handling asynchronous tasks and scheduling.
The RQ (Redis Queue) is a simple Python library for queueing jobs and processing them in the background with workers. RQ is backed by Redis and is designed to have a low barrier to entry. The intro post contains information on design decisions and how to use RQ.
Taskmaster is a lightweight simple distributed queue for handling large volumes of one-off tasks.
Huey is a simple task queue that uses Redis on the backend but otherwise does not depend on other libraries. The project was previously known as Invoker and the author changed the name.
Huey is a Redis-based task queue that aims to provide a simple, yet flexible framework for executing tasks. Huey supports task scheduling, crontab-like repeating tasks, result storage and automatic retry in the event of failure.
Hosted message and task queue services
Task queue third party services aim to solve the complexity issues that arise when scaling out a large deployment of distributed task queues.
Iron.io is a distributed messaging service platform that works with many types of task queues such as Celery. It also is built to work with other IaaS and PaaS environments such as Amazon Web Services and Heroku.
Amazon Simple Queue Service (SQS) is a set of five APIs for creating, sending, receiving, modifying and deleting messages.
CloudAMQP is at its core managed servers with RabbitMQ installed and configured. This service is an option if you are using RabbitMQ and do not want to maintain RabbitMQ installations on your own servers.
Open source examples that use task queues
Take a look at the code in this open source Flask application and this Django application for examples of how to use and deploy Celery with a Redis broker to send text messages with these frameworks.
flask-celery-example is a simple Flask application with Celery as a task queue and Redis as the broker.
Task queue resources
Getting Started Scheduling Tasks with Celery is a detailed walkthrough for setting up Celery with Django (although Celery can also be used without a problem with other frameworks).
International Space Station notifications with Python and Redis Queue (RQ) shows how to combine the RQ task queue library with Flask to send text message notifications every time a condition is met - in this blog post's case that the ISS is currently flying over your location on Earth.
Evaluating persistent, replicated message queues is a detailed comparison of Amazon SQS, MongoDB, RabbitMQ, HornetQ and Kafka's designs and performance.
Queues.io is a collection of task queue systems with short summaries for each one. The task queues are not all compatible with Python but ones that work with it are tagged with the "Python" keyword.
Why Task Queues is a presentation for what task queues are and why they are needed.
Flask by Example Implementing a Redis Task Queue provides a detailed walkthrough of setting up workers to use RQ with Redis.
How to use Celery with RabbitMQ is a detailed walkthrough for using these tools on an Ubuntu VPS.
Heroku has a clear walkthrough for using RQ for background tasks .
Introducing Celery for Python+Django provides an introduction to the Celery task queue.
Celery - Best Practices explains things you should not do with Celery and shows some underused features for making task queues easier to work with.
The "Django in Production" series by Rob Golding contains a post specifically on Background Tasks .
Asynchronous Processing in Web Applications Part One and Part Two are great reads for understanding the difference between a task queue and why you shouldn't use your database as one.
Celery in Production on the Caktus Group blog contains good practices from their experience using Celery with RabbitMQ, monitoring tools and other aspects not often discussed in existing documentation.
A 4 Minute Intro to Celery is a short introductory task queue screencast.
Heroku wrote about how to secure Celery when tasks are otherwise sent over unencrypted networks.
Miguel Grinberg wrote a nice post on using the task queue Celery with Flask . He gives an overview of Celery followed by specific code to set up the task queue and integrate it with Flask.
3 Gotchas for Working with Celery are things to keep in mind when you're new to the Celery task queue implementation.
Deferred Tasks and Scheduled Jobs with Celery 3.1, Django 1.7 and Redis is a video along with code that shows how to set up Celery with Redis as the broker in a Django application.
Setting up an asynchronous task queue for Django using Celery and Redis is a straightforward tutorial for setting up the Celery task queue for Django web applications using the Redis broker on the back end.
Background jobs with Django and Celery shows the code and a simple explanation of how to use Celery with Django .
Asynchronous Tasks With Django and Celery shows how to integrate Celery with Django and create Periodic Tasks.
Three quick tips from two years with Celery provides some solid advice on retry delays, the -Ofair flag and global task timeouts for Celery.
Task queue learning checklist
Pick a slow function in your project that is called during an HTTP request.
Determine if you can precompute the results on a fixed interval instead of during the HTTP request. If so, create a separate function you can call from elsewhere then store the precomputed value in the database.
Read the Celery documentation and the links in the resources section below to understand how the project works.
Install a message broker such as RabbitMQ or Redis and then add Celery to your project. Configure Celery to work with the installed message broker.
Use Celery to invoke the function from step one on a regular basis.
Have the HTTP request function use the precomputed value instead of the slow running code it originally relied upon.
What's next to learn after task queues?
How do I log errors that occur in my application?
I want to learn more about app users via web analytics.
What tools exist for monitoring a deployed web app?
Sign up here to receive a monthly email with major updates to this site, tutorials and discount codes for Python books.

Searching for a complete, step-by-step deployment walkthrough? Learn more about The Full Stack Python Guide to Deployments book .
Email Updates
Sign up to get a monthly email with python tutorials and major updates to this site., table of contents, task queues.

- Contributing
RQ ( Redis Queue ) is a simple Python library for queueing jobs and processing them in the background with workers. It is backed by Redis and it is designed to have a low barrier to entry. It can be integrated in your web stack easily.
RQ requires Redis >= 3.0.0.
Getting started
First, run a Redis server. You can use an existing one. To put jobs on queues, you don’t have to do anything special, just define your typically lengthy or blocking function:
Then, create a RQ queue:
And enqueue the function call:
Scheduling jobs are similarly easy:
You can also ask RQ to retry failed jobs:
To start executing enqueued function calls in the background, start a worker from your project’s directory:
That’s about it.
Installation
Simply use the following command to install the latest released version:
If you want the cutting edge version (that may well be broken), use this:
Project history
This project has been inspired by the good parts of Celery , Resque and this snippet , and has been created as a lightweight alternative to existing queueing frameworks, with a low barrier to entry.
Using Python RQ for Task Queues in Python
This is a getting started on python-rq tutorial and I will demonstrate how to work with asynchronous tasks using python redis queue (python-rq).
What will we be doing
We want a client to submit 1000's of jobs in a non-blocking asynchronous fashion, and then we will have workers which will consume these jobs from our redis queue, and process those tasks at the rate of what our consumer can handle.
The nice thing about this is that, if our consumer is unavailable for processing the tasks will remain in the queue and once the consumer is ready to consume, the tasks will be executed. It's also nice that its asynchronous, so the client don't have to wait until the task has finished.
We will run a redis server using docker, which will be used to queue all our jobs, then we will go through the basics in python and python-rq such as:
- Writing a Task
- Enqueueing a Job
- Getting information from our queue, listing jobs, job statuses
- Running our workers to consume from the queue and action our tasks
- Basic application which queues jobs to the queue, consumes and action them and monitors the queue
Redis Server
You will require docker for this next step, to start the redis server:
Install python-rq:
Create the task which will be actioned by our workers, in our case it will just be a simple function that adds all the numbers from a given string to a list, then adds them up and return the total value.
This is however a very basic task, but its just for demonstration.
Our tasks.py :
To test this locally:
Now, lets import redis and redis-queue, with our tasks and instantiate a queue object:
Submit a Task to the Queue
Let's submit a task to the queue:
We have a couple of properties from result which we can inspect, first let's have a look at the id that we got back when we submitted our task to the queue:
We can also get the status from our task:
We can also view our results in json format:
If we dont have context of the job id, we can use get_jobs to get all the jobs which is queued:
Then we can loop through the results and get the id like below:
Or to get the job id's in a list:
Since we received the job id, we can use fetch_job to get more info about the job:
And as before we can view it in json format:
We can also view the key in redis by passing the job_id:
To view how many jobs are in our queue, we can either do:
Consuming from the Queue
Now that our task is queued, let's fire of our worker to consume the job from the queue and action the task:
Now, when we get the status of our job, you will see that it finished:
And to get the result from our worker:
And like before, if you dont have context of your job id, you can get the job id, then return the result:
Naming Queues
We can namespace our tasks into specific queues, for example if we want to create queue1 :
To verify the queue name:
As we can see our queue is empty:
Let's submit 10 jobs to our queue:
To verify the number of jobs in our queue:
And to count them:
Cleaning the Queue
Cleaning the queue can either be done with:
Then to verify that our queue is clean:
Naming Workers
The same way that we defined a name for our queue, we can define a name for our workers:
Which means you can have different workers consuming jobs from specific queues.
Documentation:
- https://python-rq.org/docs/
- https://python-rq.org/docs/workers/
- https://python-rq.org/docs/monitoring/
Thanks for reading, feel free to check out my website , and subscrube to my newsletter or follow me at @ruanbekker on Twitter.
- Linktree: https://go.ruan.dev/links
- Patreon: https://go.ruan.dev/patreon

Navigation Menu
Search code, repositories, users, issues, pull requests..., provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications You must be signed in to change notification settings
Python task queue using Redis
closeio/tasktiger
Folders and files.
| Name | Name | |||
|---|---|---|---|---|
| 351 Commits | ||||
Repository files navigation
TaskTiger is a Python task queue using Redis.
(Interested in working on projects like this? Close is looking for great engineers to join our team)
Quick start
Configuration, task decorator, task options, custom retrying, inspect, requeue and delete tasks, pause queue processing, rollbar error handling, cleaning up error'd tasks, running the test suite, releasing a new version.
Per-task fork or synchronous worker
By default, TaskTiger forks a subprocess for each task, This comes with several benefits: Memory leaks caused by tasks are avoided since the subprocess is terminated when the task is finished. A hard time limit can be set for each task, after which the task is killed if it hasn't completed. To ensure performance, any necessary Python modules can be preloaded in the parent process.
TaskTiger also supports synchronous workers, which allows for better performance due to no forking overhead, and tasks have the ability to reuse network connections. To prevent memory leaks from accumulating, workers can be set to shutdown after a certain amount of time, at which point a supervisor can restart them. Workers also automatically exit on on hard timeouts to prevent an inconsistent process state.
Unique queues
TaskTiger has the option to avoid duplicate tasks in the task queue. In some cases it is desirable to combine multiple similar tasks. For example, imagine a task that indexes objects (e.g. to make them searchable). If an object is already present in the task queue and hasn't been processed yet, a unique queue will ensure that the indexing task doesn't have to do duplicate work. However, if the task is already running while it's queued, the task will be executed another time to ensure that the indexing task always picks up the latest state.
TaskTiger can ensure to never execute more than one instance of tasks with similar arguments by acquiring a lock. If a task hits a lock, it is requeued and scheduled for later executions after a configurable interval.
Task retrying
TaskTiger lets you retry exceptions (all exceptions or a list of specific ones) and comes with configurable retry intervals (fixed, linear, exponential, custom).
Flexible queues
Tasks can be easily queued in separate queues. Workers pick tasks from a randomly chosen queue and can be configured to only process specific queues, ensuring that all queues are processed equally. TaskTiger also supports subqueues which are separated by a period. For example, you can have per-customer queues in the form process_emails.CUSTOMER_ID and start a worker to process process_emails and any of its subqueues. Since tasks are picked from a random queue, all customers get equal treatment: If one customer is queueing many tasks it can't block other customers' tasks from being processed. A maximum queue size can also be enforced.
Batch queues
Batch queues can be used to combine multiple queued tasks into one. That way, your task function can process multiple sets of arguments at the same time, which can improve performance. The batch size is configurable.
Scheduled and periodic tasks
Tasks can be scheduled for execution at a specific time. Tasks can also be executed periodically (e.g. every five seconds).
Structured logging
TaskTiger supports JSON-style logging via structlog, allowing more flexibility for tools to analyze the log. For example, you can use TaskTiger together with Logstash, Elasticsearch, and Kibana.
The structlog processor tasktiger.logging.tasktiger_processor can be used to inject the current task id into all log messages.
Reliability
TaskTiger atomically moves tasks between queue states, and will re-execute tasks after a timeout if a worker crashes.
Error handling
If an exception occurs during task execution and the task is not set up to be retried, TaskTiger stores the execution tracebacks in an error queue. The task can then be retried or deleted manually. TaskTiger can be easily integrated with error reporting services like Rollbar.
Admin interface
A simple admin interface using flask-admin exists as a separate project ( tasktiger-admin ).
It is easy to get started with TaskTiger.
Create a file that contains the task(s).
Queue the task using the delay method.
Run a worker (make sure the task code can be found, e.g. using PYTHONPATH ).
A TaskTiger object keeps track of TaskTiger's settings and is used to decorate and queue tasks. The constructor takes the following arguments:
Redis connection object. The connection should be initialized with decode_responses=True to avoid encoding problems on Python 3.
Dict with config options. Most configuration options don't need to be changed, and a full list can be seen within TaskTiger 's __init__ method.
Here are a few commonly used options:
ALWAYS_EAGER
If set to True , all tasks except future tasks ( when is a future time) will be executed locally by blocking until the task returns. This is useful for testing purposes.
BATCH_QUEUES
Set up queues that will be processed in batch, i.e. multiple jobs are taken out of the queue at the same time and passed as a list to the worker method. Takes a dict where the key represents the queue name and the value represents the batch size. Note that the task needs to be declared as batch=True . Also note that any subqueues will be automatically treated as batch queues, and the batch value of the most specific subqueue name takes precedence.
ONLY_QUEUES
If set to a non-empty list of queue names, a worker only processes the given queues (and their subqueues), unless explicit queues are passed to the command line.
setup_structlog
If set to True, sets up structured logging using structlog when initializing TaskTiger. This makes writing custom worker scripts easier since it doesn't require the user to set up structlog in advance.
TaskTiger provides a task decorator to specify task options. Note that simple tasks don't need to be decorated. However, decorating the task allows you to use an alternative syntax to queue the task, which is compatible with Celery:
Tasks support a variety of options that can be specified either in the task decorator, or when queueing a task. For the latter, the delay method must be called on the TaskTiger object, and any options in the task decorator are overridden.
When queueing a task, the task needs to be defined in a module other than the Python file which is being executed. In other words, the task can't be in the __main__ module. TaskTiger will give you back an error otherwise.
The following options are supported by both delay and the task decorator:
Name of the queue where the task will be queued.
hard_timeout
If the task runs longer than the given number of seconds, it will be killed and marked as failed.
Boolean to indicate whether the task will only be queued if there is no similar task with the same function, arguments, and keyword arguments in the queue. Note that multiple similar tasks may still be executed at the same time since the task will still be inserted into the queue if another one is being processed. Requeueing an already scheduled unique task will not change the time it was originally scheduled to execute at.
If set, this implies unique=True and specifies the list of kwargs to use to construct the unique key. By default, all args and kwargs are serialized and hashed.
Boolean to indicate whether to hold a lock while the task is being executed (for the given args and kwargs). If a task with similar args/kwargs is queued and tries to acquire the lock, it will be retried later.
If set, this implies lock=True and specifies the list of kwargs to use to construct the lock key. By default, all args and kwargs are serialized and hashed.
max_queue_size
A maximum queue size can be enforced by setting this to an integer value. The QueueFullException exception will be raised when queuing a task if this limit is reached. Tasks in the active , scheduled , and queued states are counted against this limit.
Takes either a datetime (for an absolute date) or a timedelta (relative to now). If given, the task will be scheduled for the given time.
Boolean to indicate whether to retry the task when it fails (either because of an exception or because of a timeout). To restrict the list of failures, use retry_on . Unless retry_method is given, the configured DEFAULT_RETRY_METHOD is used.
If a list is given, it implies retry=True . The task will be only retried on the given exceptions (or its subclasses). To retry the task when a hard timeout occurs, use JobTimeoutException .
retry_method
If given, implies retry=True . Pass either:
- a function that takes the retry number as an argument, or,
- a tuple (f, args) , where f takes the retry number as the first argument, followed by the additional args.
The function needs to return the desired retry interval in seconds, or raise StopRetry to stop retrying. The following built-in functions can be passed for common scenarios and return the appropriate tuple:
fixed(delay, max_retries)
Returns a method that returns the given delay (in seconds) or raises StopRetry if the number of retries exceeds max_retries .
linear(delay, increment, max_retries)
Like fixed , but starts off with the given delay and increments it by the given increment after every retry.
exponential(delay, factor, max_retries)
Like fixed , but starts off with the given delay and multiplies it by the given factor after every retry.
For example, to retry a task 3 times (for a total of 4 executions), and wait 60 seconds between executions, pass retry_method=fixed(60, 3) .
runner_class
If given, a Python class can be specified to influence task running behavior. The runner class should inherit tasktiger.runner.BaseRunner and implement the task execution behavior. The default implementation is available in tasktiger.runner.DefaultRunner . The following behavior can be achieved:
Execute specific code before or after the task is executed (in the forked child process), or customize the way task functions are called in either single or batch processing.
Note that if you want to execute specific code for all tasks, you should use the CHILD_CONTEXT_MANAGERS configuration option.
Control the hard timeout behavior of a task.
Execute specific code in the main worker process after a task failed permanently.
This is an advanced feature and the interface and requirements of the runner class can change in future TaskTiger versions.
The following options can be only specified in the task decorator:
If set to True , the task will receive a list of dicts with args and kwargs and can process multiple tasks of the same type at once. Example: [{"args": [1], "kwargs": {}}, {"args": [2], "kwargs": {}}] Note that the list will only contain multiple items if the worker has set up BATCH_QUEUES for the specific queue (see the Configuration section).
If given, makes a task execute periodically. Pass either:
- a function that takes the current datetime as an argument.
- a tuple (f, args) , where f takes the current datetime as the first argument, followed by the additional args.
The schedule function must return the next task execution datetime, or None to prevent periodic execution. The function is executed to determine the initial task execution date when a worker is initialized, and to determine the next execution date when the task is about to get executed.
For most common scenarios, the below mentioned built-in functions can be passed:
periodic(seconds=0, minutes=0, hours=0, days=0, weeks=0, start_date=None, end_date=None)
Use equal, periodic intervals, starting from start_date (defaults to 2000-01-01T00:00Z , a Saturday, if not given), ending at end_date (or never, if not given). For example, to run a task every five minutes indefinitely, use schedule=periodic(minutes=5) . To run a task every every Sunday at 4am UTC, you could use schedule=periodic(weeks=1, start_date=datetime.datetime(2000, 1, 2, 4)) .
cron_expr(expr, start_date=None, end_date=None)
start_date , to specify the periodic task start date. It defaults to 2000-01-01T00:00Z , a Saturday, if not given. end_date , to specify the periodic task end date. The task repeats forever if end_date is not given. For example, to run a task every hour indefinitely, use schedule=cron_expr("0 * * * *") . To run a task every Sunday at 4am UTC, you could use schedule=cron_expr("0 4 * * 0") .
In some cases the task retry options may not be flexible enough. For example, you might want to use a different retry method depending on the exception type, or you might want to like to suppress logging an error if a task fails after retries. In these cases, RetryException can be raised within the task function. The following options are supported:
Specify a custom retry method for this retry. If not given, the task's default retry method is used, or, if unspecified, the configured DEFAULT_RETRY_METHOD . Note that the number of retries passed to the retry method is always the total number of times this method has been executed, regardless of which retry method was used.
original_traceback
If RetryException is raised from within an except block and original_traceback is True, the original traceback will be logged (i.e. the stacktrace at the place where the caught exception was raised). False by default.
If set to False and the task fails permanently, a warning will be logged instead of an error, and the task will be removed from Redis when it completes. True by default.
Example usage:
The tasktiger command is used on the command line to invoke a worker. To invoke multiple workers, multiple instances need to be started. This can be easily done e.g. via Supervisor. The following Supervisor configuration file can be placed in /etc/supervisor/tasktiger.ini and runs 4 TaskTiger workers as the ubuntu user. For more information, read Supervisor's documentation.
Workers support the following options:
-q , --queues
If specified, only the given queue(s) are processed. Multiple queues can be separated by comma. Any subqueues of the given queues will be also processed. For example, -q first,second will process items from first , second , and subqueues such as first.CUSTOMER1 , first.CUSTOMER2 .
-e , --exclude-queues
If specified, exclude the given queue(s) from processing. Multiple queues can be separated by comma. Any subqueues of the given queues will also be excluded unless a more specific queue is specified with the -q option. For example, -q email,email.incoming.CUSTOMER1 -e email.incoming will process items from the email queue and subqueues like email.outgoing.CUSTOMER1 or email.incoming.CUSTOMER1 , but not email.incoming or email.incoming.CUSTOMER2 .
-m , --module
Module(s) to import when launching the worker. This improves task performance since the module doesn't have to be reimported every time a task is forked. Multiple modules can be separated by comma.
Another way to preload modules is to set up a custom TaskTiger launch script, which is described below.
-h , --host
Redis server hostname (if different from localhost ).
-p , --port
Redis server port (if different from 6379 ).
-a , --password
Redis server password (if required).
Redis server database number (if different from 0 ).
-M , --max-workers-per-queue
Maximum number of workers that are allowed to process a queue.
--store-tracebacks/--no-store-tracebacks
Store tracebacks with execution history (config defaults to True ).
Can be fork (default) or sync . Whether to execute tasks in a separate process via fork, or execute them synchronously in the same proces. See "Features" section for the benefits of either approach.
--exit-after
Exit the worker after the time in minutes has elapsed. This is mainly useful with the synchronous executor to prevent memory leaks from accumulating.
In some cases it is convenient to have a custom TaskTiger launch script. For example, your application may have a manage.py command that sets up the environment and you may want to launch TaskTiger workers using that script. To do that, you can use the run_worker_with_args method, which launches a TaskTiger worker and parses any command line arguments. Here is an example:
TaskTiger provides access to the Task class which lets you inspect queues and perform various actions on tasks.
Each queue can have tasks in the following states:
- queued : Tasks that are queued and waiting to be picked up by the workers.
- active : Tasks that are currently being processed by the workers.
- scheduled : Tasks that are scheduled for later execution.
- error : Tasks that failed with an error.
To get a list of all tasks for a given queue and state, use Task.tasks_from_queue . The method gives you back a tuple containing the total number of tasks in the queue (useful if the tasks are truncated) and a list of tasks in the queue, latest first. Using the skip and limit keyword arguments, you can fetch arbitrary slices of the queue. If you know the task ID, you can fetch a given task using Task.from_id . Both methods let you load tracebacks from failed task executions using the load_executions keyword argument, which accepts an integer indicating how many executions should be loaded.
Tasks can also be constructed and queued using the regular constructor, which takes the TaskTiger instance, the function name and the options described in the Task options section. The task can then be queued using its delay method. Note that the when argument needs to be passed to the delay method, if applicable. Unique tasks can be reconstructed using the same arguments.
The Task object has the following properties:
- id : The task ID.
- data : The raw data as a dict from Redis.
- executions : A list of failed task executions (as dicts). An execution dict contains the processing time in time_started and time_failed , the worker host in host , the exception name in exception_name and the full traceback in traceback .
- serialized_func , args , kwargs : The serialized function name with all of its arguments.
- func : The imported (executable) function
The Task object has the following methods:
- cancel : Cancel a scheduled task.
- delay : Queue the task for execution.
- delete : Remove the task from the error queue.
- execute : Run the task without queueing it.
- n_executions : Queries and returns the number of past task executions.
- retry : Requeue the task from the error queue for execution.
- update_scheduled_time : Updates a scheduled task's date to the given date.
The current task can be accessed within the task function while it's being executed: In case of a non-batch task, the current_task property of the TaskTiger instance returns the current Task instance. In case of a batch task the current_tasks property must be used which returns a list of tasks that are currently being processed (in the same order as they were passed to the task).
Example 1: Queueing a unique task and canceling it without a reference to the original task.
Example 2: Inspecting queues and retrying a task by ID.
Example 3: Accessing the task instances within a batch task function to determine how many times the currently processing tasks were previously executed.
The --max-workers-per-queue option uses queue locks to control the number of workers that can simultaneously process the same queue. When using this option a system lock can be placed on a queue which will keep workers from processing tasks from that queue until it expires. Use the set_queue_system_lock() method of the TaskTiger object to set this lock.
TaskTiger comes with Rollbar integration for error handling. When a task errors out, it can be logged to Rollbar, grouped by queue, task function name and exception type. To enable logging, initialize rollbar with the StructlogRollbarHandler provided in the tasktiger.rollbar module. The handler takes a string as an argument which is used to prefix all the messages reported to Rollbar. Here is a custom worker launch script:
Error'd tasks occasionally need to be purged from Redis, so TaskTiger exposes a purge_errored_tasks method to help. It might be useful to set this up as a periodic task as follows:
Tests can be run locally using the provided docker compose file. After installing docker, tests should be runnable with:
Tests can be more granularly run using normal pytest flags. For example:
- Make sure the code has been thoroughly reviewed and tested in a realistic production environment.
- Update setup.py and CHANGELOG.md . Make sure you include any breaking changes.
- Run python setup.py sdist and twine upload dist/<PACKAGE_TO_UPLOAD> .
- Push a new tag pointing to the released commit, format: v0.13 for example.
- Mark the tag as a release in GitHub's UI and include in the description the changelog entry for the version. An example would be: https://github.com/closeio/tasktiger/releases/tag/v0.13 .
Releases 17
Contributors 30.
- Python 98.2%
- Dockerfile 0.1%
How to Run Your First Task with RQ, Redis, and Python
Time to read: 7 minutes
- Facebook logo
- Twitter Logo Follow us on Twitter
- LinkedIn logo
As a developer, it can be very useful to learn how to run functions in the background while being able to monitor the queue in another tab or different system. This is incredibly helpful when managing heavy workloads that might not work efficiently when called all at once, or when making large numbers of calls to a database that returns data slowly over time rather than all at once.
In this tutorial we will implement a RQ queue in Python with the help of Redis to schedule and execute tasks in a timely manner.
Tutorial Requirements
- Python 3.6 or newer. If your operating system does not provide a Python interpreter, you can go to python.org to download an installer.
Let’s talk about task queues
Task queues are a great way to allow tasks to work asynchronously outside of the main application flow. There are many task queues in Python to assist you in your project, however, we’ll be discussing a solution today known as RQ.
RQ, also known as Redis Queue , is a Python library that allows developers to enqueue jobs to be processed in the background with workers . The RQ workers will be called when it's time to execute the queue in the background. Using a connection to Redis , it’s no surprise that this library is super lightweight and offers support for those getting started for the first time.
By using this particular task queue, it is possible to process jobs in the background with little to no hassle.
Set up the environment
Create a project directory in your terminal called “rq-test” to follow along.
Install a virtual environment and copy and paste the commands to install rq and related packages. If you are using a Unix or MacOS system, enter the following commands:
If you are on a Windows machine, enter the following commands in a prompt window:
RQ requires a Redis installation on your machine which can be done using the following commands using wget . Redis is on version 6.0.6 at the time of this article publication.
If you are using a Unix or MacOS system, enter these commands to install Redis. This is my personal favorite way to install Redis, but there are alternatives below:
If you have Homebrew installed, you can type brew install redis in the terminal and refer to this GitHub gist to install Redis on the Mac . For developers using Ubuntu Linux, the command sudo apt-get install redis would get the job done as well.
Run the Redis server in a separate terminal window on the default port with the command src/redis-server from the directory where it's installed.
For Windows users, you would have to follow a separate tutorial to run Redis on Windows . Download the latest zip file on GitHub and extract the contents. Run the redis-server.exe file that was extracted from the zip file to start the Redis server.
The output should look similar to the following after running Redis:
Build out the tasks
In this case, a task for Redis Queue is merely a Python function. For this article, we’ll tell the task to print a message to the terminal for a “x” amount of seconds to demonstrate the use of RQ.
Copy and paste the following code to a file named “tasks.py” in your directory.
These are simple tasks that print out numbers and text on the terminal so that we can see if the tasks are executed properly. Using the time.sleep(1) function from the Python time library will allow your task to be suspended for the given number of seconds and overall extend the time of the task so that we can examine their progress.
Feel free to alter this code after the tutorial and create your own tasks. Some other popular tasks are sending a fax message or email by connecting to your email client.
Create your queue
Create another file in the root directory and name it “app.py”. Copy and paste the following code:
The queue object sets up a connection to Redis and initializes a queue based on that connection. This queue can hold all the jobs required to run in the background with workers.
As seen in the code, the tasks.print_task function is added using the enqueue function. This means that the task added to the queue will be executed immediately
The enqueue_in function is another nifty RQ function because it expects a timedelta in order to schedule the specified job. In this case, seconds is specified, but this variable can be changed according to the time schedule expected for your usage. Check out other ways to schedule a job on this GitHub README.
Since we are testing out the RQ queue, I have enqueued both the tasks.print_task and tasks.print_numbers functions so that we can see their output on the terminal. The third argument passed in is a "5" which also stands for the argument passed into the respective functions. In this case, we are expecting to see print_task() print "Hello World!" five times and for print_numbers() to print 5 numbers in order.
If you have created any additional task, be sure to import your tasks at the top of the file so that all the tasks in your Python file can be accessed.
Run the queue
For the purposes of this article, the gif demo below will show a perfect execution of the tasks in queue so no exceptions will be raised.
The Redis server should still be running in a tab from earlier in the tutorial at this point. If it stopped, run the command src/redis-server inside the redis-6.0.6 folder on one tab, or for developers with a Windows machine, start redis-cli.exe . Open another tab solely to run the RQ scheduler with the command rq worker --with-scheduler .
This should be the output after running the command above.
The worker command activated a worker process in order to connect to Redis and look for any jobs assigned to the queue from the code in app.py .
Lastly, open a third tab in the terminal for the root project directory. Start up the virtual environment again with the command source venv/bin/activate . Then type python app.py to run the project.
Go back to the tab that is running rq worker --with-scheduler . Wait 5 more seconds after the first task is executed to see the next task. Although the live demo gif below wasn’t able to capture the best timing due to having to run the program and record, it is noticeable that there was a pause between tasks until execution and that both tasks were completed within 15 seconds.
Here’s the sample output inside of the rqworker tab:
As seen in the output above, if the tasks written in task.py had a line to return anything, then the result of both tasks are kept for 500 seconds which is the default. A developer can alter the return value's time to live by passing in a result_ttl parameter when adding tasks to the queue.
Handle exceptions and try again
If a job were to fail, you can always set up a log to keep track of the error messages, or you can use the RQ queue to enqueue and retry failed jobs. By using RQ's FailedJobRegistry package, you can keep track of the jobs that failed during runtime. The RQ documentation discusses how it handles the exceptions and how data regarding the job can help the developer figure out how to resubmit the job.
However, RQ also supports developers in handling exceptions in their own way by injecting your own logic to the rq workers . This may be a helpful option for you if you are executing many tasks in your project and those that failed are not worth retrying.
Force a failed task to retry
Since this is an introductory article to run your first task with RQ, let's try to purposely fail one of the tasks from earlier to test out RQ's retry object.
Go to the tasks.py file and alter the print_task() function so that random numbers can be generated and determine if the function will be executed or not. We will be using the random Python library to assist us in generating numbers. Don't forget to include the import random at the top of the file.
Copy and paste the following lines of code to change the print_task() function in the tasks.py file.
Go back to the app.py file to change the queue. Instead of using the enqueue_in function to execute the tasks.print_task function, delete the line and replace it with queue.enqueue(tasks.print_task, 5, retry=Retry(max=2)) .
The retry object is imported with rq so make sure you add from rq import Retry at the top of the file as well in order to use this functionality. This object accepts max and interval arguments to specify when the particular function will be retried. In the newly changed line, the tasks.print_task function will pass in the function we want to retry, the argument parameter "5" which stands for the seconds of execution, and lastly the maximum amount of times we want the queue to retry.
The tasks in queue should now look like this:
When running the print_task task, there is a 50/50 chance that tasks.print_task() will execute properly since we're only generating a 1 or 2, and the print statement will only happen if you generate a 1. A RuntimeError will be raised otherwise and the queue will retry the task immediately as many times as it takes to successfully print "Hello World!".
What’s next for task queues?
Congratulations! You have successfully learned and implemented the basics of scheduling tasks in the RQ queue. Perhaps now you can tell the worker command to add a task that prints out an infinite number of "Congratulations" messages in a timely manner!
Otherwise, check out these different tasks that you can build in to your Redis Queue:
- Schedule Twilio SMS to a list of contacts quickly!
- Use Redis Queue to generate a fan fiction with OpenAI GPT-3
- Queue Emails with Twilio SendGrid using Redis Queue
Let me know what you have been building by reaching out to me over email!
Diane Phan is a developer on the Developer Voices team. She loves to help programmers tackle difficult challenges that might prevent them from bringing their projects to life. She can be reached at dphan [at] twilio.com or LinkedIn .
Related Posts

Related Resources
Twilio docs, from apis to sdks to sample apps.
API reference documentation, SDKs, helper libraries, quickstarts, and tutorials for your language and platform.
Resource Center
The latest ebooks, industry reports, and webinars.
Learn from customer engagement experts to improve your own communication.
Twilio's developer community hub
Best practices, code samples, and inspiration to build communications and digital engagement experiences.
Celery is a task queue implementation for Python web applications used to asynchronously execute work outside the HTTP request-response cycle.

Why is Celery useful?
Task queues and the Celery implementation in particular are one of the trickier parts of a Python web application stack to understand.
If you are a junior developer it can be unclear why moving work outside the HTTP request-response cycle is important. In short, you want your WSGI server to respond to incoming requests as quickly as possible because each request ties up a worker process until the response is finished. Moving work off those workers by spinning up asynchronous jobs as tasks in a queue is a straightforward way to improve WSGI server response times.
What's the difference between Celeryd and Celerybeat?
Celery can be used to run batch jobs in the background on a regular schedule. A key concept in Celery is the difference between the Celery daemon (celeryd), which executes tasks, Celerybeat, which is a scheduler. Think of Celeryd as a tunnel-vision set of one or more workers that handle whatever tasks you put in front of them. Each worker will perform a task and when the task is completed will pick up the next one. The cycle will repeat continously, only waiting idly when there are no more tasks to put in front of them.
Celerybeat on the other hand is like a boss who keeps track of when tasks should be executed. Your application can tell Celerybeat to execute a task at time intervals, such as every 5 seconds or once a week. Celerybeat can also be instructed to run tasks on a specific date or time, such as 5:03pm every Sunday. When the interval or specific time is hit, Celerybeat will hand the job over to Celeryd to execute on the next available worker.
Celery tutorials and advice
Celery is a powerful tool that can be difficult to wrap your mind around at first. Be sure to read up on task queue concepts then dive into these specific Celery tutorials.
A 4 Minute Intro to Celery is a short introductory task queue screencast.
This blog post series on Celery's architecture , Celery in the wild: tips and tricks to run async tasks in the real world and dealing with resource-consuming tasks on Celery provide great context for how Celery works and how to handle some of the trickier bits to working with the task queue.
How to use Celery with RabbitMQ is a detailed walkthrough for using these tools on an Ubuntu VPS.
Celery - Best Practices explains things you should not do with Celery and shows some underused features for making task queues easier to work with.
Celery Best Practices is a different author's follow up to the above best practices post that builds upon some of his own learnings from 3+ years using Celery.
Common Issues Using Celery (And Other Task Queues) contains good advice about mistakes to avoid in your task configurations, such as database transaction usage and retrying failed tasks.
Asynchronous Processing in Web Applications Part One and Part Two are great reads for understanding the difference between a task queue and why you shouldn't use your database as one.
My Experiences With A Long-Running Celery-Based Microprocess gives some good tips and advice based on experience with Celery workers that take a long time to complete their jobs.
Checklist to build great Celery async tasks is a site specifically designed to give you a list of good practices to follow as you design your task queue configuration and deploy to development, staging and production environments.
Heroku wrote about how to secure Celery when tasks are otherwise sent over unencrypted networks.
Unit testing Celery tasks explains three strategies for testing code within functions that Celery executes. The post concludes that calling Celery tasks synchronously to test them is the best strategy without any downsides. However, keep in mind that any testing method that is not the same as how the function will execute in a production environment can potentially lead to overlooked bugs. There is also an open source Git repository with all of the source code from the post.
Rollbar monitoring of Celery in a Django app explains how to use Rollbar to monitor tasks. Super useful when workers invariably die for no apparent reason.
3 Gotchas for Working with Celery are things to keep in mind when you're new to the Celery task queue implementation.
Dask and Celery compares Dask.distributed with Celery for Python projects. The post gives code examples to show how to execute tasks with either task queue.
Python+Celery: Chaining jobs? explains that Celery tasks should be dependent upon each other using Celery chains, not direct dependencies between tasks.
Celery with web frameworks
Celery is typically used with a web framework such as Django , Flask or Pyramid . These resources show you how to integrate the Celery task queue with the web framework of your choice.
How to Use Celery and RabbitMQ with Django is a great tutorial that shows how to both install and set up a basic task with Django.
Miguel Grinberg wrote a nice post on using the task queue Celery with Flask . He gives an overview of Celery followed by specific code to set up the task queue and integrate it with Flask.
Setting up an asynchronous task queue for Django using Celery and Redis is a straightforward tutorial for setting up the Celery task queue for Django web applications using the Redis broker on the back end.
A Guide to Sending Scheduled Reports Via Email Using Django And Celery shows you how to use django-celery in your application. Note however there are other ways of integrating Celery with Django that do not require the django-celery dependency.
Flask asynchronous background tasks with Celery and Redis combines Celery with Redis as the broker and Flask for the example application's framework.
Celery and Django and Docker: Oh My! shows how to create Celery tasks for Django within a Docker container. It also provides some
Asynchronous Tasks With Django and Celery shows how to integrate Celery with Django and create Periodic Tasks.
Getting Started Scheduling Tasks with Celery is a detailed walkthrough for setting up Celery with Django (although Celery can also be used without a problem with other frameworks).
Asynchronous Tasks with Falcon and Celery configures Celery with the Falcon framework, which is less commonly-used in web tutorials.
Custom Celery task states is an advanced post on creating custom states, which is especially useful for transient states in your application that are not covered by the default Celery configuration.
Asynchronous Tasks with Django and Celery looks at how to configure Celery to handle long-running tasks in a Django app.
Celery deployment resources
Celery and its broker run separately from your web and WSGI servers so it adds some additional complexity to your deployments . The following resources walk you through how to handle deployments and get the right configuration settings in place.
- How to run celery as a daemon? is a short post with the minimal code for running the Celery daemon and Celerybeat as system services on Linux.
Do you want to learn more about task queues, or another topic?
How do I execute code outside the HTTP request-response cycle?
I've built a Python web app, now how do I deploy it?
What tools exist for monitoring a deployed web app?
Table of Contents
Full stack python.
- Skip to main content
- Skip to primary sidebar
- Skip to footer
Additional menu

Super Fast Python
making you awesome at concurrency
Queue task_done() and join() in Python
April 14, 2022 by Jason Brownlee in Python Threading
Last Updated on September 12, 2022
You can mark queue tasks done via task_done() and be notified when all tasks are done via join() .
In this tutorial you will discover how to use queue task done and join in Python .
Let’s get started.
Table of Contents
Need To Know When All Tasks are Done
A thread is a thread of execution in a computer program.
Every Python program has at least one thread of execution called the main thread. Both processes and threads are created and managed by the underlying operating system.
Sometimes we may need to create additional threads in our program in order to execute code concurrently.
Python provides the ability to create and manage new threads via the threading module and the threading.Thread class .
You can learn more about Python threads in the guide:
- Threading in Python: The Complete Guide
Threads can share data with each other using thread-safe queues, such as the queue.Queue class .
A problem when using queues is knowing when all items in the queue have been processed by consumer threads.
How can we know when all items have been processed in a queue?
Run loops using all CPUs, download your FREE book to learn how.
Why Care When All Tasks Are Done
There are many reasons why a thread may want to know when all tasks in a queue have been processed.
For example:
- A producer thread may want to wait until all work is done before adding new work.
- A producer thread may want to wait for all tasks to be done before sending a shutdown signal.
- A main thread may want to wait for all tasks to be done before terminating the program.
There are two aspects to this, they are:
- A thread blocking until tasks are done.
- A task being done is more than being retrieved from the queue.
Specifically, waiting means that the thread is blocked until the condition is met.
The condition of all tasks being processed is not only the case that all items put on the queue have been retrieved, but have been processed by the thread that retrieved them.
Next, let’s look at how we might do this in Python.
Download Now: Free Threading PDF Cheat Sheet
How to Know When All Tasks Are Done
Python provides thread-safe queue data structures in the queue module, such as the queue.Queue , queue.LifoQueue and queue.PriorityQueue classes.
Objects can be added to the queue via calls to Queue.put() and removed from the queue via calls to Queue.get() .
Thread-safe means that multiple threads may put and get items from the queue concurrently without fear of a race condition or corruption of the internal data structure.
A thread can block and be notified when all current items or tasks on the queue are done by calling the Queue.join() function .
| .. .join() |
Block means that the calling thread will wait until the condition is met, specifically that all tasks are done. The Queue.join() function will not return until then.
Notified means that the blocked thread will be woken up and allowed to proceed when all tasks are done. This means that the join() function will return at this time allowing the thread to continue on with the next instructions.
Multiple different threads may join the queue and await the state that all tasks are marked done.
If there are no tasks in the queue, e.g. the queue is empty, then the join() function will return immediately.
The count of unfinished tasks goes up whenever an item is added to the queue. The count goes down whenever a consumer thread calls task_done() to indicate that the item was retrieved and all work on it is complete. When the count of unfinished tasks drops to zero, join() unblocks. — queue — A synchronized queue class
The Queue.join() function only works if threads retrieving items or tasks from the queue via Queue.get() also call the Queue.task_done() function .
| .. = queue.get() .task_done() |
The Queue.task_done() function is called by the consumer thread (e.g. the thread that calls Queue.get() ) only after the thread has finished processing the task retrieved from the queue.
This will be application specific, but is more than simply retrieving the task from the queue.
Indicate that a formerly enqueued task is complete. Used by queue consumer threads. For each get() used to fetch a task, a subsequent call to task_done() tells the queue that the processing on the task is complete. — queue — A synchronized queue class
If there are multiple consumer threads, then for join() to function correctly, each consumer thread must mark tasks as done.
If processing the task may fail with an unexpected Error or Exception , it is a good practice to wrap the processing of the task in a try-finally pattern.
| .. = queue.get() : # process the item # ... : # mark the task as done or processed queue.task_done() |
This ensures that the task is marked done in the queue, even if processing the task fails.
In turn, it allows any threads blocked by calling Queue.join() to be appropriately notified when all items are retrieved from the queue, avoiding a possible deadlock concurrency failure mode.
Now that we are familiar with the Queue.task_done() and Queue.join() functions, let’s look at some worked examples.
Free Python Threading Course
Download your FREE threading PDF cheat sheet and get BONUS access to my free 7-day crash course on the threading API.
Discover how to use the Python threading module including how to create and start new threads and how to use a mutex locks and semaphores
Learn more
Example of Queue Join and Task Done
We can explore an example of how to use join() and task_done() .
In this example we will have a producer thread that will add ten tasks to the queue and then signal that no further tasks are to be expected. The consumer thread will get the tasks, process them and mark them as done. When the signal to exit is received, the consumer thread will terminate. The main thread will wait for the producer thread to add all items to the queue, and will wait for all items on the queue to be processed before moving on.
Let’s dive in.
Producer Thread
First, we can define the function to be executed by the producer thread.
The task will iterate ten times in a loop.
| .. ('Producer starting') i in range(10): # ... |
Each iteration, it will generate a new random value between 0 and 1 via the random.random() function. It will then pair the generated value with an integer timestamp from 0 to 9 into a tuple and put the value on the queue.
| .. = (i, random()) (f'.producer added {task}') .put(task) |
Finally, the producer will put the value None on the queue to signal to the consumer that there are no further tasks.
This is called a Sentinel Value and is a common way for threads to communicate via queues to signal an important event, like a shutdown.
| .. .put(None) ('Producer finished') |
The producer() function below implements this by taking the queue instance as an argument.
| producer(queue): print('Producer starting') # add tasks to the queue for i in range(10): # generate a task task = (i, random()) print(f'.producer added {task}') # add it to the queue queue.put(task) # send a signal that no further tasks are coming queue.put(None) print('Producer finished') |
Consumer Thread
Next, we can define the function to be executed by the consumer thread.
The consumer thread will loop forever.
| .. ('Consumer starting') True: # ... |
Each iteration, it will get an item from the queue and block if there is no item yet available.
| .. = queue.get() |
If the item retrieved from the queue is the value None , then the task will break the loop and terminate the thread.
| .. task is None: break |
Otherwise, the fractional value is used to block with a call to time.sleep() and is then reported. The item is then marked as processed via a call to task_done() .
| .. (task[1]) (f'.consumer got {task}') .task_done() |
Finally, just prior to the thread exiting, it will mark the signal to terminate as processed.
| .. .task_done() ('Consumer finished') |
The consumer() function below implements this and takes the queue instance as an argument.
| consumer(queue): print('Consumer starting') # process items from the queue while True: # get a task from the queue task = queue.get() # check for signal that we are done if task is None: break # process the item sleep(task[1]) print(f'.consumer got {task}') # mark the unit of work as processed queue.task_done() # mark the signal as processed queue.task_done() print('Consumer finished') |
Create Queue and Threads
In the main thread we can create the shared queue instance.
| .. = Queue() |
Then we can configure and start the producer thread, which will generate tasks and add them to the queue for the consumer to retrieve.
| .. = Thread(target=producer, args=(queue,)) .start() |
We can then configure and start the consumer thread, which will patiently wait for work to arrive on the queue.
| .. = Thread(target=consumer, args=(queue,)) .start() |
The main thread will then block until the producer thread has added all work to the queue and the thread has terminated.
| .. .join() ('Main found that the producer has finished') |
The main thread will then block on the queue with a call to join() until the consumer has retrieved all values from the queue and processed them appropriately. This includes the final signal that there are no further task items to process.
| .. .join() ('Main found that all tasks are processed') |
It is important that the main thread blocks on the producer thread first, before blocking on the queue. This is to avoid a possible race condition.
For example, if the main thread blocked on the queue directly, it is possible that at that time for the queue to be empty, in which case the call would return immediately. Alternatively, it may join at a time when there are only a few tasks on the queue, they are consumed by the consumer thread and the join call returns.
The problem is that in both of these cases, we don’t know if the call to join returned because all tasks were marked done or just a subset of tasks that had been added to the queue at the time join was called.
By waiting for the producer thread to terminate first, we know that all tasks that could be added to the queue have been added to the queue. By blocking on the queue after the producer has finished, we know that when the call to join returns, that all tasks were added to the queue, all tasks were retrieved from the queue and all retrieved tasks were marked as done.
Complete Example
Tying this together, the complete example is listed below.
| time import sleep random import random queue import Queue threading import Thread producer(queue): print('Producer starting') # add tasks to the queue for i in range(10): # generate a task task = (i, random()) print(f'.producer added {task}') # add it to the queue queue.put(task) # send a signal that no further tasks are coming queue.put(None) print('Producer finished') consumer(queue): print('Consumer starting') # process items from the queue while True: # get a task from the queue task = queue.get() # check for signal that we are done if task is None: break # process the item sleep(task[1]) print(f'.consumer got {task}') # mark the unit of work as processed queue.task_done() # mark the signal as processed queue.task_done() print('Consumer finished') = Queue() = Thread(target=producer, args=(queue,)) .start() = Thread(target=consumer, args=(queue,)) .start() .join() ('Main found that the producer has finished') .join() ('Main found that all tasks are processed') |
Running the example first creates the queue to be shared between the producer and consumer threads.
Then the producer thread is created and configured to execute our producer() function and passed in the shared queue instance. The producer thread is then started.
Next, the consumer thread is configured to execute our consumer() function and is then started.
The producer thread runs as fast as it is able, each iteration generating a random number and adding it along with the task number to the queue. Once all ten tasks have been added to the queue, a None message is sent to the queue to indicate no further messages are to be expected and the producer thread terminates.
The main thread notices that the producer thread has terminated, then blocks on the queue itself waiting for all tasks to be retrieved and marked as done.
The consumer thread retrieves tasks one at a time from the queue, blocks and reports their value, then marks the task as done. This is repeated until the sentinel message is received and the loop is broken. Just before the consumer thread is terminated, the final sentinel message is marked as done.
The main thread notices that all tasks were marked done and is then free to continue on with other tasks. In this case, the main thread reports a message and terminates.
A sample of the output from the program is listed below. Note, your specific results will differ given the use of random numbers.
In this case, we can see that the producer ran first, adding all tasks to the queue. Then the consumer thread ran, reading off each value. After all tasks are marked done, finally the main thread continues on.
This highlights how to use task_done() and join() on a thread queue.
Next, let’s look at what happens if all tasks are already marked as done on the queue.
Overwhelmed by the python concurrency APIs? Find relief, download my FREE Python Concurrency Mind Maps
Example of Join When All Tasks Are Already Done
If all tasks on the thread queue have been marked as done, then any call to join() will return immediately.
This can happen if the queue is empty, for example no tasks were added to the queue.
| .. = Queue() .join() # returns immediately |
This can also happen if tasks were added to the queue, then retrieved and marked done and no further tasks were added.
We can update the example from the previous section to demonstrate this case.
Specifically, after the main thread is notified that all tasks were marked as done by the consumer thread, it can then attempt to join the queue again.
| .. .join() ('Tried joining again') |
| time import sleep random import random queue import Queue threading import Thread producer(queue): print('Producer starting') # add tasks to the queue for i in range(10): # generate a task task = (i, random()) print(f'.producer added {task}') # add it to the queue queue.put(task) # send a signal that no further tasks are coming queue.put(None) print('Producer finished') consumer(queue): print('Consumer starting') # process items from the queue while True: # get a task from the queue task = queue.get() # check for signal that we are done if task is None: break # process the item sleep(task[1]) print(f'.consumer got {task}') # mark the unit of work as processed queue.task_done() # mark the signal as processed queue.task_done() print('Consumer finished') = Queue() = Thread(target=producer, args=(queue,)) .start() = Thread(target=consumer, args=(queue,)) .start() .join() ('Main found that the producer has finished') .join() ('Main found that all tasks are processed') .join() ('Tried joining again') |
Running the example creates the shared queue, then creates and starts the producer and consumer threads.
The producer thread puts ten tasks to the queue, then the sentinel message. The consumer thread gets the ten tasks and marks each as done, then gets the sentinel message and marks it as done.
The main thread is then notified that all tasks on the queue are done.
The main thread then attempts to block on the queue again until all tasks are done. There are no tasks on the queue, therefore the call to join() returns immediately.
This example highlights that a call to join() will only block if there is at least one task that has not been marked as done.
Next, let’s look at what happens if we call the task_done() function too many times.

Loving The Tutorials?
Why not take the next step? Get the book.
Example of Too Many Calls to Task Done
The task_done() function may be called more times than there are tasks on the queue.
This will result in a ValueError being raised.
This can happen if task_done() is called when there are no items in the queue.
| .. = Queue() .task_done() |
It can also happen if all tasks in the queue have been retrieved and marked as done.
We can update the above example to demonstrate this case.
Consider if the consumer thread marked the sentinel message as done just prior to breaking the loop, and again after the loop.
| .. task is None: # mark the signal as processed queue.task_done() break .. .task_done() |
This would be one too many calls to task_done() compared to tasks on the queue and will result in a ValueError .
The updated version of the consumer() function with this change is listed below.
| consumer(queue): print('Consumer starting') # process items from the queue while True: # get a task from the queue task = queue.get() # check for signal that we are done if task is None: # mark the signal as processed queue.task_done() break # process the item sleep(task[1]) print(f'.consumer got {task}') # mark the unit of work as processed queue.task_done() # mark the signal as processed queue.task_done() print('Consumer finished') |
| time import sleep random import random queue import Queue threading import Thread producer(queue): print('Producer starting') # add tasks to the queue for i in range(10): # generate a task task = (i, random()) print(f'.producer added {task}') # add it to the queue queue.put(task) # send a signal that no further tasks are coming queue.put(None) print('Producer finished') consumer(queue): print('Consumer starting') # process items from the queue while True: # get a task from the queue task = queue.get() # check for signal that we are done if task is None: # mark the signal as processed queue.task_done() break # process the item sleep(task[1]) print(f'.consumer got {task}') # mark the unit of work as processed queue.task_done() # mark the signal as processed queue.task_done() print('Consumer finished') = Queue() = Thread(target=producer, args=(queue,)) .start() = Thread(target=consumer, args=(queue,)) .start() .join() ('Main found that the producer has finished') .join() ('Main found that all tasks are processed') |
The producer thread puts ten tasks to the queue, then the sentinel message.
The consumer thread gets the ten tasks and marks each as done, then gets the sentinel message and marks it as done.
The main thread is then notified that all tasks on the queue are done as per normal.
The consumer thread breaks the loop, then marks the sentinel message as done again. This causes a ValueError to be raised, which unravels the stack and ultimately terminates consumer thread.
The program achieves the desired outcome, but the consumer thread does not terminate normally.
This example highlights what happens if too many calls are made to the task_done() function.
Next, let’s look at an example of a deadlock caused by too few calls to the task_done() function.
Example of Join Deadlock Due to Missed Task Done
A deadlock may result if there is at least one thread waiting on the queue via a call to join() and too few calls are made to the task_done() function.
This can happen if an Error or Exception is raised by a consumer thread while processing a task. For example, between a call to get() and the call to task_done() on the queue.
Consider the loop in consumer() function. We can contrive a case where if a task has the identifier of five, to raise an exception.
| .. task[0] == 5: raise Exception('Something bad happened') |
An exception raised at this point will cause this item on the queue to not have the task_done() function called.
Additionally, any items not retrieved from the queue will remain on the queue and will also not be marked as task_done() .
| consumer(queue): print('Consumer starting') # process items from the queue while True: # get a task from the queue task = queue.get() # check for signal that we are done if task is None: break # process the item sleep(task[1]) print(f'.consumer got {task}') # check for a failure case if task[0] == 5: raise Exception('Something bad happened') # mark the unit of work as processed queue.task_done() # mark the signal as processed queue.task_done() print('Consumer finished') |
The exception will cause the consumer thread to unravel the stack and to terminate. The result will be that the main thread will block and wait forever on the queue as the remaining tasks will never be marked done.
This is a deadlock and the program must be terminated forcefully, such as via Control-C.
| time import sleep random import random queue import Queue threading import Thread producer(queue): print('Producer starting') # add tasks to the queue for i in range(10): # generate a task task = (i, random()) print(f'.producer added {task}') # add it to the queue queue.put(task) # send a signal that no further tasks are coming queue.put(None) print('Producer finished') consumer(queue): print('Consumer starting') # process items from the queue while True: # get a task from the queue task = queue.get() # check for signal that we are done if task is None: break # process the item sleep(task[1]) print(f'.consumer got {task}') # check for a failure case if task[0] == 5: raise Exception('Something bad happened') # mark the unit of work as processed queue.task_done() # mark the signal as processed queue.task_done() print('Consumer finished') = Queue() = Thread(target=producer, args=(queue,)) .start() = Thread(target=consumer, args=(queue,)) .start() .join() ('Main found that the producer has finished') .join() ('Main found that all tasks are processed') |
The consumer thread gets the ten tasks and marks each as done. When a task is retrieved that has an integer value of 5, the Exception is triggered and the thread is terminated.
The main thread continues to block, waiting for the consumer thread to mark all tasks as done.
This will never happen and the main thread is stuck, blocking forever for a condition that will never be met. A deadlock.
The program must then be forcefully terminated, such as via Control-C or via the kill command on POSIX operating systems like Linux or MacOS.
This highlights that a deadlock is possible in those cases where processing a task could result in an Error or Exception .
A possible fix is to wrap the processing of the task in a try-catch-finally pattern.
Specifically:
- The call to Queue.get() occurs before the try block.
- The processing of the task occurs within the try block.
- The expected Error or Exception is handled in the except block.
- The call to task_done() occurs within the finally block.
| .. = queue.get() : # process the item sleep(task[1]) print(f'.consumer got {task}') # check for a failure case if task[0] == 5: raise Exception('Something bad happened') : # carry on... pass : # mark the unit of work as processed queue.task_done() |
This approach ensures that even if the processing of a task fails, that the task is still marked as done and that any threads waiting on the queue will be appropriately notified.
Next, let’s look at some common questions about queue join() and task_done() .
Common Questions
This section lists some common questions about thread queue task_done() and join() .
Do you have any questions? Let me know in the comments below and I may add your question to this section.
Why Not Just Use Queue.qsize() or Queue.empty()?
The Queue.qsize() function will report the number of items in the queue and will return a value of zero when there are no tasks in the queue at the time of calling.
| .. not queue.qsize(): # ... |
The Queue.empty() function will return True when there are no tasks in the queue at the time of calling.
| .. queue.empty(): # ... |
Both functions can be used to report if there are no items on the queue, but neither have any way of determining if the tasks retrieved from the queue have been processed and marked done and neither have any way of notifung waiting threads.
Nevertheless, these functions can be used instead of join() in some limited cases.
If join() is called at a time when the thread knows that no further tasks will be added to the queue, such as in the above situations, then qsize() or empty() can be used instead within a busy wait loop.
A busy wait loop or busy waiting is a way for a thread to block by repeatedly checking a condition. Once the condition is met, the thread may then proceed.
For example, below is a busy wait loop using the qsize() function:
| .. not queue.qsize(): pass |
We can also use the empty() function in a busy wait loop.
| .. not queue.empty(): pass |
The problem with the busy wait loop is that the thread will remain active and consume computational resources while waiting for the condition to be met.
The join() function on the other hand will block until the condition is met (e.g. until it is notified), meaning that the thread will not consume any computational resources while waiting.
You can learn more about busy wait loops in this tutorial:
- How to Use Busy Waiting in Python
Is Queue.join() related to Thread.join()?
Calling join() on a queue will block and return once the number of calls to task_done() matches the number of calls to put() at the time that join() is called.
Calling join() a thread will block until the target thread terminates.
You can learn more about Thread.join() in the tutorial:
- How to Join a Thread in Python
Do All Consumer Threads Need To Call task_done()?
If a thread is blocked by calling join() on the queue, then all threads that are retrieving items from the queue via get() must call task_done() in order for the blocked thread to be notified correctly.
What if the Queue is Empty?
A thread may call join() on an empty thread.
If a thread calls join() on a queue that is empty, then it will not block and the call will return immediately.
What if Tasks Are Put After a Call to Join?
Tasks may be put on the queue after a thread has called join() .
Each call to put() will increment an internal counter in the queue. Each call to task_done() decrements the counter. A call to join() will return once the counter has reached zero.
This means that any calls to put() while a thread is blocked on a call to join() will require a subsequent call to task_done() by a consumer thread in order for the blocked thread to be notified.

Can task_done() Be Called Without Calls to get()?
A thread blocked with a call to join() will be notified after a task_done() call has been made for each call to put() .
Any calls to get() are not considered by the blocked thread.
This means that a thread blocked by a call to join() may be notified by the correct number of calls to task_done() , even though all of the tasks may still remain on the queue given the absence of calls to get() .
When Should I Call join()?
The join() function should be called by a thread on a queue when the calling thread wants to be notified when all tasks on the queue have been marked as done.
Ideally, the join() function would be called after all tasks that could be added to the queue have been added to the queue. This is to avoid a race condition where the blocked thread is notified because all tasks have been retrieved from the queue and marked as done, yet the producer thread has more tasks to add to the queue.
When Should I call task_done()?
The task_done() should be called on the queue after a thread has called get() to retrieve the item and after that retrieved item has been processed to the satisfaction of the application.
What if Processing a Task May Raise an Error or Exception?
Processing tasks retrieved from a queue may fail with an Error or Exception .
If this is possible, a try-except-finally or try-finally pattern may be used.
The call to get() on the queue would be made prior to the try block and the call to task_done() would be made in the finally block.
| .. = queue.get() : # ... : # mark the task as done queue.task_done() |
This ensures that regardless of the success or failure of processing the task, the task is marked as done and any thread blocked until all tasks are done will be correctly notified.
Otherwise, if a task_done() call is missed because of an error while processing, any threads waiting on the queue with a call to join() will block forever, resulting in a deadlock.
Further Reading
This section provides additional resources that you may find helpful.
Python Threading Books
- Python Threading Jump-Start , Jason Brownlee ( my book! )
- Threading API Interview Questions
- Threading Module API Cheat Sheet
I also recommend specific chapters in the following books:
- See: Chapter 12: Concurrency
- See: Chapter 7: Concurrency and Parallelism
- See: Chapter: 14: Threads and Processes
- Python Threading: The Complete Guide
- Python ThreadPoolExecutor: The Complete Guide
- Python ThreadPool: The Complete Guide
- threading - Thread-based parallelism
- queue — A synchronized queue class
- Thread (computing), Wikipedia.
- Process (computing), Wikipedia.
You now know how to wait for all tasks to be done on a thread queue.
Do you have any questions? Ask your questions in the comments below and I will do my best to answer.
Photo by Alvis Taurēns on Unsplash
Share this:
Related tutorials:.
About Jason Brownlee
Hi, my name is Jason Brownlee, Ph.D. and I’m the guy behind this website. I am obsessed with Python Concurrency.
I help python developers learn concurrency, super fast. Learn more .
Parallel Loops in Python
Discover how to run your loops in parallel, download your free book now:

Your free book " Parallel Loops in Python " includes complete and working code templates that you can modify and use right now in your own projects.
Reader Interactions
Do you have any questions cancel reply, learn threading systematically.

What if you could develop Python programs that were concurrent from the start?
The threading module provides easy-to-use thread-based concurrency.
Introducing: " Python Threading Jump-Start ".
A new book designed to teach you the threading module step-by-step, super fast!
Insert/edit link
Enter the destination URL
Or link to existing content
task-queue 2.14.0
pip install task-queue Copy PIP instructions
Released: May 7, 2024
Multithreaded cloud queue client.
Verified details
Maintainers.

Unverified details
Project links, github statistics.
- Open issues:
License: BSD License (BSD)
Author: Ignacio Tartavull, William Silversmith, and others
Classifiers
- 5 - Production/Stable
- OSI Approved :: BSD License
- Python :: 3
- Python :: 3.5
- Python :: 3.6
- Python :: 3.7
- Python :: 3.8
Project description

python-task-queue
A client and system for generating, uploading, leasing, and executing dependency free tasks both locally and in the cloud using AWS SQS or on a single machine or cluster with a common file system using file based queues. Of note, file queue requires no setup or queue service and can be used in a distributed fashion on a network filesystem.
The task queue uses JSON as a messaging medium, so be aware that e.g. integer dictionary keys can be turned into strings when bound as a parameter.
Installation
The task queue uses your CloudVolume secrets located in $HOME/.cloudvolume/secrets/ . When using AWS SQS as your queue backend, you must provide $HOME/.cloudvolume/secrets/aws-secret.json . See the CloudVolume repo for additional instructions.
As of version 2.7.0, there are two ways to create a queueable task. The new way is simpler and probably preferred.
MacOS Only: Note that proxy servers are disabled for parallel operation due to libdispatch being not fork-safe.
New School: Queueable Functions
Designate a function as queueable using the @queueable decorator. Currently variable positional arguments ( *args ) and variable keyword arguments ( **kwargs ) are not yet supported. If a function is not marked with the decorator, it cannot be executed via the queue.
You then create queueable instantiations of these functions by using the standard library partial function to create a concrete binding.
Old School: RegisteredTask Subclasses
Define a class that inherits from taskqueue.RegisteredTask and implements the execute method. RegisteredTasks contain logic that will render their attributes into a JSON payload and can be reconstituted into a live class on the other side of a task queue.
Tasks can be loaded into queues locally or in the cloud and executed later. Here's an example implementation of a trivial PrintTask . The attributes of your container class should be simple values that can be easily encoded into JSON such as ints, floats, strings, and numpy arrays. Let the execute method download and manipulate heavier data. If you're feeling curious, you can see what JSON a task will turn into by calling task.payload() .
Local Usage
For small jobs, you might want to use one or more processes to execute the tasks.
This will load the queue with 1000 print tasks then execute them across five processes.
Cloud and Cluster Usage
Set up an SQS queue and acquire an aws-secret.json that is compatible with CloudVolume. Generate the tasks and insert them into the cloud queue.
You can alternatively set up a file based queue that has the same time-based leasing property of an SQS queue.
IMPORTANT: You must import the tasks that will be executed, otherwise the code to execute them has not been loaded.
This inserts 1000 PrintTask JSON descriptions into your SQS queue.
Somewhere else, you'll do the following (probably across multiple workers):
Poll will check the queue for a new task periodically. If a task is found, it will execute it immediately, delete the task from the queue, and request another. If no task is found, a random exponential backoff of up to 120sec is built in to prevent workers from attempting to DDOS the queue. If the task fails to complete, the task will eventually recirculate within the queue, ensuring that all tasks will eventually complete provided they are not fundementally flawed in some way.
Local Container testing
If there is a AWS compatible queue running on a local cluster, e.g. alpine-sqs , the underlying connection client needs additional parameters. These can be passed into the TaskQueue constructor.
The following code on a worker will work in local and production contexts:
Example docker-compose.yml for local testing:
Example docker-compose.yml for production:
Notes on Google PubSub
TaskQueue will try to connect to pubsub using the credentials it finds at ~/.cloudvolume/secrets/google-secret.json
You must first make both a topic and a subscription that is subscribed to that topic.
Then you can specify a taskqueue using this url format (which we invented to include both the project_id, topic and subscription)
Note that Google PubSub doesn't have all the same features as Amazon SQS, including statistics reporting, and so some features do not function properly with this backend.
Also, google pubsub libraries are not installed by default and so if you want to use this backend install with the pubsub option
Notes on File Queue
FileQueue ( fq:// ) is designed to simulate the timed task leasing feature from SQS and exploits a common filesystem to avoid requiring an additional queue server. You can read in detail about its design on the wiki .
There are a few things FileQueue can do that SQS can't and also some quirks you should be aware of. For one, FileQueue can track the number of task completions ( tq.completions , tq.poll(..., tally=True) ), but it does so by appending a byte to a file called completions for each completion. The size of the file in bytes is the number of completions. This design is an attempt to avoid problems with locking and race conditions. FileQueue also tracks insertions ( tq.insertions ) in a more typical way in an insertions file. Also unlike SQS, FileQueue allows listing all tasks at once.
FileQueue also allows releasing all current tasks from their leases, something impossible in SQS. Sometimes a few tasks will die immediately after leasing, but with a long lease, and you'll figure out how to fix them. Instead of starting over or waiting possibly hours, you can set the queue to be made available again ( tq.release_all() ).
As FileQueue is based on the filesystem, it can be managed somewhat via the command line. To delete a queue, just rm -r $QUEUE_PATH . To reset a counter: rm $QUEUE_PATH/completions (e.g.). If you are brave, you could even use the mv command to reassign a task's availability.
We also discovered that FileQueues are also amenable to fixing problems on the fly. In one case, we generated a set of tasks that took 4.5 hours of computation time and decided to run those tasks on a different cluster. The 500k tasks each contained a path to the old storage cluster. Using find , xargs , and sed we were able to fix them efficiently.
Bundled ptq CLI Tool
As of 2.5.0, we now bundle a command line tool ptq to make managing running FileQueues easier.
Distributed dependency free task execution engines (such as Igneous ) often make use of cloud based queues like Amazon Simple Queue Service (SQS). In the connectomics field we process petascale images which requires generating hundreds of thousands or millions of cloud tasks per a run. In one case, we were processing serial blocks of a large image where each block depended on the previous block's completion. Each block's run required the generation and upload of millions of tasks and the use of thousands of workers. The workers would rapidly drain the task queue and it was important to ensure that it could be fed fast enough to prevent starvation of this enormous cluster.
There are a few strategies for accomplishing this. One way might be to use a fully featured DAG supporting engine which could generate the next task on demand. However, we were experienced with SQS and had designed our architecture around it. Furthermore, it was, in our experience, robust to thousands of machines knocking on it. This does not discount that there could be better methods out there, but this was convenient for us.
The two major ways to populate the SQS queue at scale would be a task generating task so a single processor could could enlist hundreds or thousands of others or we could just make our task generating client fast and memory efficient and use a handful of cores for multiprocessing. Keeping things simple and local allows for greater operational flexibility and the addition of a drop-in mutiprocessing execution engine allows for the omission of cloud services for small jobs. Importantly, improved small scale performance doesn't preclude the later development of metageneration facilities.
By default, the Python task queue libraries are single threaded and blocking, resulting in upload rates of at most tens of tasks per second. It is possible to do much better by using threads, multiple processes, and by batching requests. TaskQueue has achivied upload rates of over 3000 tasks per second single core, and around 10,000 per second multicore on a single machine. This is sufficient to keep our cluster fed and allows for programmer flexibility as they can populate queues from their local machine using simple scripts.
How to Achieve High Performance
Attaining the quoted upload rates is simple but takes a few tricks to tune the queue. By default, TaskQueue will upload hundreds of tasks per second using its threading model. We'll show via progressive examples how to tune your upload script to get many thousands of tasks per second with near zero latency and memory usage. Note that the examples below use sqs:// , but apply to fq:// as well. These examples also use the old school style of task instantiation, but you can substitute the new style without consequence.
This first example shows how you might use the queue in the most naive fashion. The tasks list takes a long time to compute, uses a lot of memory, and then inserts a single task at a time, failing to exploit the threading model in TaskQueue. Note that this behavior has changed from previous versions where we endorsed the "with" statement where this form was faster, though still problematic.
The listing above allows you to use ordinary iterative programming techniques to achieve an upload rate of hundreds per a second without much configuration, a marked improvement over simply using boto nakedly. However, the initial generation of a list of tasks uses a lot of memory and introduces a delay while the list is generated.
This form also takes advantage of SQS batch upload which allows for submitting 10 tasks at once. As the overhead for submitting a task lies mainly in HTTP/1.1 TCP/IP connection overhead, batching 10 requests results in nearly a 10x improvement in performance. However, in this case we've created all the tasks up front again in order to batch them correctly which results in the same memory and latency issues as in Listing 1.
In Listing 3, we've started using generators instead of lists. Generators are essentially lazy-lists that compute the next list element on demand. Defining a generator is fast and takes constant time, so we are able to begin production of new elements nearly instantly. The elements are produced on demand and consumed instantly, resulting in a small constant memory overhead that can be typically measured in kilobytes to megabytes.
As generators do not support the len operator, we manually pass in the number of items to display a progress bar.
In Listing 4, we use the green=True argument to use cooperative threads. Under the hood, TaskQueue relies on Python kernel threads to achieve concurrent IO. However, on systems with mutliple cores, especially those in a virutalized or NUMA context, the OS will tend to distribute the threads fairly evenly between cores leading to high context-switching overhead. Ironically, a more powerful multicore system can lead to lower performance. To remedy this issue, we introduce a user-space cooperative threading model (green threads) using gevent (which depending on your system is uses either libev or libuv for an event loop).
This can result in a substantial performance increase on some systems. Typically a single core will be fully utilized with extremely low overhead. However, using cooperative threading with networked IO in Python requires monkey patching the standard library (!!). Refusing to patch the standard library will result in single threaded performance. Thus, using GreenTaskQueue can introduce problems into many larger applications (we've seen problems with multiprocessing and ipython). However, often the task upload script can be isolated from the rest of the system and this allows monkey patching to be safely performed. To give users more control over when they wish to accept the risk of monkey patching, it is not performed automatically and a warning will appear with instructions for amending your program.
In Listing 5, we finally move to multiprocessing to attain the highest speeds. There are three critical pieces of this construction to note.
First, we do not use the usual multiprocessing package and instead use concurrent.futures.ProcessPoolExecutor . If a child process dies in multiprocessing , the parent process will simply hang (this is by design unfortunately...). Using this alternative package, at least an exception will be thrown.
Second, we pass parameters for task generation to the child proceses, not tasks. It is not possible to pass generators from parent to child processes in CPython [1]. It is also inefficient to pass tasks directly as it requires first generating them (as in Listing 1) and then invisibly pickling and unpickling them as they are passed to the child processes. Therefore, we pass only a small number of small picklable objects that are used for constructing a task generator on the other side.
Third, as described in the narrative for Listing 5, the GreenTaskQueue has less context-switching overhead than ordinary multithreaded TaskQueue. Using GreenTaskQueue will cause each core to efficiently run independently of the others. At this point, your main bottlenecks will probably be OS/network card related (let us know if they aren't!). Multiprocessing does scale task production, but it's sub-linear in the number of processes. The task upload rate per a process will fall with each additional core added, but each core still adds additional throughput up to some inflection point.
If you insist on wanting to pass generators to your subprocesses, you can use iterators instead. The construction above allows us to write the generator call up front, pass only a few primatives through the pickling process, and transparently call the generator on the other side. We can even support the len() function which is not available for generators.
If you design your iterators such that the slice operator works, TaskQueue can automatically resection the iterator such that it can be fed to multiple processes. Notably, we don't return PrintTaskIterator(self.start+slc.start, self.start+slc.stop) because it triggers an endless recursion during pickling. However, the runtime copy implementation above sidesteps this issue. Internally, PrintTaskIterator(0,200) will be turned into [ PrintTaskIterator(0,100), PrintTaskIterator(100,200) ] . We also perform tracking of exceptions raised by child processes in a queue. gevent.monkey.patch_all(thread=False) was necessary to avoid multiprocess hanging.
[1] You can't pass generators in CPython but you can pass iterators . You can pass generators if you use Pypy or Stackless Python.
-- Made with <3.
Project details
Release history release notifications | rss feed.
May 7, 2024
Sep 1, 2023
Sep 26, 2022
Jan 6, 2022
Jul 27, 2021
Jul 14, 2021
May 14, 2021
May 10, 2021
Apr 6, 2021
Mar 25, 2021
Feb 10, 2021
Jan 15, 2021
Dec 28, 2020
Dec 6, 2020
Dec 2, 2020
Nov 15, 2020
Nov 13, 2020
Nov 12, 2020
Oct 29, 2020
Sep 25, 2020
Sep 1, 2020
Jul 31, 2020
Jan 27, 2020
Nov 15, 2019
Sep 3, 2019
Apr 30, 2019
Feb 28, 2019
Feb 24, 2019
Feb 22, 2019
Feb 19, 2019
Jan 30, 2019
Jan 27, 2019
Jan 25, 2019
Jan 24, 2019
Oct 3, 2018
Jun 28, 2018
May 10, 2018
May 4, 2018
Mar 9, 2018
Mar 2, 2018
Jan 4, 2018
Jan 3, 2018
Dec 21, 2017
Nov 4, 2017
Nov 3, 2017
Oct 27, 2017
Oct 21, 2017
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages .
Source Distribution
Uploaded May 7, 2024 Source
Built Distribution
Uploaded May 7, 2024 Python 3
Hashes for task-queue-2.14.0.tar.gz
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 | ||
| MD5 | ||
| BLAKE2b-256 |
Hashes for task_queue-2.14.0-py3-none-any.whl
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 | ||
| MD5 | ||
| BLAKE2b-256 |
- português (Brasil)
Supported by

Implementing a Priority Queue in Python

A priority queue is a special type of queue where each element is associated with a priority. In a priority queue, elements are dequeued in order of their priority, rather than their insertion order. This makes priority queues a powerful data structure for scenarios where elements with higher priorities need to be processed first.
Importance of Priority Queues in Programming
Priority queues are widely used in various programming applications, including:
Task scheduling in operating systems
Managing the order of events in simulations
Implementing Dijkstra's algorithm for finding the shortest path in graphs
Managing a to-do list where tasks have different levels of urgency
Implementing a Priority Queue Using heapq
Python provides a built-in library called heapq that can be used to implement priority queues. The heapq module offers an efficient way to maintain a heap, which is a binary tree where the parent node is always smaller than or equal to its child nodes (min-heap).
Basic Operations: Push, Pop, Peek
Let's explore the basic operations of a priority queue using the heapq module.
Pushing an Element
To add an element to the priority queue, use the heappush function:
Popping an Element
To remove and return the smallest element from the priority queue, use the heappop function:
Peeking at the Smallest Element
To look at the smallest element without removing it, simply access the first element of the list:
Example Use Cases for Priority Queues
Let's look at different use cases for priority queues.
Task Scheduling
In task scheduling, tasks with higher priorities should be executed before those with lower priorities. A priority queue can manage the order of task execution efficiently.
Dijkstra's Algorithm
Dijkstra's algorithm finds the shortest path from a source node to all other nodes in a graph. A priority queue is used to select the next node to process based on the shortest known distance.
Advanced Priority Queue Operations
In this section, we will look closer at advanced usage of priority queues.
Updating an Element's Priority
Updating an element's priority involves removing the element and adding it again with the new priority. This can be inefficient, but it's a necessary step since heapq does not support direct priority updates.
Merging Two Priority Queues
To merge two priority queues, use the heapq.merge function, which returns an iterator over the sorted values.
Practical Code Examples
Priority queue with custom objects.
You can use custom objects in a priority queue by implementing comparison methods.
Using Priority Queue in a Multi-threaded Environment
Python's queue.PriorityQueue is a thread-safe priority queue that can be used in multi-threaded applications.
Priority queues are essential for efficiently managing tasks and resources based on priority. Python's heapq and queue.PriorityQueue modules provide powerful tools to implement and manipulate priority queues. Whether for simple tasks or complex algorithms like Dijkstra's, understanding how to use priority queues effectively can significantly enhance your programming toolkit.
For further reading and additional resources, consider the following:
- Python Documentation: heapq
- Python Documentation: queue.PriorityQueue
- Python »
- 3.12.4 Documentation »
- The Python Standard Library »
- Networking and Interprocess Communication »
- asyncio — Asynchronous I/O »
- Theme Auto Light Dark |
Source code: Lib/asyncio/queues.py
asyncio queues are designed to be similar to classes of the queue module. Although asyncio queues are not thread-safe, they are designed to be used specifically in async/await code.
Note that methods of asyncio queues don’t have a timeout parameter; use asyncio.wait_for() function to do queue operations with a timeout.
See also the Examples section below.
A first in, first out (FIFO) queue.
If maxsize is less than or equal to zero, the queue size is infinite. If it is an integer greater than 0 , then await put() blocks when the queue reaches maxsize until an item is removed by get() .
Unlike the standard library threading queue , the size of the queue is always known and can be returned by calling the qsize() method.
Changed in version 3.10: Removed the loop parameter.
This class is not thread safe .
Number of items allowed in the queue.
Return True if the queue is empty, False otherwise.
Return True if there are maxsize items in the queue.
If the queue was initialized with maxsize=0 (the default), then full() never returns True .
Remove and return an item from the queue. If queue is empty, wait until an item is available.
Return an item if one is immediately available, else raise QueueEmpty .
Block until all items in the queue have been received and processed.
The count of unfinished tasks goes up whenever an item is added to the queue. The count goes down whenever a consumer coroutine calls task_done() to indicate that the item was retrieved and all work on it is complete. When the count of unfinished tasks drops to zero, join() unblocks.
Put an item into the queue. If the queue is full, wait until a free slot is available before adding the item.
Put an item into the queue without blocking.
If no free slot is immediately available, raise QueueFull .
Return the number of items in the queue.
Indicate that a formerly enqueued task is complete.
Used by queue consumers. For each get() used to fetch a task, a subsequent call to task_done() tells the queue that the processing on the task is complete.
If a join() is currently blocking, it will resume when all items have been processed (meaning that a task_done() call was received for every item that had been put() into the queue).
Raises ValueError if called more times than there were items placed in the queue.
Priority Queue ¶
A variant of Queue ; retrieves entries in priority order (lowest first).
Entries are typically tuples of the form (priority_number, data) .
LIFO Queue ¶
A variant of Queue that retrieves most recently added entries first (last in, first out).
Exceptions ¶
This exception is raised when the get_nowait() method is called on an empty queue.
Exception raised when the put_nowait() method is called on a queue that has reached its maxsize .
Queues can be used to distribute workload between several concurrent tasks:
Table of Contents
- Priority Queue
Previous topic
Subprocesses
- Report a Bug
- Show Source
- Python Basics
- Interview Questions
- Python Quiz
- Popular Packages
- Python Projects
- Practice Python
- AI With Python
- Learn Python3
- Python Automation
- Python Web Dev
- DSA with Python
- Python OOPs
- Dictionaries
Extracting text from HTML file using Python
Extracting text from an HTML file is a common task in web scraping and data extraction. Python provides powerful libraries such as BeautifulSoup that make this task straightforward. In this article we will explore the process of extracting text from an HTML file using Python .
Use the below command to install the BeautifulSoup library:
Using BeautifulSoup for Text Extraction
BeautifulSoup helps us to parse HTML documents and extract data from them.
Example: In the below example we are extracting text from html file.
Handling Complex HTML Structures
Sometimes HTML files can have complex structures and we might need to extract text from nested tags or specific parts of the HTML. For such scenarios BeautifulSoup provides various methods to handle it.
Extracting Text from Nested Tags
To extract text from nested tags we will navigate through the parse tree using tag names, attributes, or CSS selectors.
Example: In below example we will extract text from nested tags.
Extracting Text Using CSS Selectors
We can also use CSS selectors to target specific elements.
Conclusion:
By following the steps explained in this article, we can efficiently parse and extract text from HTML documents. For complex HTML structures BeautifulSoup’s has powerful methods and CSS selectors. With these techniques, we can perform web scraping and data extraction tasks effectively.

Please Login to comment...
Similar reads.
- Python BeautifulSoup
Improve your Coding Skills with Practice
What kind of Experience do you want to share?
- Stack Overflow for Teams Where developers & technologists share private knowledge with coworkers
- Advertising & Talent Reach devs & technologists worldwide about your product, service or employer brand
- OverflowAI GenAI features for Teams
- OverflowAPI Train & fine-tune LLMs
- Labs The future of collective knowledge sharing
- About the company Visit the blog
Collectives™ on Stack Overflow
Find centralized, trusted content and collaborate around the technologies you use most.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Get early access and see previews of new features.
Python - What is queue.task_done() used for?
I wrote a script that has multiple threads (created with threading.Thread ) fetching URLs from a Queue using queue.get_nowait() , and then processing the HTML. I am new to multi-threaded programming, and am having trouble understanding the purpose of the queue.task_done() function.
When the Queue is empty, it automatically returns the queue.Empty exception. So I don't understand the need for each thread to call the task_done() function. We know that we're done with the queue when its empty, so why do we need to notify it that the worker threads have finished their work (which has nothing to do with the queue, after they've gotten the URL from it)?
Could someone provide me with a code example (ideally using urllib , file I/O, or something other than fibonacci numbers and printing "Hello") that shows me how this function would be used in practical applications?
4 Answers 4
Queue.task_done is not there for the workers' benefit. It is there to support Queue.join .
If I give you a box of work assignments, do I care about when you've taken everything out of the box?
No. I care about when the work is done . Looking at an empty box doesn't tell me that. You and 5 other guys might still be working on stuff you took out of the box.
Queue.task_done lets workers say when a task is done . Someone waiting for all the work to be done with Queue.join will wait until enough task_done calls have been made, not when the queue is empty.
eigenfield points out in the comments that it seems really weird for a queue to have task_done / join methods. That's true, but it's really a naming problem. The queue module has bad name choices that make it sound like a general-purpose queue library, when it's really a thread communication library.
It'd be weird for a general-purpose queue to have task_done / join methods, but it's entirely reasonable for an inter-thread message channel to have a way to indicate that messages have been processed. If the class was called thread_communication.MessageChannel instead of queue.Queue and task_done was called message_processed , the intent would be a lot clearer.
(If you need a general-purpose queue rather than an inter-thread message channel, use collections.deque .)
- 2 Yes, but what I'm asking is why the queue needs to know when the task (i.e. processing the HTML, inserting the extracted data into the DB, etc) is done at all? When it's empty I'm done with it. Why can't I just know that I'm done when the queue.Empty exception is thrown? Why does a queue of URLs need to know that I successfully entered something into the database, or processing some HTML? All the queue should care about is whether all of the URLs have been dispatched to some thread. – J. Taylor Commented Apr 3, 2018 at 19:05
- 2 @J.Taylor: Whoever's calling Queue.join needs to know. – user2357112 Commented Apr 3, 2018 at 19:06
- 2 @J.Taylor: Depends on who needs to know the work is done, and whether work is added to the queue while work is being done. The workers don't need to call task_done to know whether they're done. task_done is a way to communicate to any threads waiting for work to finish. – user2357112 Commented Apr 3, 2018 at 19:55
- 13 To me, the concept of a Queue that implies task_is_done / join semantics is unusual. A queue should only be concerned with put and get and wither it is empty or full. Not task_done() stuff. Am i in twilight zone here? – daparic Commented Jul 16, 2018 at 3:25
- 3 @ifelsemonkey It's just convenient and useful in a very common usage scenario, distributing tasks among workers. And it only applies if you need it. If you never plan to call join() on the queue, you don't need to know or care about task_done() either. – user4815162342 Commented Dec 13, 2018 at 21:53
.task_done() is used to mark .join() that the processing is done.
💡 If you use .join() and don't call .task_done() for every processed item, your script will hang forever.
Ain't nothin' like a short example;
- 2 Why do you need the additional test of "if item is None:" when you will never reach it (unless you actually store None values in the items_queue which you don't do it right now) ? As far as I see the Empty exception is thrown if queue is empty so the execution will "jump" into the catch clause. – Alex Commented Jan 21, 2021 at 7:57
- Is your "💡 If you use .join() and don't call .task_done() for every processed item, your script will hang forever." an actual quote from somewhere else? If so, please link to the source. Otherwise it would be nice to have some info that this is "just" the gist of your (great) answer. – bugmenot123 Commented Oct 5, 2022 at 9:29
"Read the source, Luke!" -- Obi-one Codobi
The source for ayncio.queue is pretty short.
- the number of unfinished tasks goes up by one when you put to the queue.
- it goes down by one with you call task_done
- join() awaits there being no unfinished tasks.
This makes join useful if and only if you are calling task_done(). Using the classic bank analogy:
- people come in the doors and get in line; door is a producer doing a q.put()
- when a teller is idle and a person is in line, they go to the teller window. teller does a q.get() .
- When the teller has finished helping the person, they are ready for the next one. teller does a q.task_done()
- at 5 p.m., the doors are locked door task finishes
- you wait until both the line is empty and each teller has finished helping the person in front of them. await q.join(tellers)
- then you send the tellers home, who are now all idling with an empty queue. for teller in tellers: teller.cancel()
Without the task_done(), you cannot know every teller is done with people. You cannot send a teller home while they have a person at his or her window.
- Excellent example. Thanks! – Jabba Commented Aug 27, 2021 at 18:23
Could someone provide me with a code example (ideally using urllib, file I/O, or something other than fibonacci numbers and printing "Hello") that shows me how this function would be used in practical applications?
@user2357112's answer nicely explains the purpose of task_done , but lacks the requested example. Here is a function that calculates checksums of an arbitrary number of files and returns a dict mapping each file name to the corresponding checksum. Internal to the function, the work is divided among a several threads.
The function uses of Queue.join to wait until the workers have finished their assigned tasks, so it is safe to return the dictionary to the caller. It is a convenient way to wait for all files being processed , as opposed to them being merely dequeued.
A note on the GIL: since the code in hashlib internally releases the GIL while calculating the checksum, using multiple threads yields a measurable (1.75x-2x depending on Python version) speedup compared to the single-threaded variant.
Your Answer
Reminder: Answers generated by artificial intelligence tools are not allowed on Stack Overflow. Learn more
Sign up or log in
Post as a guest.
Required, but never shown
By clicking “Post Your Answer”, you agree to our terms of service and acknowledge you have read our privacy policy .
Not the answer you're looking for? Browse other questions tagged python queue task or ask your own question .
- Featured on Meta
- We spent a sprint addressing your requests — here’s how it went
- Upcoming initiatives on Stack Overflow and across the Stack Exchange network...
- What makes a homepage useful for logged-in users
Hot Network Questions
- How to choose between 3/4 and 6/8 time?
- What was the first science fiction or fantasy element to appear in any Batman comic?
- On the Rambam's view on funding Torah scholars
- How will a planet on asteroid belt see Jupiter?
- Are the North Star and the moon ever visible in the night sky at the same time?
- Accommodating whiteboard glare for low-vision student
- Does 誰と mean 誰とも?
- Is an employment Conflict of Interest necessary when redundant with my Affiliation?
- Does the damage from Thunderwave occur before or after the target is moved
- As a DM, what should I do if a person decides to play a rogue?
- Coping with consequences of a dog bite before buying a puppy
- Custom panel is created but does not display properly in custom plug-in
- Reference about cancellation property for semigroups
- Does there exist a nontrivial "good" set?
- Where do we go if we gain knowledge of the absolute truth?
- Of "ils" and "elles", which pronoun is, grammatically speaking, used to refer to a group with an overwhelming female majority?
- Reviewer "rejected" my submission, and then submitted one by their own. What did they do wrong?
- Dual of slope semistable vector bundle on higher dimensional variety
- Are there any reasons I shouldn't remove this odd nook from a basement room?
- Error concerning projectile motion in respected textbook?
- USB Data communication issue on a panelized pcba hardware test platform
- In the travel industry, why is the "business" term coined in for luxury or premium services?
- Using register after multiplier in the MACC
- Equivalence of first/second choice with naive probability - I don't buy it

An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
Free Cyber Services #protect2024 Secure Our World Shields Up Report A Cyber Issue
Vulnerability Summary for the Week of June 24, 2024
The CISA Vulnerability Bulletin provides a summary of new vulnerabilities that have been recorded by the National Institute of Standards and Technology (NIST) National Vulnerability Database (NVD) in the past week. In some cases, the vulnerabilities in the bulletin may not yet have assigned CVSS scores. Please visit NVD for updated vulnerability entries, which include CVSS scores once they are available.
Vulnerabilities are based on the Common Vulnerabilities and Exposures (CVE) vulnerability naming standard and are organized according to severity, determined by the Common Vulnerability Scoring System (CVSS) standard. The division of high, medium, and low severities correspond to the following scores:
- High : vulnerabilities with a CVSS base score of 7.0–10.0
- Medium : vulnerabilities with a CVSS base score of 4.0–6.9
- Low : vulnerabilities with a CVSS base score of 0.0–3.9
Entries may include additional information provided by organizations and efforts sponsored by CISA. This information may include identifying information, values, definitions, and related links. Patch information is provided when available. Please note that some of the information in the bulletin is compiled from external, open-source reports and is not a direct result of CISA analysis.
High Vulnerabilities
| Primary Vendor -- Product | Description | Published | CVSS Score | Source & Patch Info |
|---|---|---|---|---|
| access_management_specialist_project -- access_management_specialist | An issue in Shenzhen Weitillage Industrial Co., Ltd the access management specialist V6.62.51215 allows a remote attacker to obtain sensitive information. | 2024-06-24 | | |
| aimeos--ai-client-html | ai-client-html is an Aimeos e-commerce HTML client component. Debug information revealed sensitive information from environment variables in error log. This issue has been patched in versions 2024.04.7, 2023.10.15, 2022.10.13 and 2021.10.22. | 2024-06-25 | | |
| amazon -- freertos-plus-tcp | FreeRTOS-Plus-TCP is a lightweight TCP/IP stack for FreeRTOS. FreeRTOS-Plus-TCP versions 4.0.0 through 4.1.0 contain a buffer over-read issue in the DNS Response Parser when parsing domain names in a DNS response. A carefully crafted DNS response with domain name length value greater than the actual domain name length, could cause the parser to read beyond the DNS response buffer. This issue affects applications using DNS functionality of the FreeRTOS-Plus-TCP stack. Applications that do not use DNS functionality are not affected, even when the DNS functionality is enabled. This vulnerability has been patched in version 4.1.1. | 2024-06-24 | | |
| Arista Networks--Arista Wireless Access Points | This Advisory describes an issue that impacts Arista Wireless Access Points. Any entity with the ability to authenticate via SSH to an affected AP as the "config" user is able to cause a privilege escalation via spawning a bash shell. The SSH CLI session does not require high permissions to exploit this vulnerability, but the config password is required to establish the session. The spawned shell is able to obtain root privileges. | 2024-06-27 | | |
| auto-featured-image_project -- auto-featured-image | The Auto Featured Image plugin for WordPress is vulnerable to arbitrary file uploads due to missing file type validation in the 'create_post_attachment_from_url' function in all versions up to, and including, 1.2. This makes it possible for authenticated attackers, with contributor-level and above permissions, to upload arbitrary files on the affected site's server which may make remote code execution possible. | 2024-06-27 | | |
| Avaya--IP Office | An improper input validation vulnerability was discovered in Avaya IP Office that could allow remote command or code execution via a specially crafted web request to the Web Control component. Affected versions include all versions prior to 11.1.3.1. | 2024-06-25 | | |
| Avaya--IP Office | An unrestricted file upload vulnerability in Avaya IP Office was discovered that could allow remote command or code execution via the One-X component. Affected versions include all versions prior to 11.1.3.1. | 2024-06-25 | | |
| ays-pro--Quiz Maker | The Quiz Maker plugin for WordPress is vulnerable to time-based SQL Injection via the 'ays_questions' parameter in all versions up to, and including, 6.5.8.3 due to insufficient escaping on the user supplied parameter and lack of sufficient preparation on the existing SQL query. This makes it possible for unauthenticated attackers to append additional SQL queries into already existing queries that can be used to extract sensitive information from the database. | 2024-06-25 | | |
| Baicells--Snap Router | Use of Hard-coded Credentials vulnerability in Baicells Snap Router BaiCE_BMI on EP3011 (User Passwords modules) allows unauthorized access to the device. | 2024-06-25 | | |
| BC Security--Empire | BC Security Empire before 5.9.3 is vulnerable to a path traversal issue that can lead to remote code execution. A remote, unauthenticated attacker can exploit this vulnerability over HTTP by acting as a normal agent, completing all cryptographic handshakes, and then triggering an upload of payload data containing a malicious path. | 2024-06-27 | | |
| Brocade--Fabric OS | A vulnerability in the default configuration of the Simple Network Management Protocol (SNMP) feature of Brocade Fabric OS versions before v9.0.0 could allow an authenticated, remote attacker to read data from an affected device via SNMP. The vulnerability is due to hard-coded, default community string in the configuration file for the SNMP daemon. An attacker could exploit this vulnerability by using the static community string in SNMP version 1 queries to an affected device. | 2024-06-26 | | |
| ChatGPTNextWeb--ChatGPT-Next-Web | NextChat is a cross-platform ChatGPT/Gemini UI. There is a Server-Side Request Forgery (SSRF) vulnerability due to a lack of validation of the `endpoint` GET parameter on the WebDav API endpoint. This SSRF can be used to perform arbitrary HTTPS request from the vulnerable instance (MKCOL, PUT and GET methods supported), or to target NextChat users and make them execute arbitrary JavaScript code in their browser. This vulnerability has been patched in version 2.12.4. | 2024-06-28 | | |
| CycloneDX--cyclonedx-core-java | The CycloneDX core module provides a model representation of the SBOM along with utilities to assist in creating, validating, and parsing SBOMs. Before deserializing CycloneDX Bill of Materials in XML format, _cyclonedx-core-java_ leverages XPath expressions to determine the schema version of the BOM. The `DocumentBuilderFactory` used to evaluate XPath expressions was not configured securely, making the library vulnerable to XML External Entity (XXE) injection. This vulnerability has been fixed in cyclonedx-core-java version 9.0.4. | 2024-06-28 | | |
| DataDog--dd-trace-cpp | dd-trace-cpp is the Datadog distributed tracing for C++. When the library fails to extract trace context due to malformed unicode, it logs the list of audited headers and their values using the `nlohmann` JSON library. However, due to the way the JSON library is invoked, it throws an uncaught exception, which results in a crash. This vulnerability has been patched in version 0.2.2. | 2024-06-28 | | |
| Dell--Integrated Dell Remote Access Controller 9 | iDRAC9, versions prior to 7.00.00.172 for 14th Generation and 7.10.50.00 for 15th and 16th Generations, contains a session hijacking vulnerability in IPMI. A remote attacker could potentially exploit this vulnerability, leading to arbitrary code execution on the vulnerable application. | 2024-06-29 | | |
| Dell--PowerProtect DD | Dell PowerProtect DD, versions prior to 8.0, LTS 7.13.1.0, LTS 7.10.1.30, LTS 7.7.5.40 contain a buffer overflow vulnerability. A remote low privileged attacker could potentially exploit this vulnerability, leading to an application crash or execution of arbitrary code on the vulnerable application's underlying operating system with privileges of the vulnerable application. | 2024-06-26 | | |
| Dell--PowerProtect DD | Dell PowerProtect DD, versions prior to 8.0, LTS 7.13.1.0, LTS 7.10.1.30, LTS 7.7.5.40 contain an OS command injection vulnerability in an admin operation. A remote low privileged attacker could potentially exploit this vulnerability, leading to the execution of arbitrary OS commands on the system application's underlying OS with the privileges of the vulnerable application. Exploitation may lead to a system take over by an attacker. | 2024-06-26 | | |
| Elastic--Elastic Cloud Enterprise | It was identified that under certain specific preconditions, an API key that was originally created with a specific privileges could be subsequently used to create new API keys that have elevated privileges. | 2024-06-28 | | |
| flippercode--WP Maps Display Google Maps Perfectly with Ease | The WordPress Plugin for Google Maps - WP MAPS plugin for WordPress is vulnerable to SQL Injection via the 'id' parameter of the 'put_wpgm' shortcode in all versions up to, and including, 4.6.1 due to insufficient escaping on the user supplied parameter and lack of sufficient preparation on the existing SQL query. This makes it possible for authenticated attackers, with contributor-level access and above, to append additional SQL queries into already existing queries that can be used to extract sensitive information from the database. | 2024-06-29 | | |
| Fortra--FileCatalyst Workflow | A SQL Injection vulnerability in Fortra FileCatalyst Workflow allows an attacker to modify application data. Likely impacts include creation of administrative users and deletion or modification of data in the application database. Data exfiltration via SQL injection is not possible using this vulnerability. Successful unauthenticated exploitation requires a Workflow system with anonymous access enabled, otherwise an authenticated user is required. This issue affects all versions of FileCatalyst Workflow from 5.1.6 Build 135 and earlier. | 2024-06-25 | | |
| gitlab -- gitlab | An issue was discovered in GitLab CE/EE affecting all versions starting from 15.8 prior to 16.11.5, starting from 17.0 prior to 17.0.3, and starting from 17.1 prior to 17.1.1, which allows an attacker to trigger a pipeline as another user under certain circumstances. | 2024-06-27 | | |
| gitlab -- gitlab | Improper authorization in global search in GitLab EE affecting all versions from 16.11 prior to 16.11.5 and 17.0 prior to 17.0.3 and 17.1 prior to 17.1.1 allows an attacker leak content of a private repository in a public project. | 2024-06-27 | | |
| goauthentik--authentik | authentik is an open-source Identity Provider that emphasizes flexibility and versatility. Authentik API-Access-Token mechanism can be exploited to gain admin user privileges. A successful exploit of the issue will result in a user gaining full admin access to the Authentik application, including resetting user passwords and more. This issue has been patched in version(s) 2024.2.4, 2024.4.2 and 2024.6.0. | 2024-06-28 | | |
| goauthentik--authentik | authentik is an open-source Identity Provider. Access restrictions assigned to an application were not checked when using the OAuth2 Device code flow. This could potentially allow users without the correct authorization to get OAuth tokens for an application and access it. This issue has been patched in version(s) 2024.6.0, 2024.2.4 and 2024.4.3. | 2024-06-28 | | |
| HashiCorp--Shared library | HashiCorp's go-getter library can be coerced into executing Git update on an existing maliciously modified Git Configuration, potentially leading to arbitrary code execution. | 2024-06-25 | | |
| Hewlett Packard Enterprise (HPE)--HPE Athonet Mobile Core | A security vulnerability has been identified in HPE Athonet Mobile Core software. The core application contains a code injection vulnerability where a threat actor could execute arbitrary commands with the privilege of the underlying container leading to complete takeover of the target system. | 2024-06-25 | | |
| Hitachi Vantara--Pentaho Business Analytics Server | Hitachi Vantara Pentaho Business Analytics Server prior to versions 10.1.0.0 and 9.3.0.7, including 8.3.x allow a malicious URL to inject content into the Analyzer plugin interface. | 2024-06-26 | | |
| Hitachi Vantara--Pentaho Business Analytics Server | Hitachi Vantara Pentaho Business Analytics Server prior to versions 10.1.0.0 and 9.3.0.7, including 8.3.x allow a malicious URL to inject content into the Analyzer plugin interface. | 2024-06-26 | | |
| Hitachi Vantara--Pentaho Business Analytics Server | Hitachi Vantara Pentaho Business Analytics Server versions before 10.1.0.0 and 9.3.0.7, including 8.3.x do not correctly protect the ACL service endpoint of the Pentaho User Console against XML External Entity Reference. | 2024-06-26 | | |
| IBM--MQ | IBM MQ 9.3 LTS and 9.3 CD could allow an authenticated user to escalate their privileges under certain configurations due to incorrect privilege assignment. IBM X-Force ID: 289894. | 2024-06-28 | | |
| IBM--OpenBMC | IBM OpenBMC FW1050.00 through FW1050.10 BMCWeb HTTPS server component could disclose sensitive URI content to an unauthorized actor that bypasses authentication channels. IBM X-ForceID: 290026. | 2024-06-27 | | |
| IBM--Security Access Manager Docker | IBM Security Access Manager Docker 10.0.0.0 through 10.0.7.1 could allow a local user to obtain root access due to improper access controls. IBM X-Force ID: 254638. | 2024-06-27 | | |
| IBM--Security Access Manager Docker | IBM Security Access Manager Docker 10.0.0.0 through 10.0.7.1 could allow a local user to obtain root access due to improper access controls. IBM X-Force ID: 254649. | 2024-06-27 | | |
| IBM--Security Access Manager Docker | IBM Security Access Manager Docker 10.0.0.0 through 10.0.7.1, under certain configurations, could allow a user on the network to install malicious packages. IBM X-Force ID: 261197. | 2024-06-27 | | |
| Icegram--Email Subscribers & Newsletters | Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection') vulnerability in Icegram Email Subscribers & Newsletters allows SQL Injection.This issue affects Email Subscribers & Newsletters: from n/a through 5.7.25. | 2024-06-26 | | |
| InstaWP Team--InstaWP Connect | Improper Control of Generation of Code ('Code Injection') vulnerability in InstaWP Team InstaWP Connect allows Code Injection.This issue affects InstaWP Connect: from n/a through 0.1.0.38. | 2024-06-24 | | |
| Intrado--911 Emergency Gateway (EGW) | Intrado 911 Emergency Gateway login form is vulnerable to an unauthenticated blind time-based SQL injection, which may allow an unauthenticated remote attacker to execute malicious code, exfiltrate data, or manipulate the database. | 2024-06-26 | | |
| itsourcecode--Online Food Ordering System | A vulnerability has been found in itsourcecode Online Food Ordering System up to 1.0 and classified as critical. This vulnerability affects unknown code of the file /addproduct.php. The manipulation of the argument photo leads to unrestricted upload. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. VDB-269806 is the identifier assigned to this vulnerability. | 2024-06-27 | | |
| itsourcecode--Pool of Bethesda Online Reservation System | A vulnerability, which was classified as critical, has been found in itsourcecode Pool of Bethesda Online Reservation System 1.0. Affected by this issue is some unknown functionality of the file controller.php. The manipulation of the argument rmtype_id leads to sql injection. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. The identifier of this vulnerability is VDB-269804. | 2024-06-27 | | |
| itsourcecode--Simple Online Hotel Reservation System | A vulnerability was found in itsourcecode Simple Online Hotel Reservation System 1.0. It has been declared as critical. This vulnerability affects unknown code of the file index.php. The manipulation of the argument username leads to sql injection. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. The identifier of this vulnerability is VDB-269620. | 2024-06-25 | | |
| j11g -- cruddiy | The CRUDDIY project is vulnerable to shell command injection via sending a crafted POST request to the application server. The exploitation risk is limited since CRUDDIY is meant to be launched locally. Nevertheless, a user with the project running on their computer might visit a website which would send such a malicious request to the locally launched server. | 2024-06-24 | | |
| Juniper Networks--Session Smart Router | An Authentication Bypass Using an Alternate Path or Channel vulnerability in Juniper Networks Session Smart Router or conductor running with a redundant peer allows a network based attacker to bypass authentication and take full control of the device. Only routers or conductors that are running in high-availability redundant configurations are affected by this vulnerability. No other Juniper Networks products or platforms are affected by this issue. This issue affects: Session Smart Router: * All versions before 5.6.15, * from 6.0 before 6.1.9-lts, * from 6.2 before 6.2.5-sts. Session Smart Conductor: * All versions before 5.6.15, * from 6.0 before 6.1.9-lts, * from 6.2 before 6.2.5-sts. WAN Assurance Router: * 6.0 versions before 6.1.9-lts, * 6.2 versions before 6.2.5-sts. | 2024-06-27 | | |
| linux -- linux_kernel | In the Linux kernel, the following vulnerability has been resolved: drm: zynqmp_dpsub: Always register bridge We must always register the DRM bridge, since zynqmp_dp_hpd_work_func calls drm_bridge_hpd_notify, which in turn expects hpd_mutex to be initialized. We do this before zynqmp_dpsub_drm_init since that calls drm_bridge_attach. This fixes the following lockdep warning: [ 19.217084] ------------[ cut here ]------------ [ 19.227530] DEBUG_LOCKS_WARN_ON(lock->magic != lock) [ 19.227768] WARNING: CPU: 0 PID: 140 at kernel/locking/mutex.c:582 __mutex_lock+0x4bc/0x550 [ 19.241696] Modules linked in: [ 19.244937] CPU: 0 PID: 140 Comm: kworker/0:4 Not tainted 6.6.20+ #96 [ 19.252046] Hardware name: xlnx,zynqmp (DT) [ 19.256421] Workqueue: events zynqmp_dp_hpd_work_func [ 19.261795] pstate: 60000005 (nZCv daif -PAN -UAO -TCO -DIT -SSBS BTYPE=--) [ 19.269104] pc : __mutex_lock+0x4bc/0x550 [ 19.273364] lr : __mutex_lock+0x4bc/0x550 [ 19.277592] sp : ffffffc085c5bbe0 [ 19.281066] x29: ffffffc085c5bbe0 x28: 0000000000000000 x27: ffffff88009417f8 [ 19.288624] x26: ffffff8800941788 x25: ffffff8800020008 x24: ffffffc082aa3000 [ 19.296227] x23: ffffffc080d90e3c x22: 0000000000000002 x21: 0000000000000000 [ 19.303744] x20: 0000000000000000 x19: ffffff88002f5210 x18: 0000000000000000 [ 19.311295] x17: 6c707369642e3030 x16: 3030613464662072 x15: 0720072007200720 [ 19.318922] x14: 0000000000000000 x13: 284e4f5f4e524157 x12: 0000000000000001 [ 19.326442] x11: 0001ffc085c5b940 x10: 0001ff88003f388b x9 : 0001ff88003f3888 [ 19.334003] x8 : 0001ff88003f3888 x7 : 0000000000000000 x6 : 0000000000000000 [ 19.341537] x5 : 0000000000000000 x4 : 0000000000001668 x3 : 0000000000000000 [ 19.349054] x2 : 0000000000000000 x1 : 0000000000000000 x0 : ffffff88003f3880 [ 19.356581] Call trace: [ 19.359160] __mutex_lock+0x4bc/0x550 [ 19.363032] mutex_lock_nested+0x24/0x30 [ 19.367187] drm_bridge_hpd_notify+0x2c/0x6c [ 19.371698] zynqmp_dp_hpd_work_func+0x44/0x54 [ 19.376364] process_one_work+0x3ac/0x988 [ 19.380660] worker_thread+0x398/0x694 [ 19.384736] kthread+0x1bc/0x1c0 [ 19.388241] ret_from_fork+0x10/0x20 [ 19.392031] irq event stamp: 183 [ 19.395450] hardirqs last enabled at (183): [<ffffffc0800b9278>] finish_task_switch.isra.0+0xa8/0x2d4 [ 19.405140] hardirqs last disabled at (182): [<ffffffc081ad3754>] __schedule+0x714/0xd04 [ 19.413612] softirqs last enabled at (114): [<ffffffc080133de8>] srcu_invoke_callbacks+0x158/0x23c [ 19.423128] softirqs last disabled at (110): [<ffffffc080133de8>] srcu_invoke_callbacks+0x158/0x23c [ 19.432614] ---[ end trace 0000000000000000 ]--- (cherry picked from commit 61ba791c4a7a09a370c45b70a81b8c7d4cf6b2ae) | 2024-06-24 | | |
| linux -- linux_kernel | In the Linux kernel, the following vulnerability has been resolved: riscv: prevent pt_regs corruption for secondary idle threads Top of the kernel thread stack should be reserved for pt_regs. However this is not the case for the idle threads of the secondary boot harts. Their stacks overlap with their pt_regs, so both may get corrupted. Similar issue has been fixed for the primary hart, see c7cdd96eca28 ("riscv: prevent stack corruption by reserving task_pt_regs(p) early"). However that fix was not propagated to the secondary harts. The problem has been noticed in some CPU hotplug tests with V enabled. The function smp_callin stored several registers on stack, corrupting top of pt_regs structure including status field. As a result, kernel attempted to save or restore inexistent V context. | 2024-06-24 | | |
| linux -- linux_kernel | In the Linux kernel, the following vulnerability has been resolved: drm/amdgpu: Fix buffer size in gfx_v9_4_3_init_ cp_compute_microcode() and rlc_microcode() The function gfx_v9_4_3_init_microcode in gfx_v9_4_3.c was generating about potential truncation of output when using the snprintf function. The issue was due to the size of the buffer 'ucode_prefix' being too small to accommodate the maximum possible length of the string being written into it. The string being written is "amdgpu/%s_mec.bin" or "amdgpu/%s_rlc.bin", where %s is replaced by the value of 'chip_name'. The length of this string without the %s is 16 characters. The warning message indicated that 'chip_name' could be up to 29 characters long, resulting in a total of 45 characters, which exceeds the buffer size of 30 characters. To resolve this issue, the size of the 'ucode_prefix' buffer has been reduced from 30 to 15. This ensures that the maximum possible length of the string being written into the buffer will not exceed its size, thus preventing potential buffer overflow and truncation issues. Fixes the below with gcc W=1: drivers/gpu/drm/amd/amdgpu/gfx_v9_4_3.c: In function 'gfx_v9_4_3_early_init': drivers/gpu/drm/amd/amdgpu/gfx_v9_4_3.c:379:52: warning: '%s' directive output may be truncated writing up to 29 bytes into a region of size 23 [-Wformat-truncation=] 379 | snprintf(fw_name, sizeof(fw_name), "amdgpu/%s_rlc.bin", chip_name); | ^~ ...... 439 | r = gfx_v9_4_3_init_rlc_microcode(adev, ucode_prefix); | ~~~~~~~~~~~~ drivers/gpu/drm/amd/amdgpu/gfx_v9_4_3.c:379:9: note: 'snprintf' output between 16 and 45 bytes into a destination of size 30 379 | snprintf(fw_name, sizeof(fw_name), "amdgpu/%s_rlc.bin", chip_name); | ^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ drivers/gpu/drm/amd/amdgpu/gfx_v9_4_3.c:413:52: warning: '%s' directive output may be truncated writing up to 29 bytes into a region of size 23 [-Wformat-truncation=] 413 | snprintf(fw_name, sizeof(fw_name), "amdgpu/%s_mec.bin", chip_name); | ^~ ...... 443 | r = gfx_v9_4_3_init_cp_compute_microcode(adev, ucode_prefix); | ~~~~~~~~~~~~ drivers/gpu/drm/amd/amdgpu/gfx_v9_4_3.c:413:9: note: 'snprintf' output between 16 and 45 bytes into a destination of size 30 413 | snprintf(fw_name, sizeof(fw_name), "amdgpu/%s_mec.bin", chip_name); | ^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ | 2024-06-24 | | |
| Magarsus Consultancy--SSO (Single Sign On) | Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection'), CWE - 200 - Exposure of Sensitive Information to an Unauthorized Actor, CWE - 522 - Insufficiently Protected Credentials vulnerability in Magarsus Consultancy SSO (Single Sign On) allows SQL Injection.This issue affects SSO (Single Sign On): from 1.0 before 1.1. | 2024-06-26 | | |
| Membership Software--WishList Member X | Improper Control of Generation of Code ('Code Injection') vulnerability in Membership Software WishList Member X allows Code Injection.This issue affects WishList Member X: from n/a before 3.26.7. | 2024-06-24 | | |
| Membership Software--WishList Member X | Improper Privilege Management vulnerability in Membership Software WishList Member X allows Privilege Escalation.This issue affects WishList Member X: from n/a before 3.26.7. | 2024-06-24 | | |
| Membership Software--WishList Member X | Missing Authorization vulnerability in Membership Software WishList Member X.This issue affects WishList Member X: from n/a before 3.26.7. | 2024-06-24 | | |
| Mia Technology Inc.--Mia-Med Health Aplication | Improper Restriction of Excessive Authentication Attempts vulnerability in Mia Technology Inc. Mia-Med Health Aplication allows Interface Manipulation.This issue affects Mia-Med Health Aplication: before 1.0.14. | 2024-06-24 | | |
| Microsoft--Microsoft Power Platform | An authenticated attacker can exploit an Untrusted Search Path vulnerability in Microsoft Dataverse to execute code over a network. | 2024-06-27 | | |
| mitmproxy--pdoc | pdoc provides API Documentation for Python Projects. Documentation generated with `pdoc --math` linked to JavaScript files from polyfill.io. The polyfill.io CDN has been sold and now serves malicious code. This issue has been fixed in pdoc 14.5.1. | 2024-06-26 | | |
| modalweb--Advanced File Manager | The Advanced File Manager plugin for WordPress is vulnerable to Sensitive Information Exposure in all versions up to, and including, 5.2.4 via the 'fma_local_file_system' function. This makes it possible for unauthenticated attackers to extract sensitive data including backups or other sensitive information if the files have been moved to the built-in Trash folder. | 2024-06-29 | | |
| Moxa--OnCell G3150A-LTE Series | OnCell G3470A-LTE Series firmware versions v1.7.7 and prior have been identified as vulnerable due to a lack of neutralized inputs in IPSec configuration. An attacker could modify the intended commands sent to target functions, which could cause malicious users to execute unauthorized commands. | 2024-06-25 | | |
| Moxa--OnCell G3150A-LTE Series | OnCell G3470A-LTE Series firmware versions v1.7.7 and prior have been identified as vulnerable due to missing bounds checking on buffer operations. An attacker could write past the boundaries of allocated buffer regions in memory, causing a program crash. | 2024-06-25 | | |
| Moxa--OnCell G3470A-LTE Series | OnCell G3470A-LTE Series firmware versions v1.7.7 and prior have been identified as vulnerable due to a lack of neutralized inputs in the web key upload function. An attacker could modify the intended commands sent to target functions, which could cause malicious users to execute unauthorized commands. | 2024-06-25 | | |
| n/a--n/a | An issue was discovered in the Agent in Delinea Privilege Manager (formerly Thycotic Privilege Manager) before 12.0.1096 on Windows. Sometimes, a non-administrator user can copy a crafted DLL file to a temporary directory (used by .NET Shadow Copies) such that privilege escalation can occur if the core agent service loads that file. | 2024-06-28 | | |
| Next4Biz CRM & BPM Software--Business Process Manangement (BPM) | Improper Control of Generation of Code ('Code Injection') vulnerability in Next4Biz CRM & BPM Software Business Process Manangement (BPM) allows Remote Code Inclusion.This issue affects Business Process Manangement (BPM): from 6.6.4.4 before 6.6.4.5. | 2024-06-24 | | |
| omron -- nj101-1000_firmware | Insufficient verification of data authenticity issue exists in NJ Series CPU Unit all versions and NX Series CPU Unit all versions. If a user program in the affected product is altered, the product may not be able to detect the alteration. | 2024-06-24 | | |
| pendulum-project--ntpd-rs | nptd-rs is a tool for synchronizing your computer's clock, implementing the NTP and NTS protocols. There is a missing limit for accepted NTS-KE connections. This allows an unauthenticated remote attacker to crash ntpd-rs when an NTS-KE server is configured. Non NTS-KE server configurations, such as the default ntpd-rs configuration, are unaffected. This vulnerability has been patched in version 1.1.3. | 2024-06-28 | | |
| pgadmin.org--pgAdmin 4 | pgAdmin <= 8.8 has an installation Directory permission issue. Because of this issue, attackers can gain unauthorised access to the installation directory on the Debian or RHEL 8 platforms. | 2024-06-25 | | |
| Progress Software Corporation--WhatsUp Gold | In WhatsUp Gold versions released before 2023.1.3, a Remote Code Execution issue exists in Progress WhatsUp Gold. This vulnerability allows an unauthenticated attacker to achieve the RCE as a service account through NmApi.exe. | 2024-06-25 | | |
| Progress Software Corporation--WhatsUp Gold | In WhatsUp Gold versions released before 2023.1.3, an unauthenticated Remote Code Execution vulnerability in Progress WhatsUpGold. The Apm.UI.Areas.APM.Controllers.CommunityController allows execution of commands with iisapppool\nmconsole privileges. | 2024-06-25 | | |
| Progress Software Corporation--WhatsUp Gold | In WhatsUp Gold versions released before 2023.1.3, an unauthenticated Remote Code Execution vulnerability in Progress WhatsUpGold. The WhatsUp.ExportUtilities.Export.GetFileWithoutZip allows execution of commands with iisapppool\nmconsole privileges. | 2024-06-25 | | |
| Progress Software Corporation--WhatsUp Gold | In WhatsUp Gold versions released before 2023.1.3, an authenticated user with certain permissions can upload an arbitrary file and obtain RCE using Apm.UI.Areas.APM.Controllers.Api.Applications.AppProfileImportController. | 2024-06-25 | | |
| Progress Software Corporation--WhatsUp Gold | In WhatsUp Gold versions released before 2023.1.3, an Improper Access Control vulnerability in Wug.UI.Controllers.InstallController.SetAdminPassword allows local attackers to modify admin's password. | 2024-06-25 | | |
| Progress Software Corporation--WhatsUp Gold | In WhatsUp Gold versions released before 2023.1.3, there is a missing authentication vulnerability in WUGDataAccess.Credentials. This vulnerability allows unauthenticated attackers to disclose Windows Credentials stored in the product Credential Library. | 2024-06-25 | | |
| Progress Software Corporation--WhatsUp Gold | In WhatsUp Gold versions released before 2023.1.3, a vulnerability exists in the TestController functionality. A specially crafted unauthenticated HTTP request can lead to a disclosure of sensitive information. | 2024-06-25 | | |
| Progress Software Corporation--WhatsUp Gold | In WhatsUp Gold versions released before 2023.1.3, an uncontrolled resource consumption vulnerability exists. A specially crafted unauthenticated HTTP request to the TestController Chart functionality can lead to denial of service. | 2024-06-25 | | |
| Progress Software Corporation--WhatsUp Gold | In WhatsUp Gold versions released before 2023.1.3, an unauthenticated Denial of Service vulnerability was identified. An unauthenticated attacker can put the application into the SetAdminPassword installation step, which renders the application non-accessible. | 2024-06-25 | | |
| Progress Software Corporation--WhatsUp Gold | In WhatsUp Gold versions released before 2023.1.3, a Server Side Request Forgery vulnerability exists in the GetASPReport feature. This allows any authenticated user to retrieve ASP reports from an HTML form. | 2024-06-25 | | |
| Progress Software Corporation--WhatsUp Gold | In WhatsUp Gold versions released before 2023.1.3, an authenticated SSRF vulnerability in Wug.UI.Areas.Wug.Controllers.SessionControler.Update allows a low privileged user to chain this SSRF with an Improper Access Control vulnerability. This can be used to escalate privileges to Admin. | 2024-06-25 | | |
| Progress Software Corporation--WhatsUp Gold | In WhatsUp Gold versions released before 2023.1.3, Distributed Edition installations can be exploited by using a deserialization tool to achieve a Remote Code Execution as SYSTEM. The vulnerability exists in the main message processing routines NmDistributed.DistributedServiceBehavior.OnMessage for server and NmDistributed.DistributedClient.OnMessage for clients. | 2024-06-25 | | |
| Progress--MOVEit Gateway | Improper Authentication vulnerability in Progress MOVEit Gateway (SFTP modules) allows Authentication Bypass.This issue affects MOVEit Gateway: 2024.0.0. | 2024-06-25 | | |
| Progress--MOVEit Transfer | Improper Authentication vulnerability in Progress MOVEit Transfer (SFTP module) can lead to Authentication Bypass.This issue affects MOVEit Transfer: from 2023.0.0 before 2023.0.11, from 2023.1.0 before 2023.1.6, from 2024.0.0 before 2024.0.2. | 2024-06-25 | | |
| PTC--Creo Elements/Direct License | PTC Creo Elements/Direct License Server exposes a web interface which can be used by unauthenticated remote attackers to execute arbitrary OS commands on the server. | 2024-06-27 | | |
| renesas -- rcar_gen3 | Incorrect Calculation vulnerability in Renesas arm-trusted-firmware allows Local Execution of Code. When checking whether a new image invades/overlaps with a previously loaded image the code neglects to consider a few cases. that could An attacker to bypass memory range restriction and overwrite an already loaded image partly or completely, which could result in code execution and bypass of secure boot. | 2024-06-24 | | |
| Salon Booking System--Salon booking system | Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') vulnerability in Salon Booking System Salon booking system allows File Manipulation.This issue affects Salon booking system: from n/a through 9.9. | 2024-06-24 | | |
| scidsg--hushline | Hush Line is a free and open-source, anonymous-tip-line-as-a-service for organizations or individuals. There is a stored XSS in the Inbox. The input is displayed using the `safe` Jinja2 attribute, and thus not sanitized upon display. This issue has been patched in version 0.1.0. | 2024-06-28 | | |
| scidsg--hushline | Hush Line is a free and open-source, anonymous-tip-line-as-a-service for organizations or individuals. The TOTP authentication flow has multiple issues that weakens its one-time nature. Specifically, the lack of 2FA for changing security settings allows attacker with CSRF or XSS primitives to change such settings without user interaction and credentials are required. This vulnerability has been patched in version 0.10. | 2024-06-27 | | |
| silabs.com--Ember ZNet SDK | An unauthenticated IEEE 802.15.4 'co-ordinator realignment' packet can be used to force Zigbee nodes to change their network identifier (pan ID), leading to a denial of service. This packet type is not useful in production and should be used only for PHY qualification. | 2024-06-27 | | |
| SoftEtherVPN--SoftEtherVPN | SoftEtherVPN is a an open-source cross-platform multi-protocol VPN Program. When SoftEtherVPN is deployed with L2TP enabled on a device, it introduces the possibility of the host being used for amplification/reflection traffic generation because it will respond to every packet with two response packets that are larger than the request packet size. These sorts of techniques are used by external actors who generate spoofed source IPs to target a destination on the internet. This vulnerability has been patched in version 5.02.5185. | 2024-06-26 | | |
| Spotfire--Spotfire Analyst | Vulnerability in Spotfire Spotfire Analyst, Spotfire Spotfire Server, Spotfire Spotfire for AWS Marketplace allows In the case of the installed Windows client: Successful execution of this vulnerability will result in an attacker being able to run arbitrary code.This requires human interaction from a person other than the attacker., In the case of the Web player (Business Author): Successful execution of this vulnerability via the Web Player, will result in the attacker being able to run arbitrary code as the account running the Web player process, In the case of Automation Services: Successful execution of this vulnerability will result in an attacker being able to run arbitrary code via Automation Services..This issue affects Spotfire Analyst: from 12.0.9 through 12.5.0, from 14.0 through 14.0.2; Spotfire Server: from 12.0.10 through 12.5.0, from 14.0 through 14.0.3, from 14.2.0 through 14.3.0; Spotfire for AWS Marketplace: from 14.0 before 14.3.0. | 2024-06-27 | | |
| stiofansisland--UsersWP Front-end login form, User Registration, User Profile & Members Directory plugin for WordPress | The UsersWP - Front-end login form, User Registration, User Profile & Members Directory plugin for WordPress plugin for WordPress is vulnerable to time-based SQL Injection via the 'uwp_sort_by' parameter in all versions up to, and including, 1.2.10 due to insufficient escaping on the user supplied parameter and lack of sufficient preparation on the existing SQL query. This makes it possible for unauthenticated attackers to append additional SQL queries into already existing queries that can be used to extract sensitive information from the database. | 2024-06-29 | | |
| StylemixThemes--Consulting Elementor Widgets | Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') vulnerability in StylemixThemes Consulting Elementor Widgets allows PHP Local File Inclusion.This issue affects Consulting Elementor Widgets: from n/a through 1.3.0. | 2024-06-24 | | |
| StylemixThemes--Consulting Elementor Widgets | Improper Neutralization of Special Elements used in a Command ('Command Injection') vulnerability in StylemixThemes Consulting Elementor Widgets allows OS Command Injection.This issue affects Consulting Elementor Widgets: from n/a through 1.3.0. | 2024-06-24 | | |
| StylemixThemes--Consulting Elementor Widgets | Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') vulnerability in StylemixThemes Consulting Elementor Widgets allows PHP Local File Inclusion.This issue affects Consulting Elementor Widgets: from n/a through 1.3.0. | 2024-06-24 | | |
| Synology--Camera Firmware | A vulnerability regarding buffer copy without checking size of input ('Classic Buffer Overflow') is found in the libjansson component and it does not affect the upstream library. This allows remote attackers to execute arbitrary code via unspecified vectors. The following models with Synology Camera Firmware versions before 1.0.7-0298 may be affected: BC500 and TC500. | 2024-06-28 | | |
| Synology--Camera Firmware | A vulnerability regarding improper neutralization of special elements used in an OS command ('OS Command Injection') is found in the IP block functionality. This allows remote authenticated users with administrator privileges to execute arbitrary commands via unspecified vectors. The following models with Synology Camera Firmware versions before 1.0.7-0298 may be affected: BC500 and TC500. | 2024-06-28 | | |
| Synology--Camera Firmware | A vulnerability regarding authentication bypass by spoofing is found in the RTSP functionality. This allows man-in-the-middle attackers to obtain privileges without consent via unspecified vectors. The following models with Synology Camera Firmware versions before 1.0.7-0298 may be affected: BC500 and TC500. | 2024-06-28 | | |
| Synology--Camera Firmware | A vulnerability regarding improper neutralization of special elements used in an OS command ('OS Command Injection') is found in the NTP configuration. This allows remote authenticated users with administrator privileges to execute arbitrary commands via unspecified vectors. The following models with Synology Camera Firmware versions before 1.0.7-0298 may be affected: BC500 and TC500. | 2024-06-28 | | |
| Synology--Synology Router Manager (SRM) | Download of code without integrity check vulnerability in AirPrint functionality in Synology Router Manager (SRM) before 1.2.5-8227-11 and 1.3.1-9346-8 allows man-in-the-middle attackers to execute arbitrary code via unspecified vectors. | 2024-06-28 | | |
| Talya Informatics--Elektraweb | Reliance on Cookies without Validation and Integrity Checking vulnerability in Talya Informatics Elektraweb allows Session Credential Falsification through Manipulation, Accessing/Intercepting/Modifying HTTP Cookies, Manipulating Opaque Client-based Data Tokens.This issue affects Elektraweb: before v17.0.68. | 2024-06-27 | | |
| Talya Informatics--Elektraweb | Improper Access Control, Missing Authorization, Incorrect Authorization, Incorrect Permission Assignment for Critical Resource, Missing Authentication, Weak Authentication, Improper Restriction of Communication Channel to Intended Endpoints vulnerability in Talya Informatics Elektraweb allows Exploiting Incorrectly Configured Access Control Security Levels, Manipulating Web Input to File System Calls, Embedding Scripts within Scripts, Malicious Logic Insertion, Modification of Windows Service Configuration, Malicious Root Certificate, Intent Spoof, WebView Exposure, Data Injected During Configuration, Incomplete Data Deletion in a Multi-Tenant Environment, Install New Service, Modify Existing Service, Install Rootkit, Replace File Extension Handlers, Replace Trusted Executable, Modify Shared File, Add Malicious File to Shared Webroot, Run Software at Logon, Disable Security Software.This issue affects Elektraweb: before v17.0.68. | 2024-06-27 | | |
| Talya Informatics--Travel APPS | Authorization Bypass Through User-Controlled Key vulnerability in Talya Informatics Travel APPS allows Exploiting Incorrectly Configured Access Control Security Levels.This issue affects Travel APPS: before v17.0.68. | 2024-06-27 | | |
| The Conduit Contributors--Conduit | Missing authorization in Client-Server API in Conduit <=0.7.0, allowing for any alias to be removed and added to another room, which can be used for privilege escalation by moving the #admins alias to a room which they control, allowing them to run commands resetting passwords, siging json with the server's key, deactivating users, and more | 2024-06-25 | | |
| The Conduit Contributors--Conduit | Lack of privilege checking when processing a redaction in Conduit versions v0.6.0 and lower, allowing a local user to redact any message from users on the same server, given that they are able to send redaction events. | 2024-06-25 | | |
| themewinter--WPCafe Online Food Ordering, Restaurant Menu, Delivery, and Reservations for WooCommerce | The WPCafe - Online Food Ordering, Restaurant Menu, Delivery, and Reservations for WooCommerce plugin for WordPress is vulnerable to Local File Inclusion in all versions up to, and including, 2.2.25 via the reservation_extra_field shortcode parameter. This makes it possible for authenticated attackers, with Contributor-level access and above, to include remote files on the server, potentially resulting in code execution | 2024-06-25 | | |
| Tp-Link--ER7206 Omada Gigabit VPN Router | A leftover debug code vulnerability exists in the cli_server debug functionality of Tp-Link ER7206 Omada Gigabit VPN Router 1.4.1 Build 20240117 Rel.57421. A specially crafted series of network requests can lead to arbitrary command execution. An attacker can send a sequence of requests to trigger this vulnerability. | 2024-06-25 | | |
| tpm2-software--tpm2-tools | tpm2 is the source repository for the Trusted Platform Module (TPM2.0) tools. This vulnerability allows attackers to manipulate tpm2_checkquote outputs by altering the TPML_PCR_SELECTION in the PCR input file. As a result, digest values are incorrectly mapped to PCR slots and banks, providing a misleading picture of the TPM state. This issue has been patched in version 5.7. | 2024-06-28 | | |
| usbarmory--mxs-dcp | The NXP Data Co-Processor (DCP) is a built-in hardware module for specific NXP SoCs¹ that implements a dedicated AES cryptographic engine for encryption/decryption operations. The dcp_tool reference implementation included in the repository selected the test key, regardless of its `-t` argument. This issue has been patched in commit 26a7. | 2024-06-28 | | |
| virtosoftware -- sharepoint_bulk_file_download | An issue was discovered in VirtoSoftware Virto Bulk File Download 5.5.44 for SharePoint 2019. The Virto.SharePoint.FileDownloader/Api/Download.ashx isCompleted method allows arbitrary file download and deletion via absolute path traversal in the path parameter. | 2024-06-24 | | |
| VMware--Salt Project | A specially crafted url can be created which leads to a directory traversal in the salt file server. A malicious user can read an arbitrary file from a Salt master's filesystem. | 2024-06-27 | | |
| warfareplugins--Social Sharing Plugin Social Warfare | Several plugins for WordPress hosted on WordPress.org have been compromised and injected with malicious PHP scripts. A malicious threat actor compromised the source code of various plugins and injected code that exfiltrates database credentials and is used to create new, malicious, administrator users and send that data back to a server. Currently, not all plugins have been patched and we strongly recommend uninstalling the plugins for the time being and running a complete malware scan. | 2024-06-25 | | |
| wpeka-club--Cookie Consent for WP Cookie Consent, Consent Log, Cookie Scanner, Script Blocker (for GDPR, CCPA & ePrivacy) | The WP Cookie Consent ( for GDPR, CCPA & ePrivacy ) plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'Client-IP' header in all versions up to, and including, 3.2.0 due to insufficient input sanitization and output escaping. This makes it possible for unauthenticated attackers to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-26 | |
Back to top
Medium Vulnerabilities
| Primary Vendor -- Product | Description | Published | CVSS Score | Source & Patch Info |
|---|---|---|---|---|
| Adobe--Adobe Experience Manager | Adobe Experience Manager versions 6.5.20 and earlier are affected by a stored Cross-Site Scripting (XSS) vulnerability that could be abused by a low-privileged attacker to inject malicious scripts into vulnerable form fields. Malicious JavaScript may be executed in a victim's browser when they browse to the page containing the vulnerable field. | 2024-06-25 | | |
| Adobe--Adobe Experience Manager | Adobe Experience Manager versions 6.5.20 and earlier are affected by a stored Cross-Site Scripting (XSS) vulnerability that could be abused by a low-privileged attacker to inject malicious scripts into vulnerable form fields. Malicious JavaScript may be executed in a victim's browser when they browse to the page containing the vulnerable field. | 2024-06-25 | | |
| amans2k--Funnel Builder for WordPress by FunnelKit Customize WooCommerce Checkout Pages, Create Sales Funnels, Order Bumps & One Click Upsells | The Funnel Builder for WordPress by FunnelKit - Customize WooCommerce Checkout Pages, Create Sales Funnels, Order Bumps & One Click Upsells plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'mimes' parameter in all versions up to, and including, 3.3.1 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Author-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-29 | | |
| anchorcms -- anchor_cms | Cross Site Scripting vulnerability in Anchor CMS v.0.12.7 allows a remote attacker to execute arbitrary code via a crafted .pdf file. | 2024-06-24 | | |
| Automattic--WordPress | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Automattic WordPress allows Stored XSS.This issue affects WordPress: from 6.5 through 6.5.4, from 6.4 through 6.4.4, from 6.3 through 6.3.4, from 6.2 through 6.2.5, from 6.1 through 6.1.6, from 6.0 through 6.0.8, from 5.9 through 5.9.9. | 2024-06-25 | | |
| Automattic--WordPress | Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') vulnerability in Automattic WordPress allows Relative Path Traversal.This issue affects WordPress: from 6.5 through 6.5.4, from 6.4 through 6.4.4, from 6.3 through 6.3.4, from 6.2 through 6.2.5, from 6.1 through 6.1.6, from 6.0 through 6.0.8, from 5.9 through 5.9.9, from 5.8 through 5.8.9, from 5.7 through 5.7.11, from 5.6 through 5.6.13, from 5.5 through 5.5.14, from 5.4 through 5.4.15, from 5.3 through 5.3.17, from 5.2 through 5.2.20, from 5.1 through 5.1.18, from 5.0 through 5.0.21, from 4.9 through 4.9.25, from 4.8 through 4.8.24, from 4.7 through 4.7.28, from 4.6 through 4.6.28, from 4.5 through 4.5.31, from 4.4 through 4.4.32, from 4.3 through 4.3.33, from 4.2 through 4.2.37, from 4.1 through 4.1.40. | 2024-06-25 | | |
| awordpresslife--Portfolio Gallery Image Gallery Plugin | The Portfolio Gallery - Image Gallery Plugin plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's 'PFG' shortcode in all versions up to, and including, 1.6.4 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-27 | | |
| bdthemes--Ultimate Post Kit Addons For Elementor (Post Grid, Post Carousel, Post Slider, Category List, Post Tabs, Timeline, Post Ticker, Tag Cloud) | The Ultimate Post Kit Addons For Elementor - (Post Grid, Post Carousel, Post Slider, Category List, Post Tabs, Timeline, Post Ticker, Tag Cloud) plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'url' parameter within the Social Count (Static) widget in all versions up to, and including, 3.11.7 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-28 | | |
| berriai--berriai/litellm | berriai/litellm version 1.34.34 is vulnerable to improper access control in its team management functionality. This vulnerability allows attackers to perform unauthorized actions such as creating, updating, viewing, deleting, blocking, and unblocking any teams, as well as adding or deleting any member to or from any teams. The vulnerability stems from insufficient access control checks in various team management endpoints, enabling attackers to exploit these functionalities without proper authorization. | 2024-06-27 | | |
| bfintal--Stackable Page Builder Gutenberg Blocks | The Stackable - Page Builder Gutenberg Blocks plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'data-caption' parameter in all versions up to, and including, 3.13.1 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-28 | | |
| bhagirath25--Floating Social Buttons | The Floating Social Buttons plugin for WordPress is vulnerable to Cross-Site Request Forgery in all versions up to, and including, 1.5. This is due to missing or incorrect nonce validation on the floating_social_buttons_option() function. This makes it possible for unauthenticated attackers to update the plugins settings and inject malicious web scripts via a forged request granted they can trick a site administrator into performing an action such as clicking on a link. | 2024-06-29 | | |
| bigbluebutton--bigbluebutton | BigBlueButton is an open-source virtual classroom designed to help teachers teach and learners learn. An attacker with a valid join link to a meeting can trick BigBlueButton into generating a signed join link with additional parameters. One of those parameters may be "role=moderator", allowing an attacker to join a meeting as moderator using a join link that was originally created for viewer access. This vulnerability has been patched in version(s) 2.6.18, 2.7.8 and 3.0.0-alpha.7. | 2024-06-28 | | |
| Blossom Themes--BlossomThemes Email Newsletter | Server-Side Request Forgery (SSRF) vulnerability in Blossom Themes BlossomThemes Email Newsletter.This issue affects BlossomThemes Email Newsletter: from n/a through 2.2.6. | 2024-06-26 | | |
| brechtvds--Easy Affiliate Links | The Easy Affiliate Links plugin for WordPress is vulnerable to unauthorized modification of data due to a missing capability check on the eafl_reset_settings AJAX action in all versions up to, and including, 3.7.3. This makes it possible for authenticated attackers, with Subscriber-level access and above, to reset the plugin's settings. | 2024-06-28 | | |
| brechtvds--Easy Image Collage | The Easy Image Collage plugin for WordPress is vulnerable to unauthorized loss of data due to a missing capability check on the ajax_image_collage() function in all versions up to, and including, 1.13.5. This makes it possible for authenticated attackers, with Contributor-level access and above, to erase all of the content in arbitrary posts. | 2024-06-28 | | |
| britner--Gutenberg Blocks with AI by Kadence WP Page Builder Features | The Gutenberg Blocks with AI by Kadence WP - Page Builder Features plugin for WordPress is vulnerable to DOM-based Stored Cross-Site Scripting via HTML data attributes in all versions up to, and including, 3.2.45 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-29 | | |
| Brocade--Fabric OS | A vulnerability in a password management API in Brocade Fabric OS versions before v9.2.1, v9.2.0b, v9.1.1d, and v8.2.3e prints sensitive information in log files. This could allow an authenticated user to view the server passwords for protocols such as scp and sftp. Detail. When the firmwaredownload command is incorrectly entered or points to an erroneous file, the firmware download log captures the failed command, including any password entered in the command line. | 2024-06-26 | | |
| Brocade--Fabric OS | A vulnerability in the web interface in Brocade Fabric OS before v9.2.1, v9.2.0b, and v9.1.1d prints encoded session passwords on session storage for Virtual Fabric platforms. This could allow an authenticated user to view other users' session encoded passwords. | 2024-06-26 | | |
| Canonical Ltd.--Ubuntu Advantage Desktop Pro | Marco Trevisan discovered that the Ubuntu Advantage Desktop Daemon, before version 1.12, leaks the Pro token to unprivileged users by passing the token as an argument in plaintext. | 2024-06-27 | | |
| carlosfazenda--Page and Post Clone | The Page and Post Clone plugin for WordPress is vulnerable to Insecure Direct Object Reference in all versions up to, and including, 6.0 via the 'content_clone' function due to missing validation on a user controlled key. This makes it possible for authenticated attackers, with Author-level access and above, to clone and read private posts. | 2024-06-29 | | |
| Checkmk GmbH--Checkmk | Stored XSS in some confirmation pop-ups in Checkmk before versions 2.3.0p7 and 2.2.0p28 allows Checkmk users to execute arbitrary scripts by injecting HTML elements into some user input fields that are shown in a confirmation pop-up. | 2024-06-25 | | |
| Checkmk GmbH--Checkmk | Stored XSS in the Crash Report page in Checkmk before versions 2.3.0p7, 2.2.0p28, 2.1.0p45, and 2.0.0 (EOL) allows users with permission to change Global Settings to execute arbitrary scripts by injecting HTML elements into the Crash Report URL in the Global Settings. | 2024-06-25 | | |
| CryoutCreations--Anima | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in CryoutCreations Anima allows Stored XSS.This issue affects Anima: from n/a through 1.4.1. | 2024-06-26 | | |
| Dell--PowerEdge Platform | Dell PowerEdge Server BIOS contains an TOCTOU race condition vulnerability. A local low privileged attacker could potentially exploit this vulnerability to gain access to otherwise unauthorized resources. | 2024-06-25 | | |
| Dell--PowerProtect DD | Dell PowerProtect DD, versions prior to 8.0, LTS 7.13.1.0, LTS 7.10.1.30, LTS 7.7.5.40 contain a Server-Side Request Forgery (SSRF) vulnerability. A remote high privileged attacker could potentially exploit this vulnerability, leading to disclosure of information on the application or remote client. | 2024-06-26 | | |
| Dell--PowerProtect DD | Dell PowerProtect DD, versions prior to 8.0, LTS 7.13.1.0, LTS 7.10.1.30, LTS 7.7.5.40 contain an Improper Control of a Resource Through its Lifetime vulnerability in an admin operation. A remote low privileged attacker could potentially exploit this vulnerability, leading to temporary resource constraint of system application. Exploitation may lead to denial of service of the application. | 2024-06-26 | | |
| Dell--PowerProtect DD | Dell PowerProtect DD, versions prior to 8.0, LTS 7.13.1.0, LTS 7.10.1.30, LTS 7.7.5.40 contain a Stored Cross-Site Scripting Vulnerability. A remote high privileged attacker could potentially exploit this vulnerability, leading to the storage of malicious HTML or JavaScript codes in a trusted application data store. When a high privileged victim user accesses the data store through their browsers, the malicious code gets executed by the web browser in the context of the vulnerable web application. Exploitation may lead to information disclosure, session theft, or client-side request forgery | 2024-06-26 | | |
| Dell--PowerProtect DD | Dell PowerProtect Data Domain, versions prior to 7.13.0.0, LTS 7.7.5.40, LTS 7.10.1.30 contain an weak cryptographic algorithm vulnerability. A remote unauthenticated attacker could potentially exploit this vulnerability, leading to man-in-the-middle attack that exposes sensitive session information. | 2024-06-26 | | |
| Dell--PowerProtect DD | Dell Data Domain, versions prior to 7.13.0.0, LTS 7.7.5.30, LTS 7.10.1.20 contain an SQL Injection vulnerability. A local low privileged attacker could potentially exploit this vulnerability, leading to the execution of certain SQL commands on the application's backend database causing unauthorized access to application data. | 2024-06-26 | | |
| Dell--PowerProtect DD | Dell PowerProtect DD, versions prior to 8.0, LTS 7.13.1.0, LTS 7.10.1.30, LTS 7.7.5.40 on DDMC contain a relative path traversal vulnerability. A remote high privileged attacker could potentially exploit this vulnerability, leading to the application sending over an unauthorized file to the managed system. | 2024-06-26 | | |
| detheme -- dethemekit_for_elementor | The DethemeKit For Elementor plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the URL parameter of the De Gallery widget in all versions up to and including 2.1.5 due to insufficient input sanitization and output escaping on user-supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user clicks on the injected link. | 2024-06-27 | | |
| devitemsllc--HT Mega Absolute Addons For Elementor | The HT Mega - Absolute Addons For Elementor plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the Video player widget settings in all versions up to, and including, 2.5.5 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-26 | | |
| devitemsllc--HT Mega Absolute Addons For Elementor | The HT Mega - Absolute Addons For Elementor plugin for WordPress is vulnerable to Stored Cross-Site Scripting via multiple widgets in all versions up to, and including, 2.5.5 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-26 | | |
| Dream-Theme--The7 Website and eCommerce Builder for WordPress | The The7 - Website and eCommerce Builder for WordPress theme for WordPress is vulnerable to Stored Cross-Site Scripting via the 'url' attribute within the plugin's Icon and Heading widgets in all versions up to, and including, 11.13.0 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-25 | | |
| Enalean--tuleap | Tuleap is an Open Source Suite to improve management of software developments and collaboration. Users are able to see backlog items that they should not see. This issue has been patched in Tuleap Community Edition version 15.9.99.97. | 2024-06-25 | | |
| ericsson -- codechecker | CodeChecker is an analyzer tooling, defect database and viewer extension for the Clang Static Analyzer and Clang Tidy. Zip files uploaded to the server endpoint of `CodeChecker store` are not properly sanitized. An attacker, using a path traversal attack, can load and display files on the machine of `CodeChecker server`. The vulnerable endpoint is `/Default/v6.53/CodeCheckerService@massStoreRun`. The path traversal vulnerability allows reading data on the machine of the `CodeChecker server`, with the same permission level as the `CodeChecker server`. The attack requires a user account on the `CodeChecker server`, with permission to store to a server, and view the stored report. This vulnerability has been patched in version 6.23. | 2024-06-24 | | |
| everthemess--Goya | The Goya theme for WordPress is vulnerable to Reflected Cross-Site Scripting via the 'attra-color', 'attra-size', and 'product-cata' parameters in versions up to, and including, 1.0.8.7 due to insufficient input sanitization and output escaping. This makes it possible for unauthenticated attackers to inject arbitrary web scripts in pages that execute if they can successfully trick a user into performing an action such as clicking on a link. | 2024-06-29 | | |
| fastly--js-compute-runtime | @fastly/js-compute is a JavaScript SDK and runtime for building Fastly Compute applications. The implementation of several functions were determined to include a use-after-free bug. This bug could allow for unintended data loss if the result of the preceding functions were sent anywhere else, and often results in a guest trap causing services to return a 500. This bug has been fixed in version 3.16.0 of the `@fastly/js-compute` package. | 2024-06-26 | | |
| finesoft_project -- finesoft | Cross Site Scripting vulnerability in Hangzhou Meisoft Information Technology Co., Ltd. Finesoft v.8.0 and before allows a remote attacker to execute arbitrary code via a crafted script to the login.jsp parameter. | 2024-06-24 | | |
| finesoft_project -- finesoft | Hangzhou Meisoft Information Technology Co., Ltd. FineSoft <=8.0 is affected by Cross Site Scripting (XSS) which allows remote attackers to execute arbitrary code. Enter any account and password, click Login, the page will report an error, and a controllable parameter will appear at the URL:weburl. | 2024-06-24 | | |
| gallerycreator--Gallery Blocks with Lightbox. Image Gallery, (HTML5 video , YouTube, Vimeo) Video Gallery and Lightbox for native gallery | The Gallery Blocks with Lightbox. Image Gallery, (HTML5 video , YouTube, Vimeo) Video Gallery and Lightbox for native gallery plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'galleryID' and 'className' parameters in all versions up to, and including, 3.2.1 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-28 | | |
| Genexis--Tilgin Fiber Home Gateway HG1522 | A vulnerability was found in Genexis Tilgin Fiber Home Gateway HG1522 CSx000-01_09_01_12. It has been declared as problematic. Affected by this vulnerability is an unknown functionality of the file /status/product_info/. The manipulation of the argument product_info leads to cross site scripting. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-269755. NOTE: The vendor was contacted early about this disclosure but did not respond in any way. | 2024-06-26 | | |
| gitlab -- gitlab | An issue was discovered in GitLab CE/EE affecting all versions starting from 9.2 prior to 16.11.5, starting from 17.0 prior to 17.0.3, and starting from 17.1 prior to 17.1.1, with the processing logic for generating link in dependency files can lead to a regular expression DoS attack on the server | 2024-06-27 | | |
| gitlab -- gitlab | An issue was discovered in GitLab CE/EE affecting all versions starting from 16.7 prior to 16.11.5, starting from 17.0 prior to 17.0.3, and starting from 17.1 prior to 17.1.1, which allows private job artifacts can be accessed by any user. | 2024-06-27 | | |
| gitlab -- gitlab | Multiple Denial of Service (DoS) conditions has been discovered in GitLab CE/EE affecting all versions starting from 1.0 prior to 16.11.5, starting from 17.0 prior to 17.0.3, and starting from 17.1 prior to 17.1.1 which allowed an attacker to cause resource exhaustion via banzai pipeline. | 2024-06-27 | | |
| gitlab -- gitlab | An issue was discovered in GitLab CE/EE affecting all versions starting from 12.0 prior to 16.11.5, starting from 17.0 prior to 17.0.3, and starting from 17.1 prior to 17.1.1, which allows for an attacker to cause a denial of service using a crafted OpenAPI file. | 2024-06-27 | | |
| gitlab -- gitlab | An issue was discovered in GitLab CE/EE affecting all versions starting from 16.9 prior to 16.11.5, starting from 17.0 prior to 17.0.3, and starting from 17.1 prior to 17.1.1, which allows merge request title to be visible publicly despite being set as project members only. | 2024-06-27 | | |
| gitlab -- gitlab | An issue was discovered in GitLab CE/EE affecting all versions starting from 16.9 prior to 16.11.5, starting from 17.0 prior to 17.0.3, and starting from 17.1 prior to 17.1.1, where a stored XSS vulnerability could be imported from a project with malicious commit notes. | 2024-06-27 | | |
| gitlab -- gitlab | An issue was discovered in GitLab EE affecting all versions starting from 16.0 prior to 16.11.5, starting from 17.0 prior to 17.0.3, and starting from 17.1 prior to 17.1.1, which allows an attacker to access issues and epics without having an SSO session using Duo Chat. | 2024-06-27 | | |
| gitlab -- gitlab | An issue was discovered in GitLab CE/EE affecting all versions starting from 16.1 prior to 16.11.5, starting from 17.0 prior to 17.0.3, and starting from 17.1 prior to 17.1.1, which allows non-project member to promote key results to objectives. | 2024-06-27 | | |
| gitlab -- gitlab | An issue was discovered in GitLab CE/EE affecting all versions starting from 16.10 prior to 16.11.5, starting from 17.0 prior to 17.0.3, and starting from 17.1 prior to 17.1.1, which allows a project maintainer can delete the merge request approval policy via graphQL. | 2024-06-27 | | |
| h5p -- h5p | The Interactive Content WordPress plugin before 1.15.8 does not validate uploads which could allow a Contributors and above to update malicious SVG files, leading to Stored Cross-Site Scripting issues | 2024-06-27 | | |
| hashicorp -- retryablehttp | go-retryablehttp prior to 0.7.7 did not sanitize urls when writing them to its log file. This could lead to go-retryablehttp writing sensitive HTTP basic auth credentials to its log file. This vulnerability, CVE-2024-6104, was fixed in go-retryablehttp 0.7.7. | 2024-06-24 | | |
| HCL Software--Connections | HCL Connections is vulnerable to a cross-site scripting attack where an attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user which leads to executing malicious script code. This may let the attacker steal cookie-based authentication credentials and comprise user's account then launch other attacks. | 2024-06-25 | | |
| Hitachi--Hitachi Storage Provider for VMware vCenter | Incorrect Default Permissions vulnerability in Hitachi Storage Provider for VMware vCenter allows local users to read and write specific files.This issue affects Hitachi Storage Provider for VMware vCenter: from 3.1.0 before 3.7.4. | 2024-06-25 | | |
| IBM--Cloud Pak for Security | IBM Cloud Pak for Security (CP4S) 1.10.0.0 through 1.10.11.0 and IBM QRadar Software Suite 1.10.12.0 through 1.10.21.0 allows web pages to be stored locally which can be read by another user on the system. IBM X-Force ID: 233673. | 2024-06-28 | | |
| IBM--Cognos Analytics | IBM Cognos Analytics 11.2.0, 11.2.1, 11.2.2, 11.2.3, 11.2.4, 12.0.0, 12.0.1, and 12.0.2 is potentially vulnerable to cross site scripting (XSS). A remote attacker could execute malicious commands due to improper validation of column headings in Cognos Assistant. IBM X-Force ID: 282780. | 2024-06-28 | | |
| IBM--Cognos Analytics | IBM Cognos Analytics 11.2.0, 11.2.1, 11.2.2, 11.2.3, 11.2.4, 12.0.0, 12.0.1, and 12.0.2 is vulnerable to improper certificate validation when using the IBM Planning Analytics Data Source Connection. This could allow an attacker to spoof a trusted entity by interfering in the communication path between IBM Planning Analytics server and IBM Cognos Analytics server. IBM X-Force ID: 283364. | 2024-06-28 | | |
| IBM--MQ | IBM MQ Console 9.3 LTS and 9.3 CD could disclose could allow a remote attacker to obtain sensitive information when a detailed technical error message is returned in the browser. This information could be used in further attacks against the system. IBM X-Force ID: 292765. | 2024-06-28 | | |
| IBM--MQ | IBM MQ 9.3 LTS and 9.3 CD could allow a remote attacker to obtain sensitive information when a detailed technical error message is returned in the browser. This information could be used in further attacks against the system. IBM X-Force ID: 292766. | 2024-06-28 | | |
| IBM--MQ | IBM MQ 9.0 LTS, 9.1 LTS, 9.2 LTS, 9.3 LTS and 9.3 CD, in certain configurations, is vulnerable to a denial of service attack caused by an error processing messages when an API Exit using MQBUFMH is used. IBM X-Force ID: 290259. | 2024-06-28 | | |
| IBM--MQ | IBM MQ 9.0 LTS, 9.1 LTS, 9.2 LTS, 9.3 LTS, and 9.3 CD is vulnerable to a denial of service attack caused by an error applying configuration changes. IBM X-Force ID: 290335. | 2024-06-28 | | |
| IBM--Security Access Manager Docker | IBM Security Access Manager Docker 10.0.0.0 through 10.0.7.1 could disclose sensitive information to a local user to do improper permission controls. IBM X-Force ID: 261195. | 2024-06-27 | | |
| IBM--Security Access Manager Docker | IBM Security Access Manager Docker 10.0.0.0 through 10.0.7.1 uses weaker than expected cryptographic algorithms that could allow an attacker to decrypt highly sensitive information. IBM X-Force ID: 261198. | 2024-06-27 | | |
| IBM--Security Verify Access Docker | IBM Security Access Manager Docker 10.0.0.0 through 10.0.7.1 could allow a local user to possibly elevate their privileges due to sensitive configuration information being exposed. IBM X-Force ID: 292413. | 2024-06-28 | | |
| IBM--Security Verify Access Docker | IBM Security Access Manager Docker 10.0.0.0 through 10.0.7.1 could allow a local user to obtain sensitive information from the container due to incorrect default permissions. IBM X-Force ID: 292415. | 2024-06-28 | | |
| IBM--Security Verify Access | IBM Security Verify Access 10.0.0 through 10.0.7.1 could allow a local user to obtain sensitive information from trace logs. IBM X-Force ID: 252183. | 2024-06-27 | | |
| IBM--Security Verify Access | IBM Security Verify Access 10.0.0.0 through 10.0.7.1, under certain configurations, could allow an unauthenticated attacker to cause a denial of service due to asymmetric resource consumption. IBM X-Force ID: 287615. | 2024-06-27 | | |
| IBM--Sterling B2B Integrator Standard Edition | IBM Sterling B2B Integrator Standard Edition 6.0.0.0 through 6.2.0.2 is vulnerable to cross-site scripting. This vulnerability allows an authenticated user to embed arbitrary JavaScript code in the Web UI thus altering the intended functionality potentially leading to credentials disclosure within a trusted session. IBM X-Force ID: 265511. | 2024-06-27 | | |
| IBM--Sterling B2B Integrator Standard Edition | IBM Sterling B2B Integrator Standard Edition 6.1 and 6.2 does not restrict or incorrectly restricts frame objects or UI layers that belong to another application or domain, which can lead to user confusion about which interface the user is interacting with. IBM X-Force ID: 265508. | 2024-06-27 | | |
| IBM--Storage Defender - Resiliency Service | IBM Storage Defender - Resiliency Service 2.0.0 through 2.0.4 uses an inadequate account lockout setting that could allow an attacker on the network to brute force account credentials. IBM X-Force ID: 281678. | 2024-06-28 | | |
| IBM--Storage Defender - Resiliency Service | IBM Storage Defender - Resiliency Service 2.0.0 through 2.0.4 agent username and password error response discrepancy exposes product to brute force enumeration. IBM X-Force ID: 294869. | 2024-06-28 | | |
| IBM--WebSphere Application Server | IBM WebSphere Application Server 8.5 and 9.0 is vulnerable to cross-site scripting. This vulnerability allows a privileged user to embed arbitrary JavaScript code in the Web UI thus altering the intended functionality potentially leading to credentials disclosure within a trusted session. IBM X-Force ID: 292640. | 2024-06-27 | | |
| itsourcecode--Tailoring Management System | A vulnerability, which was classified as critical, was found in itsourcecode Tailoring Management System 1.0. This affects an unknown part of the file customeradd.php. The manipulation of the argument fullname/address/phonenumber/sex/email/city/comment leads to sql injection. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used. The identifier VDB-269805 was assigned to this vulnerability. | 2024-06-27 | | |
| kadencewp -- gutenberg_blocks_with_ai | The Gutenberg Blocks with AI by Kadence WP - Page Builder Features plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the Google Maps widget parameters in all versions up to, and including, 3.2.42 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-27 | | |
| kadencewp -- kadence_blocks_pro | The kadence-blocks-pro WordPress plugin before 2.3.8 does not prevent users with at least the contributor role using some of its shortcode's functionalities to leak arbitrary options from the database. | 2024-06-27 | | |
| lahirudanushka--School Management System | A vulnerability was found in lahirudanushka School Management System 1.0.0/1.0.1 and classified as critical. Affected by this issue is some unknown functionality of the file examresults-par.php of the component Exam Results Page. The manipulation of the argument sid leads to sql injection. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. The identifier of this vulnerability is VDB-269492. | 2024-06-24 | | |
| lahirudanushka--School Management System | A vulnerability classified as critical has been found in lahirudanushka School Management System 1.0.0/1.0.1. This affects an unknown part of the file /attendancelist.php of the component Attendance Report Page. The manipulation of the argument aid leads to sql injection. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-269487. | 2024-06-24 | | |
| lahirudanushka--School Management System | A vulnerability classified as critical was found in lahirudanushka School Management System 1.0.0/1.0.1. This vulnerability affects unknown code of the file parent.php of the component Parent Page. The manipulation of the argument update leads to sql injection. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. The identifier of this vulnerability is VDB-269488. | 2024-06-24 | | |
| lahirudanushka--School Management System | A vulnerability, which was classified as critical, has been found in lahirudanushka School Management System 1.0.0/1.0.1. This issue affects some unknown processing of the file teacher.php of the component Teacher Page. The manipulation of the argument update leads to sql injection. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used. The identifier VDB-269489 was assigned to this vulnerability. | 2024-06-24 | | |
| lahirudanushka--School Management System | A vulnerability, which was classified as critical, was found in lahirudanushka School Management System 1.0.0/1.0.1. Affected is an unknown function of the file student.php of the component Student Page. The manipulation of the argument update leads to sql injection. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used. VDB-269490 is the identifier assigned to this vulnerability. | 2024-06-24 | | |
| lahirudanushka--School Management System | A vulnerability has been found in lahirudanushka School Management System 1.0.0/1.0.1 and classified as critical. Affected by this vulnerability is an unknown functionality of the file subject.php of the component Subject Page. The manipulation of the argument update leads to sql injection. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-269491. | 2024-06-24 | | |
| linux -- linux_kernel | In the Linux kernel, the following vulnerability has been resolved: um: Add winch to winch_handlers before registering winch IRQ Registering a winch IRQ is racy, an interrupt may occur before the winch is added to the winch_handlers list. If that happens, register_winch_irq() adds to that list a winch that is scheduled to be (or has already been) freed, causing a panic later in winch_cleanup(). Avoid the race by adding the winch to the winch_handlers list before registering the IRQ, and rolling back if um_request_irq() fails. | 2024-06-24 | | |
| looswebstudio--SEO SIMPLE PACK | The SEO SIMPLE PACK plugin for WordPress is vulnerable to Information Exposure in all versions up to, and including, 3.2.1 via META description. This makes it possible for unauthenticated attackers to extract limited information about password protected posts. | 2024-06-28 | | |
| Magarsus Consultancy--SSO (Single Sign On) | URL Redirection to Untrusted Site ('Open Redirect') vulnerability in Magarsus Consultancy SSO (Single Sign On) allows Manipulating Hidden Fields.This issue affects SSO (Single Sign On): from 1.0 before 1.1. | 2024-06-26 | | |
| ManageEngine--OpManager | Zoho ManageEngine ITOM products versions from 128234 to 128248 are affected by the stored cross-site scripting vulnerability in the proxy server option. | 2024-06-24 | | |
| matter-labs--era-compiler-vyper | ZKsync Era is a layer 2 rollup that uses zero-knowledge proofs to scale Ethereum. There is possible invalid stack access due to the addresses used to access the stack not properly being converted to cells. This issue has been patched in version 1.5.0. | 2024-06-28 | | |
| mediavine -- create | The Create by Mediavine plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's Schema Meta shortcode in all versions up to, and including, 1.9.7 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-27 | | |
| mermaid-js--zenuml-core | ZenUML is JavaScript-based diagramming tool that requires no server, using Markdown-inspired text definitions and a renderer to create and modify sequence diagrams. Markdown-based comments in the ZenUML diagram syntax are susceptible to Cross-site Scripting (XSS). The comment feature allows the user to attach small notes for reference. This feature allows the user to enter in their comment in markdown comment, allowing them to use common markdown features, such as `**` for bolded text. However, the markdown text is currently not sanitized before rendering, allowing an attacker to enter a malicious payload for the comment which leads to XSS. This puts existing applications that use ZenUML unsandboxed at risk of arbitrary JavaScript execution when rendering user-controlled diagrams. This vulnerability was patched in version 3.23.25, | 2024-06-26 | | |
| Mia Technology Inc.--Mia-Med Health Aplication | Use of a Broken or Risky Cryptographic Algorithm vulnerability in Mia Technology Inc. Mia-Med Health Aplication allows Signature Spoofing by Improper Validation.This issue affects Mia-Med Health Aplication: before 1.0.14. | 2024-06-24 | | |
| Moxa--OnCell G3150A-LTE Series | OnCell G3470A-LTE Series firmware versions v1.7.7 and prior have been identified as vulnerable due to accepting a format string from an external source as an argument. An attacker could modify an externally controlled format string to cause a memory leak and denial of service. | 2024-06-25 | | |
| n/a--djangorestframework | Versions of the package djangorestframework before 3.15.2 are vulnerable to Cross-site Scripting (XSS) via the break_long_headers template filter due to improper input sanitization before splitting and joining with <br> tags. | 2024-06-26 | | |
| n/a--ESXi | VMware ESXi contains an out-of-bounds read vulnerability. A malicious actor with local administrative privileges on a virtual machine with an existing snapshot may trigger an out-of-bounds read leading to a denial-of-service condition of the host. | 2024-06-25 | | |
| n/a--vCenter Server | The vCenter Server contains a denial-of-service vulnerability. A malicious actor with network access to vCenter Server may create a denial-of-service condition. | 2024-06-25 | | |
| N/A--VMware Cloud Director Object Storage Extension | VMware Cloud Director Object Storage Extension contains an Insertion of Sensitive Information vulnerability. A malicious actor with adjacent access to web/proxy server logging may be able to obtain sensitive information from URLs that are logged. | 2024-06-27 | | |
| N/A--VMware Cloud Director | VMware Cloud Director contains an Improper Privilege Management vulnerability. An authenticated tenant administrator for a given organization within VMware Cloud Director may be able to accidentally disable their organization leading to a Denial of Service for active sessions within their own organization's scope. | 2024-06-27 | | |
| n/a--VMware ESXi | VMware ESXi contains an authentication bypass vulnerability. A malicious actor with sufficient Active Directory (AD) permissions can gain full access to an ESXi host that was previously configured to use AD for user management https://blogs.vmware.com/vsphere/2012/09/joining-vsphere-hosts-to-active-directory.html by re-creating the configured AD group ('ESXi Admins' by default) after it was deleted from AD. | 2024-06-25 | | |
| N/A--VMware Workspace One UEM | VMware Workspace One UEM update addresses an information exposure vulnerability. A malicious actor with network access to the Workspace One UEM may be able to perform an attack resulting in an information exposure. | 2024-06-27 | | |
| nattywp--Silesia | The Silesia theme for WordPress is vulnerable to Stored Cross-Site Scripting via the 'link' attribute within the theme's Button shortcode in all versions up to, and including, 1.0.6 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-28 | | |
| netweblogic--Events Manager Calendar, Bookings, Tickets, and more! | The Events Manager - Calendar, Bookings, Tickets, and more! plugin for WordPress is vulnerable to Reflected Cross-Site Scripting via the 'country' parameter in all versions up to, and including, 6.4.8 due to insufficient input sanitization and output escaping. This makes it possible for unauthenticated attackers to inject arbitrary web scripts in pages that execute if they can successfully trick a user into performing an action such as clicking on a link. | 2024-06-29 | | |
| Next4Biz CRM & BPM Software--Business Process Manangement (BPM) | Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in Next4Biz CRM & BPM Software Business Process Manangement (BPM) allows Stored XSS.This issue affects Business Process Manangement (BPM): from 6.6.4.4 before 6.6.4.5. | 2024-06-24 | | |
| ninjateam -- wp_chat_app | The WP Chat App WordPress plugin before 3.6.5 does not sanitise and escape some of its settings, which could allow high privilege users such as admins to perform Cross-Site Scripting attacks even when unfiltered_html is disallowed. | 2024-06-27 | | |
| petesheppard84--Extensions for Elementor | The Extensions for Elementor plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'url' parameter within the EE Button widget in all versions up to, and including, 2.0.30 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-29 | | |
| Play.ht--Play.ht | Improper Authentication vulnerability in Play.Ht allows Accessing Functionality Not Properly Constrained by ACLs.This issue affects Play.Ht: from n/a through 3.6.4. | 2024-06-24 | | |
| posimyththemes--The Plus Addons for Elementor Elementor Addons, Page Templates, Widgets, Mega Menu, WooCommerce | The The Plus Addons for Elementor - Elementor Addons, Page Templates, Widgets, Mega Menu, WooCommerce plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'video_color' parameter in all versions up to, and including, 5.6.0 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-27 | | |
| Progress Software Corporation--WhatsUp Gold | In WhatsUp Gold versions released before 2023.1.3, a path traversal vulnerability exists. A specially crafted unauthenticated HTTP request to AppProfileImport can lead can lead to information disclosure. | 2024-06-25 | | |
| Progress Software Corporation--WhatsUp Gold | In WhatsUp Gold versions released before 2023.1.3, an unauthenticated Path Traversal vulnerability exists Wug.UI.Areas.Wug.Controllers.SessionController.LoadNMScript. This allows allows reading of any file from the applications web-root directory . | 2024-06-25 | | |
| Progress Software Corporation--WhatsUp Gold | In WhatsUp Gold versions released before 2023.1.3, an unauthenticated Arbitrary File Read issue exists in Wug.UI.Areas.Wug.Controllers.SessionController.CachedCSS. This vulnerability allows reading of any file with iisapppool\NmConsole privileges. | 2024-06-25 | | |
| ravichandra--Infinite | The Infinite theme for WordPress is vulnerable to Stored Cross-Site Scripting via the 'project_url' parameter in all versions up to, and including, 1.1.2 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-28 | | |
| renesas -- rcar_gen3 | Integer Underflow (Wrap or Wraparound) vulnerability in Renesas arm-trusted-firmware. An integer underflow in image range check calculations could lead to bypassing address restrictions and loading of images to unallowed addresses. | 2024-06-24 | | |
| rocklobster -- contact_form_7 | The Contact Form 7 WordPress plugin before 5.9.5 has an open redirect that allows an attacker to utilize a false URL and redirect to the URL of their choosing. | 2024-06-27 | | |
| scidsg--hushline | Hush Line is a free and open-source, anonymous-tip-line-as-a-service for organizations or individuals. The CSP policy applied on the `tips.hushline.app` website and bundled by default in this repository is trivial to bypass. This vulnerability has been patched in version 0.1.0. | 2024-06-28 | | |
| silabs.com--SiSDK | In a Silicon Labs multi-protocol gateway, a corrupt pointer to buffered data on a multi-protocol radio co-processor (RCP) causes the OpenThread Border Router(OTBR) application task running on the host platform to crash, allowing an attacker to cause a temporary denial-of-service. | 2024-06-27 | | |
| SourceCodester--Simple Online Bidding System | A vulnerability was found in SourceCodester Simple Online Bidding System 1.0. It has been classified as critical. This affects an unknown part of the file /admin/ajax.php?action=save_settings. The manipulation of the argument img leads to unrestricted upload. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used. The identifier VDB-269493 was assigned to this vulnerability. | 2024-06-24 | | |
| Spotfire--Spotfire Enterprise Runtime for R - Server Edition | Vulnerability in Spotfire Spotfire Enterprise Runtime for R - Server Edition, Spotfire Spotfire Statistics Services, Spotfire Spotfire Analyst, Spotfire Spotfire Desktop, Spotfire Spotfire Server allows The impact of this vulnerability depends on the privileges of the user running the affected software..This issue affects Spotfire Enterprise Runtime for R - Server Edition: from 1.12.7 through 1.20.0; Spotfire Statistics Services: from 12.0.7 through 12.3.1, from 14.0.0 through 14.3.0; Spotfire Analyst: from 12.0.9 through 12.5.0, from 14.0.0 through 14.3.0; Spotfire Desktop: from 14.0 through 14.3.0; Spotfire Server: from 12.0.10 through 12.5.0, from 14.0.0 through 14.3.0. | 2024-06-27 | | |
| squid-cache--squid | Squid is a caching proxy for the Web supporting HTTP, HTTPS, FTP, and more. Due to an Out-of-bounds Write error when assigning ESI variables, Squid is susceptible to a Memory Corruption error. This error can lead to a Denial of Service attack. | 2024-06-25 | | |
| Synology--Camera Firmware | A vulnerability regarding improper limitation of a pathname to a restricted directory ('Path Traversal') is found in the Language Settings functionality. This allows remote attackers to read specific files containing non-sensitive information via unspecified vectors. The following models with Synology Camera Firmware versions before 1.0.7-0298 may be affected: BC500 and TC500. | 2024-06-28 | | |
| Synology--Camera Firmware | A vulnerability regarding incorrect authorization is found in the firmware upgrade functionality. This allows remote authenticated users with administrator privileges to bypass firmware integrity check via unspecified vectors. The following models with Synology Camera Firmware versions before 1.0.7-0298 may be affected: BC500 and TC500. | 2024-06-28 | | |
| Synology--Synology Router Manager (SRM) | Incorrect default permissions vulnerability in firewall functionality in Synology Router Manager (SRM) before 1.2.5-8227-11 and 1.3.1-9346-8 allows man-in-the-middle attackers to access highly sensitive intranet resources via unspecified vectors. | 2024-06-28 | | |
| Talya Informatics--Travel APPS | Improper Access Control vulnerability in Talya Informatics Travel APPS allows Exploiting Incorrectly Configured Access Control Security Levels.This issue affects Travel APPS: before v17.0.68. | 2024-06-27 | | |
| tatvic--Conversios Google Analytics 4 (GA4), Google Ads, Meta Pixel & more for WooCommerce | The Conversios - Google Analytics 4 (GA4), Meta Pixel & more Via Google Tag Manager For WooCommerce plugin for WordPress is vulnerable to Reflected Cross-Site Scripting via the 'tiktok_user_id' parameter in all versions up to, and including, 7.0.12 due to insufficient input sanitization and output escaping. This makes it possible for unauthenticated attackers to inject arbitrary web scripts in pages that execute if they can successfully trick a user into performing an action such as clicking on a link. | 2024-06-28 | | |
| Tenda--A301 | A vulnerability classified as critical was found in Tenda A301 15.13.08.12. Affected by this vulnerability is the function fromSetWirelessRepeat of the file /goform/SetOnlineDevName. The manipulation of the argument devName leads to stack-based buffer overflow. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-269947. NOTE: The vendor was contacted early about this disclosure but did not respond in any way. | 2024-06-28 | | |
| Tenda--A301 | A vulnerability, which was classified as critical, has been found in Tenda A301 15.13.08.12. Affected by this issue is the function formWifiBasicSet of the file /goform/SetOnlineDevName. The manipulation of the argument devName leads to stack-based buffer overflow. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. The identifier of this vulnerability is VDB-269948. NOTE: The vendor was contacted early about this disclosure but did not respond in any way. | 2024-06-28 | | |
| The Conduit Contributors--Conduit | Lack of validation of origin in federation API in Conduit, allowing any remote server to impersonate any user from any server in most EDUs | 2024-06-25 | | |
| The Conduit Contributors--Conduit | Lack of consideration of key expiry when validating signatures in Conduit, allowing an attacker which has compromised an expired key to forge requests as the remote server, as well as PDUs with timestamps past the expiry date | 2024-06-25 | | |
| thehappymonster--Happy Addons for Elementor | The Happy Addons for Elementor plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'url' attribute within the plugin's Gradient Heading widget in all versions up to, and including, 3.11.1 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-29 | | |
| timstrifler--Exclusive Addons for Elementor | The Exclusive Addons for Elementor plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's Card widget in all versions up to, and including, 2.6.9.8 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-26 | | |
| tislam100--Scylla lite | The Scylla lite theme for WordPress is vulnerable to Stored Cross-Site Scripting via the 'url' parameter within the theme's Button shortcode in all versions up to, and including, 1.8.3 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-28 | | |
| tislam100--Theron Lite | The Theron Lite theme for WordPress is vulnerable to Stored Cross-Site Scripting via the 'url' parameter within the theme's Button shortcode in all versions up to, and including, 2.0 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-28 | | |
| tpm2-software--tpm2-tools | tpm2-tools is the source repository for the Trusted Platform Module (TPM2.0) tools. A malicious attacker can generate arbitrary quote data which is not detected by `tpm2 checkquote`. This issue was patched in version 5.7. | 2024-06-28 | | |
| tpm2-software--tpm2-tss | This repository hosts source code implementing the Trusted Computing Group's (TCG) TPM2 Software Stack (TSS). The JSON Quote Info returned by Fapi_Quote has to be deserialized by Fapi_VerifyQuote to the TPM Structure `TPMS_ATTEST`. For the field `TPM2_GENERATED magic` of this structure any number can be used in the JSON structure. The verifier can receive a state which does not represent the actual, possibly malicious state of the device under test. The malicious device might get access to data it shouldn't, or can use services it shouldn't be able to. This issue has been patched in version 4.1.0. | 2024-06-28 | | |
| trudesk_project -- trudesk | TruDesk Help Desk/Ticketing Solution v1.1.11 is vulnerable to a Cross-Site Request Forgery (CSRF) attack which would allow an attacker to restart the server, causing a DoS attack. The attacker must craft a webpage that would perform a GET request to the /api/v1/admin/restart endpoint, then the victim (who has sufficient privileges), would visit the page and the server restart would begin. The attacker must know the full URL that TruDesk is on in order to craft the webpage. | 2024-06-24 | | |
| twinpictures, baden03--jQuery T(-) Countdown Widget | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in twinpictures, baden03 jQuery T(-) Countdown Widget allows Stored XSS.This issue affects jQuery T(-) Countdown Widget: from n/a through 2.3.25. | 2024-06-26 | | |
| urkekg--Stock Ticker | The Stock Ticker plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's stock_ticker shortcode in all versions up to, and including, 3.24.4 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-29 | | |
| virtosoftware -- sharepoint_bulk_file_download | An issue was discovered in VirtoSoftware Virto Bulk File Download 5.5.44 for SharePoint 2019. It discloses full pathnames via Virto.SharePoint.FileDownloader/Api/Download.ashx?action=archive. | 2024-06-24 | | |
| virtosoftware -- sharepoint_bulk_file_download | An issue was discovered in VirtoSoftware Virto Bulk File Download 5.5.44 for SharePoint 2019. The Virto.SharePoint.FileDownloader/Api/Download.ashx isCompleted method allows an NTLMv2 hash leak via a UNC share pathname in the path parameter. | 2024-06-24 | | |
| VMware--Salt Project | Syndic cache directory creation is vulnerable to a directory traversal attack in salt project which can lead a malicious attacker to create an arbitrary directory on a Salt master. | 2024-06-27 | | |
| webtechstreet -- elementor_addon_elements | The Elementor Addon Elements plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'url' parameter in versions up to, and including, 1.13.5 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with contributor-level permissions and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-27 | | |
| webtechstreet -- elementor_addon_elements | The Elementor Addon Elements plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'url' parameter in versions up to, and including, 1.13.5 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with contributor-level permissions and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-27 | | |
| WordPress Foundation--WordPress | WordPress Core is vulnerable to Stored Cross-Site Scripting via the HTML API in various versions prior to 6.5.5 due to insufficient input sanitization and output escaping on URLs. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-25 | | |
| wpzita--Zita Elementor Site Library | The Zita Elementor Site Library plugin for WordPress is vulnerable to unauthorized modification of data due to a missing capability check on the import_xml_data, xml_data_import, import_option_data, import_widgets, and import_customizer_settings functions in all versions up to, and including, 1.6.2. This makes it possible for authenticated attackers, with subscriber-level access and above, to create pages, update certain options, including WooCommerce page titles and Elementor settings, import widgets, and update the plugin's customizer settings and the WordPress custom CSS. NOTE: This vulnerability was partially fixed in version 1.6.2. | 2024-06-25 | | |
| xwiki -- xwiki | XWiki Platform is a generic wiki platform offering runtime services for applications built on top of it. The content of a document included using `{{include reference="targetdocument"/}}` is executed with the right of the includer and not with the right of its author. This means that any user able to modify the target document can impersonate the author of the content which used the `include` macro. This vulnerability has been patched in XWiki 15.0 RC1 by making the default behavior safe. | 2024-06-24 | | |
| Yokogawa Electric Corporation--FAST/TOOLS | A vulnerability has been found in FAST/TOOLS and CI Server. The affected product's WEB HMI server's function to process HTTP requests has a security flaw (Reflected XSS) that allows the execution of malicious scripts. Therefore, if a client PC with inadequate security measures accesses a product URL containing a malicious request, the malicious script may be executed on the client PC. The affected products and versions are as follows: FAST/TOOLS (Packages: RVSVRN, UNSVRN, HMIWEB, FTEES, HMIMOB) R9.01 to R10.04 CI Server R1.01.00 to R1.03.00 | 2024-06-26 | | |
| Yokogawa Electric Corporation--FAST/TOOLS | A vulnerability has been found in FAST/TOOLS and CI Server. The affected products have built-in accounts with no passwords set. Therefore, if the product is operated without a password set by default, an attacker can break into the affected product. The affected products and versions are as follows: FAST/TOOLS (Packages: RVSVRN, UNSVRN, HMIWEB, FTEES, HMIMOB) R9.01 to R10.04 CI Server R1.01.00 to R1.03.00 | 2024-06-26 | |
Low Vulnerabilities
| Primary Vendor -- Product | Description | Published | CVSS Score | Source & Patch Info |
|---|---|---|---|---|
| bigbluebutton--bigbluebutton | BigBlueButton is an open-source virtual classroom designed to help teachers teach and learners learn. An attacker may be able to exploit the overly elevated file permissions in the `/usr/local/bigbluebutton/core/vendor/bundle/ruby/2.7.0/gems/resque-2.6.0` directory with the goal of privilege escalation, potentially exposing sensitive information on the server. This issue has been patched in version(s) 2.6.18, 2.7.8 and 3.0.0-alpha.7. | 2024-06-28 | | |
| Checkmk GmbH--Checkmk | Insertion of Sensitive Information into Log File in Checkmk GmbH's Checkmk versions <2.3.0p7, <2.2.0p28, <2.1.0p45 and <=2.0.0p39 (EOL) causes automation user secrets to be written to audit log files accessible to administrators. | 2024-06-26 | | |
| Dell--CloudLink | Dell Key Trust Platform, v3.0.6 and prior, contains Use of a Cryptographic Primitive with a Risky Implementation vulnerability. A local privileged attacker could potentially exploit this vulnerability, leading to privileged information disclosure. | 2024-06-28 | | |
| Dell--CPG BIOS | Dell Client Platform BIOS contains an Out-of-bounds Write vulnerability in an externally developed component. A high privileged attacker with local access could potentially exploit this vulnerability, leading to Information tampering. | 2024-06-25 | | |
| Dell--PowerProtect DD | Dell PowerProtect DD, versions prior to 8.0, LTS 7.13.1.0, LTS 7.10.1.30, LTS 7.7.5.40 contain an open redirect vulnerability. A remote low privileged attacker could potentially exploit this vulnerability, leading to information disclosure. | 2024-06-26 | | |
| Dell--PowerProtect DD | Dell PowerProtect DD, versions prior to 8.0, LTS 7.13.1.0, LTS 7.10.1.30, LTS 7.7.5.40 contain a disclosure of temporary sensitive information vulnerability. A remote high privileged attacker could potentially exploit this vulnerability, leading to the reuse of disclosed information to gain unauthorized access to the application report. | 2024-06-26 | | |
| DSpace--DSpace | DSpace is an open source software is a turnkey repository application used by more than 2,000 organizations and institutions worldwide to provide durable access to digital resources. In DSpace 7.0 through 7.6.1, when an HTML, XML or JavaScript Bitstream is downloaded, the user's browser may execute any embedded JavaScript. If that embedded JavaScript is malicious, there is a risk of an XSS attack. This vulnerability has been patched in version 7.6.2. | 2024-06-26 | | |
| HCL Software--Connections | HCL Connections contains a broken access control vulnerability that may allow unauthorized user to update data in certain scenarios. | 2024-06-25 | | |
| HCL Software--DRYiCE AEX | HCL DRYiCE AEX is impacted by a lack of clickjacking protection in the AEX web application. An attacker can use multiple transparent or opaque layers to trick a user into clicking on a button or link on another page than the one intended. | 2024-06-28 | | |
| HCL Software--DRYiCE AEX | HCL DRYiCE AEX product is impacted by lack of input validation vulnerability in a particular web application. A malicious script can be injected into a system which can cause the system to behave in unexpected ways. | 2024-06-28 | | |
| HCL Software--DRYiCE AEX | HCL DRYiCE AEX product is impacted by Missing Root Detection vulnerability in the mobile application. The mobile app can be installed in the rooted device due to which malicious users can gain unauthorized access to the rooted devices, compromising security and potentially leading to data breaches or other malicious activities. | 2024-06-28 | | |
| HCL Software--DRYiCE AEX | HCL DRYiCE AEX is potentially impacted by disclosure of sensitive information in the mobile application when a snapshot is taken. | 2024-06-28 | | |
| Kareadita--Kavita | Kavita is a cross platform reading server. Opening an ebook with malicious scripts inside leads to code execution inside the browsing context. Kavita doesn't sanitize or sandbox the contents of epubs, allowing scripts inside ebooks to execute. This vulnerability was patched in version 0.8.1. | 2024-06-28 | | |
| LabVantage--LIMS | A vulnerability was found in LabVantage LIMS 2017. It has been declared as problematic. This vulnerability affects unknown code of the file /labvantage/rc?command=file&file=WEB-CORE/elements/files/filesembedded.jsp of the component POST Request Handler. The manipulation of the argument sdcid/keyid1/keyid2/keyid3 leads to cross site scripting. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. The identifier of this vulnerability is VDB-269800. NOTE: The vendor was contacted early about this disclosure but did not respond in any way. | 2024-06-27 | | |
| LabVantage--LIMS | A vulnerability was found in LabVantage LIMS 2017. It has been rated as problematic. This issue affects some unknown processing of the file /labvantage/rc?command=page of the component POST Request Handler. The manipulation of the argument param1 leads to cross site scripting. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used. The identifier VDB-269801 was assigned to this vulnerability. NOTE: The vendor was contacted early about this disclosure but did not respond in any way. | 2024-06-27 | | |
| LabVantage--LIMS | A vulnerability classified as problematic has been found in LabVantage LIMS 2017. Affected is an unknown function of the file /labvantage/rc?command=page&sdcid=LV_ReagentLot of the component POST Request Handler. The manipulation of the argument mode leads to cross site scripting. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used. VDB-269802 is the identifier assigned to this vulnerability. | 2024-06-27 | | |
| LabVantage--LIMS | A vulnerability classified as problematic was found in LabVantage LIMS 2017. Affected by this vulnerability is an unknown functionality of the file /labvantage/rc?command=file&file=WEB-OPAL/pagetypes/bulletins/sendbulletin.jsp of the component POST Request Handler. The manipulation of the argument bulletinbody leads to cross site scripting. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-269803. | 2024-06-27 | | |
| lahirudanushka--School Management System | A vulnerability was found in lahirudanushka School Management System 1.0.0/1.0.1 and classified as problematic. This issue affects some unknown processing of the file /subject.php of the component Subject Page. The manipulation of the argument Subject Title/Sybillus Details leads to cross site scripting. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-269807. | 2024-06-27 | | |
| NixOS--nix | Nix is a package manager for Linux and other Unix systems that makes package management reliable and reproducible. A build process has access to and can change the permissions of the build directory. After creating a setuid binary in a globally accessible location, a malicious local user can assume the permissions of a Nix daemon worker and hijack all future builds. This issue was patched in version(s) 2.23.1, 2.22.2, 2.21.3, 2.20.7, 2.19.5 and 2.18.4. | 2024-06-28 | | |
| octobercms--october | October is a self-hosted CMS platform based on the Laravel PHP Framework. This issue affects authenticated administrators who may be redirected to an untrusted URL using the PageFinder schema. The resolver for the page finder link schema (`october://`) allowed external links, therefore allowing an open redirect outside the scope of the active host. This vulnerability has been patched in version 3.5.15. | 2024-06-26 | | |
| octobercms--october | October is a self-hosted CMS platform based on the Laravel PHP Framework. The X-October-Request-Handler Header does not sanitize the AJAX handler name and allows unescaped HTML to be reflected back. There is no impact since this vulnerability cannot be exploited through normal browser interactions. This unescaped value is only detectable when using a proxy interception tool. This issue has been patched in version 3.5.15. | 2024-06-26 | | |
| The Conduit Contributors--Conduit | Incomplete cleanup when performing redactions in Conduit, allowing an attacker to check whether certain strings were present in the PDU before redaction | 2024-06-25 | | |
| udn--udn News App | udn News Android APP stores the user session in logcat file when user log into the APP. A malicious APP or an attacker with physical access to the Android device can retrieve this session and use it to log into the news APP and other services provided by udn. | 2024-06-25 | | |
| udn--udn News App | udn News Android APP stores the unencrypted user session in the local database when user log into the application. A malicious APP or an attacker with physical access to the Android device can retrieve this session and use it to log into the news APP and other services provided by udn. | 2024-06-25 | | |
| ZKTeco--ZKBio CVSecurity V5000 | A vulnerability, which was classified as problematic, was found in ZKTeco ZKBio CVSecurity V5000 4.1.0. This affects an unknown part of the component Push Configuration Section. The manipulation of the argument Configuration Name leads to cross site scripting. It is possible to initiate the attack remotely. The identifier VDB-269733 was assigned to this vulnerability. NOTE: The vendor was contacted early about this disclosure but did not respond in any way. | 2024-06-26 | |
Severity Not Yet Assigned
| Primary Vendor -- Product | Description | Published | CVSS Score | Source & Patch Info |
|---|---|---|---|---|
| Adminer--Adminer | Adminer and AdminerEvo are vulnerable to SSRF via database connection fields. This could allow an unauthenticated remote attacker to enumerate or access systems the attacker would not otherwise have access to. Adminer is no longer supported, but this issue was fixed in AdminerEvo version 4.8.4. | 2024-06-24 | not yet calculated | |
| Adminer--Adminer | Adminer and AdminerEvo allow an unauthenticated remote attacker to cause a denial of service by connecting to an attacker-controlled service that responds with HTTP redirects. The denial of service is subject to PHP configuration limits. Adminer is no longer supported, but this issue was fixed in AdminerEvo version 4.8.4. | 2024-06-24 | not yet calculated | |
| Apache Software Foundation--Apache JSPWiki | XSS in Upload page in Apache JSPWiki 2.12.1 and priors allows the attacker to execute javascript in the victim's browser and get some sensitive information about the victim. Apache JSPWiki users should upgrade to 2.12.2 or later. | 2024-06-24 | not yet calculated | |
| Apache Software Foundation--Apache StreamPipes | Use of Cryptographically Weak Pseudo-Random Number Generator (PRNG) vulnerability in Apache StreamPipes user self-registration and password recovery mechanism. This allows an attacker to guess the recovery token in a reasonable time and thereby to take over the attacked user's account. This issue affects Apache StreamPipes: from 0.69.0 through 0.93.0. Users are recommended to upgrade to version 0.95.0, which fixes the issue. | 2024-06-24 | not yet calculated | |
| Apple--AirPods Firmware Update A, AirPods Firmware Update F, and Beats Firmware Update F | An authentication issue was addressed with improved state management. This issue is fixed in AirPods Firmware Update 6A326, AirPods Firmware Update 6F8, and Beats Firmware Update 6F8. When your headphones are seeking a connection request to one of your previously paired devices, an attacker in Bluetooth range might be able to spoof the intended source device and gain access to your headphones. | 2024-06-26 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted CATPART file, when parsed in CC5Dll.dll and ASMBASE228A.dll through Autodesk applications, can force an Out-of-Bound Write. A malicious actor can leverage this vulnerability to cause a crash, read sensitive data, or execute arbitrary code in the context of the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted PRT file, when parsed in opennurbs.dll through Autodesk applications, can force an Out-of-Bound Read. A malicious actor can leverage this vulnerability to cause a crash, read sensitive data, or execute arbitrary code in the context of the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted X_B and X_T file, when parsed in pskernel.DLL through Autodesk applications, can force an Out-of-Bound Write. A malicious actor can leverage this vulnerability to cause a crash, read sensitive data, or execute arbitrary code in the context of the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted CATPART, X_B and STEP, when parsed in ASMKERN228A.dll and ASMKERN229A.dll through Autodesk applications, can lead to a memory corruption vulnerability by write access violation. This vulnerability, in conjunction with other vulnerabilities, can lead to code execution in the context of the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted CATPRODUCT file, when parsed in CC5Dll.dll through Autodesk applications, can lead to a memory corruption vulnerability by write access violation. This vulnerability, in conjunction with other vulnerabilities, can lead to code execution in the context of the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted SLDDRW file, when parsed in ODXSW_DLL.dll through Autodesk applications, can force an Out-of-Bound Read. A malicious actor can leverage this vulnerability to cause a crash, read sensitive data, or execute arbitrary code in the context of the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted PRT file, when parsed in odxug_dll.dll through Autodesk applications, can force an Out-of-Bounds Write. A malicious actor can leverage this vulnerability to cause a crash, read sensitive data, or execute arbitrary code in the context of the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted 3DM file, when parsed in ASMkern229A.dll through Autodesk applications, can force an Out-of-Bounds Write. A malicious actor can leverage this vulnerability to cause a crash, read sensitive data, or execute arbitrary code in the context of the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted 3DM file, when parsed in opennurbs.dll through Autodesk applications, can force an Out-of-Bounds Read. A malicious actor can leverage this vulnerability to cause a crash, read sensitive data, or execute arbitrary code in the context of the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted MODEL file, when parsed in libodx.dll through Autodesk applications, can force an Out-of-Bounds Read. A malicious actor can leverage this vulnerability to cause a crash, read sensitive data, or execute arbitrary code in the context of the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted SLDPRT file, when parsed in ODXSW_DLL.dll through Autodesk applications, can be used to cause a Heap-based Overflow. A malicious actor can leverage this vulnerability to cause a crash, read sensitive data, or execute arbitrary code in the context of the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted MODEL file, when parsed in atf_asm_interface.dll through Autodesk applications, can be used to cause a Heap-based Buffer Overflow. A malicious actor can leverage this vulnerability to cause a crash or execute arbitrary code in the context of the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted 3DM file, when parsed in opennurbs.dll and ASMkern229A.dll through Autodesk applications, can lead to a memory corruption vulnerability by write access violation. This vulnerability, along with other vulnerabilities, can lead to code execution in the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted SLDASM or SLDPRT file, when parsed in ODXSW_DLL.dll through Autodesk applications, can lead to a memory corruption vulnerability by write access violation. This vulnerability, along with other vulnerabilities, can lead to code execution in the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted IGES file, when parsed in ASMImport229A.dll through Autodesk applications, can be used to cause a use-after-free vulnerability. A malicious actor can leverage this vulnerability to cause a crash or execute arbitrary code in the context of the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted STP file, when parsed in stp_aim_x64_vc15d.dll through Autodesk applications, can be used to uninitialized variables. This vulnerability, along with other vulnerabilities, can lead to code execution in the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted 3DM file, when parsed in opennurbs.dll through Autodesk applications, can force an Out-of-Bounds Write. A malicious actor can leverage this vulnerability to cause a crash, write sensitive data, or execute arbitrary code in the context of the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted X_B file, when parsed in pskernel.DLL through Autodesk applications, can lead to a memory corruption vulnerability by write access violation. This vulnerability, in conjunction with other vulnerabilities, can lead to code execution in the context of the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | [A maliciously crafted 3DM file, when parsed in opennurbs.dll through Autodesk applications, can be used to cause a Heap-based Overflow. A malicious actor can leverage this vulnerability to cause a crash, read sensitive data, or execute arbitrary code in the context of the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted MODEL file, when parsed in ASMkern229A.dllthrough Autodesk applications, can be used to uninitialized variables. This vulnerability, along with other vulnerabilities, could lead to code execution in the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted DWG and SLDPRT file, when parsed in opennurbs.dll and ODXSW_DLL.dll through Autodesk applications, can be used to cause a Stack-based Overflow. A malicious actor can leverage this vulnerability to cause a crash, read sensitive data, or execute arbitrary code in the context of the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted SLDPRT file, when parsed in ASMKERN229A.dll through Autodesk applications, can cause a use-after-free vulnerability. This vulnerability, along with other vulnerabilities, could lead to code execution in the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted X_B and X_T file, when parsed in pskernel.DLL through Autodesk applications, can force an Out-of-Bound Read. A malicious actor can leverage this vulnerability to cause a crash, read sensitive data, or execute arbitrary code in the context of the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted CATPRODUCT file, when parsed in CC5Dll.dll through Autodesk applications, can lead to a memory corruption vulnerability by write access violation. This vulnerability, in conjunction with other vulnerabilities, can lead to code execution in the context of the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--AutoCAD, Advance Steel and Civil 3D | A maliciously crafted X_B and X_T file, when parsed in pskernel.DLL through Autodesk applications, can cause a use-after-free vulnerability. This vulnerability, along with other vulnerabilities, could lead to code execution in the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--Autodesk applications | A maliciously crafted 3DM and MODEL file, when parsed in opennurbs.dll and atf_api.dll through Autodesk applications, can force an Out-of-Bound Read. A malicious actor can leverage this vulnerability to cause a crash, read sensitive data, or execute arbitrary code in the context of the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--Autodesk applications | A maliciously crafted MODEL file, when parsed in libodxdll through Autodesk applications, can cause a double free. This vulnerability, along with other vulnerabilities, can lead to code execution in the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--Autodesk applications | A maliciously crafted CATPART, STP, and MODEL file, when parsed in atf_dwg_consumer.dll, rose_x64_vc15.dll and libodxdll through Autodesk applications, can cause a use-after-free vulnerability. This vulnerability, along with other vulnerabilities, can lead to code execution in the current process. | 2024-06-25 | not yet calculated | |
| Autodesk--Autodesk applications | A maliciously crafted 3DM, MODEL and X_B file, when parsed in ASMkern229A.dll and ASMBASE229A.dll through Autodesk applications, can force an Out-of-Bound Read and/or Out-of-Bound Write. A malicious actor can leverage this vulnerability to cause a crash, read sensitive data, or execute arbitrary code in the context of the current process. | 2024-06-25 | not yet calculated | |
| berriai--berriai/litellm | BerriAI/litellm version v1.35.8 contains a vulnerability where an attacker can achieve remote code execution. The vulnerability exists in the `add_deployment` function, which decodes and decrypts environment variables from base64 and assigns them to `os.environ`. An attacker can exploit this by sending a malicious payload to the `/config/update` endpoint, which is then processed and executed by the server when the `get_secret` function is triggered. This requires the server to use Google KMS and a database to store a model. | 2024-06-27 | not yet calculated | |
| Bludit--Bludit | A security vulnerability has been identified in Bludit, allowing attackers with knowledge of the API token to upload arbitrary files through the File API which leads to arbitrary code execution on the server. This vulnerability arises from improper handling of file uploads, enabling malicious actors to upload and execute PHP files. | 2024-06-24 | not yet calculated | |
| Bludit--Bludit | A security vulnerability has been identified in Bludit, allowing authenticated attackers to execute arbitrary code through the Image API. This vulnerability arises from improper handling of file uploads, enabling malicious actors to upload and execute PHP files. | 2024-06-24 | not yet calculated | |
| Bludit--Bludit | A session fixation vulnerability in Bludit allows an attacker to bypass the server's authentication if they can trick an administrator or any other user into authorizing a session ID of their choosing. | 2024-06-24 | not yet calculated | |
| Bludit--Bludit | Bludit uses the SHA-1 hashing algorithm to compute password hashes. Thus, attackers could determine cleartext passwords with brute-force attacks due to the inherent speed of SHA-1. In addition, the salt that is computed by Bludit is generated with a non-cryptographically secure function. | 2024-06-24 | not yet calculated | |
| Bludit--Bludit | Bludit uses predictable methods in combination with the MD5 hashing algorithm to generate sensitive tokens such as the API token and the user token. This allows attackers to authenticate against the Bludit API. | 2024-06-24 | not yet calculated | |
| Concept Intermedia--S@M CMS | Sites managed in S@M CMS (Concept Intermedia) might be vulnerable to Reflected XSS via including scripts in requested file names. Only a part of observed services is vulnerable, but since vendor has not investigated the root problem, it is hard to determine when the issue appears. | 2024-06-28 | not yet calculated | |
| Concept Intermedia--S@M CMS | Sites managed in S@M CMS (Concept Intermedia) might be vulnerable to Reflected XSS via including scripts in one of GET header parameters. Only a part of observed services is vulnerable, but since vendor has not investigated the root problem, it is hard to determine when the issue appears. | 2024-06-28 | not yet calculated | |
| Concept Intermedia--S@M CMS | Sites managed in S@M CMS (Concept Intermedia) might be vulnerable to a blind SQL Injection executed using the search bar. Only a part of observed services is vulnerable, but since vendor has not investigated the root problem, it is hard to determine when the issue appears. | 2024-06-28 | not yet calculated | |
| Devolutions--Remote Desktop Manager | Improper access control in PAM dashboard in Devolutions Remote Desktop Manager 2024.2.11 and earlier on Windows allows an authenticated user to bypass the execute permission via the use of the PAM dashboard. | 2024-06-26 | not yet calculated | |
| Devolutions--Server | Authentication bypass in the 2FA feature in Devolutions Server 2024.1.14.0 and earlier allows an authenticated attacker to authenticate to another user without being asked for the 2FA via another browser tab. | 2024-06-25 | not yet calculated | |
| Faronics--WINSelect (Standard + Enterprise) | The application Faronics WINSelect (Standard + Enterprise) saves its configuration in an encrypted file on the file system which "Everyone" has read and write access to, path to file: C:\ProgramData\WINSelect\WINSelect.wsd The path for the affected WINSelect Enterprise configuration file is: C:\ProgramData\Faronics\StorageSpace\WS\WINSelect.wsd | 2024-06-24 | not yet calculated | |
| Faronics--WINSelect (Standard + Enterprise) | The configuration file is encrypted with a static key derived from a static five-character password which allows an attacker to decrypt this file. The application hashes this five-character password with the outdated and broken MD5 algorithm (no salt) and uses the first five bytes as the key for RC4. The configuration file is then encrypted with these parameters. | 2024-06-24 | not yet calculated | |
| Faronics--WINSelect (Standard + Enterprise) | The decrypted configuration file contains the password in cleartext which is used to configure WINSelect. It can be used to remove the existing restrictions and disable WINSelect entirely. | 2024-06-24 | not yet calculated | |
| gaizhenbiao--gaizhenbiao/chuanhuchatgpt | A Server-Side Request Forgery (SSRF) vulnerability exists in the upload processing interface of gaizhenbiao/ChuanhuChatGPT versions <= ChuanhuChatGPT-20240410-git.zip. This vulnerability allows attackers to send crafted requests from the vulnerable server to internal or external resources, potentially bypassing security controls and accessing sensitive data. | 2024-06-27 | not yet calculated | |
| gaizhenbiao--gaizhenbiao/chuanhuchatgpt | A Regular Expression Denial of Service (ReDoS) vulnerability exists in the latest version of gaizhenbiao/chuanhuchatgpt. The vulnerability is located in the filter_history function within the utils.py module. This function takes a user-provided keyword and attempts to match it against chat history filenames using a regular expression search. Due to the lack of sanitization or validation of the keyword parameter, an attacker can inject a specially crafted regular expression, leading to a denial of service condition. This can cause severe degradation of service performance and potential system unavailability. | 2024-06-27 | not yet calculated | |
| gaizhenbiao--gaizhenbiao/chuanhuchatgpt | A path traversal vulnerability exists in gaizhenbiao/chuanhuchatgpt version 20240410, allowing any user to delete other users' chat histories. This vulnerability can also be exploited to delete any files ending in `.json` on the target system, leading to a denial of service as users are unable to authenticate. | 2024-06-27 | not yet calculated | |
| golang.org/x/image--golang.org/x/image/tiff | Parsing a corrupt or malicious image with invalid color indices can cause a panic. | 2024-06-27 | not yet calculated | |
| Google--Chrome | Use after free in Dawn in Google Chrome prior to 126.0.6478.126 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. (Chromium security severity: High) | 2024-06-24 | not yet calculated | |
| Google--Chrome | Use after free in Swiftshader in Google Chrome prior to 126.0.6478.126 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. (Chromium security severity: High) | 2024-06-24 | not yet calculated | |
| Google--Chrome | Use after free in Dawn in Google Chrome prior to 126.0.6478.126 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. (Chromium security severity: High) | 2024-06-24 | not yet calculated | |
| Google--Chrome | Use after free in Dawn in Google Chrome prior to 126.0.6478.126 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. (Chromium security severity: High) | 2024-06-24 | not yet calculated | |
| Google--Nearby | There exists a vulnerability in Quickshare/Nearby where an attacker can force the a victim to stay connected to a temporary hotspot created for the share. As part of the sequence of packets in a QuickShare connection over Bluetooth, the attacker forces the victim to connect to the attacker's WiFi network and then sends an OfflineFrame that crashes Quick Share. This makes the Wifi connection to the attacker's network last instead of returning to the old network when the Quick Share session is done allowing the attacker to be a MiTM. We recommend upgrading to version 1.0.1724.0 of Quickshare or above | 2024-06-26 | not yet calculated | |
| Google--Nearby | There exists a vulnerability in Quickshare/Nearby where an attacker can bypass the accept file dialog on QuickShare Windows. Normally in QuickShare Windows app we can't send a file without the user accept from the receiving device if the visibility is set to everyone mode or contacts mode. We recommend upgrading to version 1.0.1724.0 of Quickshare or above | 2024-06-26 | not yet calculated | |
| h2oai--h2oai/h2o-3 | In h2oai/h2o-3 version 3.46.0, the `run_tool` command in the `rapids` component allows the `main` function of any class under the `water.tools` namespace to be called. One such class, `MojoConvertTool`, crashes the server when invoked with an invalid argument, causing a denial of service. | 2024-06-27 | not yet calculated | |
| Hanwha Vision Co., Ltd.--A-Series, Q-Series, PNM-series Camera | badmonkey, a Security Researcher has found a flaw that allows for a unauthenticated DoS attack on the camera. An attacker runs a crafted URL, nobody can access the web management page of the camera. and must manually restart the device or re-power it. The manufacturer has released patch firmware for the flaw, please refer to the manufacturer's report for details and workarounds. | 2024-06-25 | not yet calculated | |
| HP Inc.--HP PC BIOS | A potential Time-of-Check to Time-of Use (TOCTOU) vulnerability has been identified in the HP BIOS for certain HP PC products, which might allow arbitrary code execution, denial of service, and information disclosure. HP is releasing BIOS updates to mitigate the potential vulnerability. | 2024-06-28 | not yet calculated | |
| imartinez--imartinez/privategpt | A Cross-Site Request Forgery (CSRF) vulnerability in version 0.5.0 of imartinez/privategpt allows an attacker to delete all uploaded files on the server. This can lead to data loss and service disruption for the application's users. | 2024-06-27 | not yet calculated | |
| imartinez--imartinez/privategpt | An open redirect vulnerability exists in imartinez/privategpt version 0.5.0 due to improper handling of the 'file' parameter. This vulnerability allows attackers to redirect users to a URL specified by user-controlled input without proper validation or sanitization. The impact of this vulnerability includes potential phishing attacks, malware distribution, and credential theft. | 2024-06-27 | not yet calculated | |
| JAMF--Jamf Compliance Editor | The XPC service within the audit functionality of Jamf Compliance Editor before version 1.3.1 on macOS can lead to local privilege escalation. | 2024-06-27 | not yet calculated | |
| Jan Syski--MegaBIP | SQL Injection vulnerability in MegaBIP software allows attacker to disclose the contents of the database, obtain session cookies or modify the content of pages. This issue affects MegaBIP software versions through 5.12.1. | 2024-06-24 | not yet calculated | |
| Jenkins Project--Jenkins Bitbucket Branch Source Plugin | Jenkins Bitbucket Branch Source Plugin 886.v44cf5e4ecec5 and earlier prints the Bitbucket OAuth access token as part of the Bitbucket URL in the build log in some cases. | 2024-06-26 | not yet calculated | |
| Jenkins Project--Jenkins Plain Credentials Plugin | In rare cases Jenkins Plain Credentials Plugin 182.v468b_97b_9dcb_8 and earlier stores secret file credentials unencrypted (only Base64 encoded) on the Jenkins controller file system, where they can be viewed by users with access to the Jenkins controller file system (global credentials) or with Item/Extended Read permission (folder-scoped credentials). | 2024-06-26 | not yet calculated | |
| Jenkins Project--Jenkins Structs Plugin | When Jenkins Structs Plugin 337.v1b_04ea_4df7c8 and earlier fails to configure a build step, it logs a warning message containing diagnostic information that may contain secrets passed as step parameters, potentially resulting in accidental exposure of secrets through the default system log. | 2024-06-26 | not yet calculated | |
| lightning-ai--lightning-ai/pytorch-lightning | A vulnerability in the /v1/runs API endpoint of lightning-ai/pytorch-lightning v2.2.4 allows attackers to exploit path traversal when extracting tar.gz files. When the LightningApp is running with the plugin_server, attackers can deploy malicious tar.gz plugins that embed arbitrary files with path traversal vulnerabilities. This can result in arbitrary files being written to any directory in the victim's local file system, potentially leading to remote code execution. | 2024-06-27 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: x86/xen: Drop USERGS_SYSRET64 paravirt call commit afd30525a659ac0ae0904f0cb4a2ca75522c3123 upstream. USERGS_SYSRET64 is used to return from a syscall via SYSRET, but a Xen PV guest will nevertheless use the IRET hypercall, as there is no sysret PV hypercall defined. So instead of testing all the prerequisites for doing a sysret and then mangling the stack for Xen PV again for doing an iret just use the iret exit from the beginning. This can easily be done via an ALTERNATIVE like it is done for the sysenter compat case already. It should be noted that this drops the optimization in Xen for not restoring a few registers when returning to user mode, but it seems as if the saved instructions in the kernel more than compensate for this drop (a kernel build in a Xen PV guest was slightly faster with this patch applied). While at it remove the stale sysret32 remnants. [ pawan: Brad Spengler and Salvatore Bonaccorso <[email protected]> reported a problem with the 5.10 backport commit edc702b4a820 ("x86/entry_64: Add VERW just before userspace transition"). When CONFIG_PARAVIRT_XXL=y, CLEAR_CPU_BUFFERS is not executed in syscall_return_via_sysret path as USERGS_SYSRET64 is runtime patched to: .cpu_usergs_sysret64 = { 0x0f, 0x01, 0xf8, 0x48, 0x0f, 0x07 }, // swapgs; sysretq which is missing CLEAR_CPU_BUFFERS. It turns out dropping USERGS_SYSRET64 simplifies the code, allowing CLEAR_CPU_BUFFERS to be explicitly added to syscall_return_via_sysret path. Below is with CONFIG_PARAVIRT_XXL=y and this patch applied: syscall_return_via_sysret: ... <+342>: swapgs <+345>: xchg %ax,%ax <+347>: verw -0x1a2(%rip) <------ <+354>: sysretq ] | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: media: lgdt3306a: Add a check against null-pointer-def The driver should check whether the client provides the platform_data. The following log reveals it: [ 29.610324] BUG: KASAN: null-ptr-deref in kmemdup+0x30/0x40 [ 29.610730] Read of size 40 at addr 0000000000000000 by task bash/414 [ 29.612820] Call Trace: [ 29.613030] <TASK> [ 29.613201] dump_stack_lvl+0x56/0x6f [ 29.613496] ? kmemdup+0x30/0x40 [ 29.613754] print_report.cold+0x494/0x6b7 [ 29.614082] ? kmemdup+0x30/0x40 [ 29.614340] kasan_report+0x8a/0x190 [ 29.614628] ? kmemdup+0x30/0x40 [ 29.614888] kasan_check_range+0x14d/0x1d0 [ 29.615213] memcpy+0x20/0x60 [ 29.615454] kmemdup+0x30/0x40 [ 29.615700] lgdt3306a_probe+0x52/0x310 [ 29.616339] i2c_device_probe+0x951/0xa90 | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: media: ti: j721e-csi2rx: Fix races while restarting DMA After the frame is submitted to DMA, it may happen that the submitted list is not updated soon enough, and the DMA callback is triggered before that. This can lead to kernel crashes, so move everything in a single lock/unlock section to prevent such races. | 2024-06-24 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: f2fs: compress: don't allow unaligned truncation on released compress inode f2fs image may be corrupted after below testcase: - mkfs.f2fs -O extra_attr,compression -f /dev/vdb - mount /dev/vdb /mnt/f2fs - touch /mnt/f2fs/file - f2fs_io setflags compression /mnt/f2fs/file - dd if=/dev/zero of=/mnt/f2fs/file bs=4k count=4 - f2fs_io release_cblocks /mnt/f2fs/file - truncate -s 8192 /mnt/f2fs/file - umount /mnt/f2fs - fsck.f2fs /dev/vdb [ASSERT] (fsck_chk_inode_blk:1256) --> ino: 0x5 has i_blocks: 0x00000002, but has 0x3 blocks [FSCK] valid_block_count matching with CP [Fail] [0x4, 0x5] [FSCK] other corrupted bugs [Fail] The reason is: partial truncation assume compressed inode has reserved blocks, after partial truncation, valid block count may change w/o .i_blocks and .total_valid_block_count update, result in corruption. This patch only allow cluster size aligned truncation on released compress inode for fixing. | 2024-06-24 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: f2fs: compress: fix to cover {reserve,release}_compress_blocks() w/ cp_rwsem lock It needs to cover {reserve,release}_compress_blocks() w/ cp_rwsem lock to avoid racing with checkpoint, otherwise, filesystem metadata including blkaddr in dnode, inode fields and .total_valid_block_count may be corrupted after SPO case. | 2024-06-24 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: PCI: of_property: Return error for int_map allocation failure Return -ENOMEM from of_pci_prop_intr_map() if kcalloc() fails to prevent a NULL pointer dereference in this case. [bhelgaas: commit log] | 2024-06-24 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: fpga: region: add owner module and take its refcount The current implementation of the fpga region assumes that the low-level module registers a driver for the parent device and uses its owner pointer to take the module's refcount. This approach is problematic since it can lead to a null pointer dereference while attempting to get the region during programming if the parent device does not have a driver. To address this problem, add a module owner pointer to the fpga_region struct and use it to take the module's refcount. Modify the functions for registering a region to take an additional owner module parameter and rename them to avoid conflicts. Use the old function names for helper macros that automatically set the module that registers the region as the owner. This ensures compatibility with existing low-level control modules and reduces the chances of registering a region without setting the owner. Also, update the documentation to keep it consistent with the new interface for registering an fpga region. | 2024-06-24 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: fpga: bridge: add owner module and take its refcount The current implementation of the fpga bridge assumes that the low-level module registers a driver for the parent device and uses its owner pointer to take the module's refcount. This approach is problematic since it can lead to a null pointer dereference while attempting to get the bridge if the parent device does not have a driver. To address this problem, add a module owner pointer to the fpga_bridge struct and use it to take the module's refcount. Modify the function for registering a bridge to take an additional owner module parameter and rename it to avoid conflicts. Use the old function name for a helper macro that automatically sets the module that registers the bridge as the owner. This ensures compatibility with existing low-level control modules and reduces the chances of registering a bridge without setting the owner. Also, update the documentation to keep it consistent with the new interface for registering an fpga bridge. Other changes: opportunistically move put_device() from __fpga_bridge_get() to fpga_bridge_get() and of_fpga_bridge_get() to improve code clarity since the bridge device is taken in these functions. | 2024-06-24 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: fpga: manager: add owner module and take its refcount The current implementation of the fpga manager assumes that the low-level module registers a driver for the parent device and uses its owner pointer to take the module's refcount. This approach is problematic since it can lead to a null pointer dereference while attempting to get the manager if the parent device does not have a driver. To address this problem, add a module owner pointer to the fpga_manager struct and use it to take the module's refcount. Modify the functions for registering the manager to take an additional owner module parameter and rename them to avoid conflicts. Use the old function names for helper macros that automatically set the module that registers the manager as the owner. This ensures compatibility with existing low-level control modules and reduces the chances of registering a manager without setting the owner. Also, update the documentation to keep it consistent with the new interface for registering an fpga manager. Other changes: opportunistically move put_device() from __fpga_mgr_get() to fpga_mgr_get() and of_fpga_mgr_get() to improve code clarity since the manager device is taken in these functions. | 2024-06-24 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: drm/xe: Only use reserved BCS instances for usm migrate exec queue The GuC context scheduling queue is 2 entires deep, thus it is possible for a migration job to be stuck behind a fault if migration exec queue shares engines with user jobs. This can deadlock as the migrate exec queue is required to service page faults. Avoid deadlock by only using reserved BCS instances for usm migrate exec queue. (cherry picked from commit 04f4a70a183a688a60fe3882d6e4236ea02cfc67) | 2024-06-24 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: nilfs2: fix potential kernel bug due to lack of writeback flag waiting Destructive writes to a block device on which nilfs2 is mounted can cause a kernel bug in the folio/page writeback start routine or writeback end routine (__folio_start_writeback in the log below): kernel BUG at mm/page-writeback.c:3070! Oops: invalid opcode: 0000 [#1] PREEMPT SMP KASAN PTI ... RIP: 0010:__folio_start_writeback+0xbaa/0x10e0 Code: 25 ff 0f 00 00 0f 84 18 01 00 00 e8 40 ca c6 ff e9 17 f6 ff ff e8 36 ca c6 ff 4c 89 f7 48 c7 c6 80 c0 12 84 e8 e7 b3 0f 00 90 <0f> 0b e8 1f ca c6 ff 4c 89 f7 48 c7 c6 a0 c6 12 84 e8 d0 b3 0f 00 ... Call Trace: <TASK> nilfs_segctor_do_construct+0x4654/0x69d0 [nilfs2] nilfs_segctor_construct+0x181/0x6b0 [nilfs2] nilfs_segctor_thread+0x548/0x11c0 [nilfs2] kthread+0x2f0/0x390 ret_from_fork+0x4b/0x80 ret_from_fork_asm+0x1a/0x30 </TASK> This is because when the log writer starts a writeback for segment summary blocks or a super root block that use the backing device's page cache, it does not wait for the ongoing folio/page writeback, resulting in an inconsistent writeback state. Fix this issue by waiting for ongoing writebacks when putting folios/pages on the backing device into writeback state. | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: btrfs: fix crash on racing fsync and size-extending write into prealloc We have been seeing crashes on duplicate keys in btrfs_set_item_key_safe(): BTRFS critical (device vdb): slot 4 key (450 108 8192) new key (450 108 8192) ------------[ cut here ]------------ kernel BUG at fs/btrfs/ctree.c:2620! invalid opcode: 0000 [#1] PREEMPT SMP PTI CPU: 0 PID: 3139 Comm: xfs_io Kdump: loaded Not tainted 6.9.0 #6 Hardware name: QEMU Standard PC (i440FX + PIIX, 1996), BIOS 1.16.3-2.fc40 04/01/2014 RIP: 0010:btrfs_set_item_key_safe+0x11f/0x290 [btrfs] With the following stack trace: #0 btrfs_set_item_key_safe (fs/btrfs/ctree.c:2620:4) #1 btrfs_drop_extents (fs/btrfs/file.c:411:4) #2 log_one_extent (fs/btrfs/tree-log.c:4732:9) #3 btrfs_log_changed_extents (fs/btrfs/tree-log.c:4955:9) #4 btrfs_log_inode (fs/btrfs/tree-log.c:6626:9) #5 btrfs_log_inode_parent (fs/btrfs/tree-log.c:7070:8) #6 btrfs_log_dentry_safe (fs/btrfs/tree-log.c:7171:8) #7 btrfs_sync_file (fs/btrfs/file.c:1933:8) #8 vfs_fsync_range (fs/sync.c:188:9) #9 vfs_fsync (fs/sync.c:202:9) #10 do_fsync (fs/sync.c:212:9) #11 __do_sys_fdatasync (fs/sync.c:225:9) #12 __se_sys_fdatasync (fs/sync.c:223:1) #13 __x64_sys_fdatasync (fs/sync.c:223:1) #14 do_syscall_x64 (arch/x86/entry/common.c:52:14) #15 do_syscall_64 (arch/x86/entry/common.c:83:7) #16 entry_SYSCALL_64+0xaf/0x14c (arch/x86/entry/entry_64.S:121) So we're logging a changed extent from fsync, which is splitting an extent in the log tree. But this split part already exists in the tree, triggering the BUG(). This is the state of the log tree at the time of the crash, dumped with drgn (https://github.com/osandov/drgn/blob/main/contrib/btrfs_tree.py) to get more details than btrfs_print_leaf() gives us: >>> print_extent_buffer(prog.crashed_thread().stack_trace()[0]["eb"]) leaf 33439744 level 0 items 72 generation 9 owner 18446744073709551610 leaf 33439744 flags 0x100000000000000 fs uuid e5bd3946-400c-4223-8923-190ef1f18677 chunk uuid d58cb17e-6d02-494a-829a-18b7d8a399da item 0 key (450 INODE_ITEM 0) itemoff 16123 itemsize 160 generation 7 transid 9 size 8192 nbytes 8473563889606862198 block group 0 mode 100600 links 1 uid 0 gid 0 rdev 0 sequence 204 flags 0x10(PREALLOC) atime 1716417703.220000000 (2024-05-22 15:41:43) ctime 1716417704.983333333 (2024-05-22 15:41:44) mtime 1716417704.983333333 (2024-05-22 15:41:44) otime 17592186044416.000000000 (559444-03-08 01:40:16) item 1 key (450 INODE_REF 256) itemoff 16110 itemsize 13 index 195 namelen 3 name: 193 item 2 key (450 XATTR_ITEM 1640047104) itemoff 16073 itemsize 37 location key (0 UNKNOWN.0 0) type XATTR transid 7 data_len 1 name_len 6 name: user.a data a item 3 key (450 EXTENT_DATA 0) itemoff 16020 itemsize 53 generation 9 type 1 (regular) extent data disk byte 303144960 nr 12288 extent data offset 0 nr 4096 ram 12288 extent compression 0 (none) item 4 key (450 EXTENT_DATA 4096) itemoff 15967 itemsize 53 generation 9 type 2 (prealloc) prealloc data disk byte 303144960 nr 12288 prealloc data offset 4096 nr 8192 item 5 key (450 EXTENT_DATA 8192) itemoff 15914 itemsize 53 generation 9 type 2 (prealloc) prealloc data disk byte 303144960 nr 12288 prealloc data offset 8192 nr 4096 ... So the real problem happened earlier: notice that items 4 (4k-12k) and 5 (8k-12k) overlap. Both are prealloc extents. Item 4 straddles i_size and item 5 starts at i_size. Here is the state of ---truncated--- | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: btrfs: protect folio::private when attaching extent buffer folios [BUG] Since v6.8 there are rare kernel crashes reported by various people, the common factor is bad page status error messages like this: BUG: Bad page state in process kswapd0 pfn:d6e840 page: refcount:0 mapcount:0 mapping:000000007512f4f2 index:0x2796c2c7c pfn:0xd6e840 aops:btree_aops ino:1 flags: 0x17ffffe0000008(uptodate|node=0|zone=2|lastcpupid=0x3fffff) page_type: 0xffffffff() raw: 0017ffffe0000008 dead000000000100 dead000000000122 ffff88826d0be4c0 raw: 00000002796c2c7c 0000000000000000 00000000ffffffff 0000000000000000 page dumped because: non-NULL mapping [CAUSE] Commit 09e6cef19c9f ("btrfs: refactor alloc_extent_buffer() to allocate-then-attach method") changes the sequence when allocating a new extent buffer. Previously we always called grab_extent_buffer() under mapping->i_private_lock, to ensure the safety on modification on folio::private (which is a pointer to extent buffer for regular sectorsize). This can lead to the following race: Thread A is trying to allocate an extent buffer at bytenr X, with 4 4K pages, meanwhile thread B is trying to release the page at X + 4K (the second page of the extent buffer at X). Thread A | Thread B -----------------------------------+------------------------------------- | btree_release_folio() | | This is for the page at X + 4K, | | Not page X. | | alloc_extent_buffer() | |- release_extent_buffer() |- filemap_add_folio() for the | | |- atomic_dec_and_test(eb->refs) | page at bytenr X (the first | | | | page). | | | | Which returned -EEXIST. | | | | | | | |- filemap_lock_folio() | | | | Returned the first page locked. | | | | | | | |- grab_extent_buffer() | | | | |- atomic_inc_not_zero() | | | | | Returned false | | | | |- folio_detach_private() | | |- folio_detach_private() for X | |- folio_test_private() | | |- folio_test_private() | Returned true | | | Returned true |- folio_put() | |- folio_put() Now there are two puts on the same folio at folio X, leading to refcount underflow of the folio X, and eventually causing the BUG_ON() on the page->mapping. The condition is not that easy to hit: - The release must be triggered for the middle page of an eb If the release is on the same first page of an eb, page lock would kick in and prevent the race. - folio_detach_private() has a very small race window It's only between folio_test_private() and folio_clear_private(). That's exactly when mapping->i_private_lock is used to prevent such race, and commit 09e6cef19c9f ("btrfs: refactor alloc_extent_buffer() to allocate-then-attach method") screwed that up. At that time, I thought the page lock would kick in as filemap_release_folio() also requires the page to be locked, but forgot the filemap_release_folio() only locks one page, not all pages of an extent buffer. [FIX] Move all the code requiring i_private_lock into attach_eb_folio_to_filemap(), so that everything is done with proper lock protection. Furthermore to prevent future problems, add an extra lockdep_assert_locked() to ensure we're holding the proper lock. To reproducer that is able to hit the race (takes a few minutes with instrumented code inserting delays to alloc_extent_buffer()): #!/bin/sh drop_caches () { while(true); do echo 3 > /proc/sys/vm/drop_caches echo 1 > /proc/sys/vm/compact_memory done } run_tar () { while(true); do for x in `seq 1 80` ; do tar cf /dev/zero /mnt > /dev/null & done wait done } mkfs.btrfs -f -d single -m single ---truncated--- | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: blk-cgroup: fix list corruption from reorder of WRITE ->lqueued __blkcg_rstat_flush() can be run anytime, especially when blk_cgroup_bio_start is being executed. If WRITE of `->lqueued` is re-ordered with READ of 'bisc->lnode.next' in the loop of __blkcg_rstat_flush(), `next_bisc` can be assigned with one stat instance being added in blk_cgroup_bio_start(), then the local list in __blkcg_rstat_flush() could be corrupted. Fix the issue by adding one barrier. | 2024-06-24 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: genirq/irqdesc: Prevent use-after-free in irq_find_at_or_after() irq_find_at_or_after() dereferences the interrupt descriptor which is returned by mt_find() while neither holding sparse_irq_lock nor RCU read lock, which means the descriptor can be freed between mt_find() and the dereference: CPU0 CPU1 desc = mt_find() delayed_free_desc(desc) irq_desc_get_irq(desc) The use-after-free is reported by KASAN: Call trace: irq_get_next_irq+0x58/0x84 show_stat+0x638/0x824 seq_read_iter+0x158/0x4ec proc_reg_read_iter+0x94/0x12c vfs_read+0x1e0/0x2c8 Freed by task 4471: slab_free_freelist_hook+0x174/0x1e0 __kmem_cache_free+0xa4/0x1dc kfree+0x64/0x128 irq_kobj_release+0x28/0x3c kobject_put+0xcc/0x1e0 delayed_free_desc+0x14/0x2c rcu_do_batch+0x214/0x720 Guard the access with a RCU read lock section. | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: s390/ap: Fix crash in AP internal function modify_bitmap() A system crash like this Failing address: 200000cb7df6f000 TEID: 200000cb7df6f403 Fault in home space mode while using kernel ASCE. AS:00000002d71bc007 R3:00000003fe5b8007 S:000000011a446000 P:000000015660c13d Oops: 0038 ilc:3 [#1] PREEMPT SMP Modules linked in: mlx5_ib ... CPU: 8 PID: 7556 Comm: bash Not tainted 6.9.0-rc7 #8 Hardware name: IBM 3931 A01 704 (LPAR) Krnl PSW : 0704e00180000000 0000014b75e7b606 (ap_parse_bitmap_str+0x10e/0x1f8) R:0 T:1 IO:1 EX:1 Key:0 M:1 W:0 P:0 AS:3 CC:2 PM:0 RI:0 EA:3 Krnl GPRS: 0000000000000001 ffffffffffffffc0 0000000000000001 00000048f96b75d3 000000cb00000100 ffffffffffffffff ffffffffffffffff 000000cb7df6fce0 000000cb7df6fce0 00000000ffffffff 000000000000002b 00000048ffffffff 000003ff9b2dbc80 200000cb7df6fcd8 0000014bffffffc0 000000cb7df6fbc8 Krnl Code: 0000014b75e7b5fc: a7840047 brc 8,0000014b75e7b68a 0000014b75e7b600: 18b2 lr %r11,%r2 #0000014b75e7b602: a7f4000a brc 15,0000014b75e7b616 >0000014b75e7b606: eb22d00000e6 laog %r2,%r2,0(%r13) 0000014b75e7b60c: a7680001 lhi %r6,1 0000014b75e7b610: 187b lr %r7,%r11 0000014b75e7b612: 84960021 brxh %r9,%r6,0000014b75e7b654 0000014b75e7b616: 18e9 lr %r14,%r9 Call Trace: [<0000014b75e7b606>] ap_parse_bitmap_str+0x10e/0x1f8 ([<0000014b75e7b5dc>] ap_parse_bitmap_str+0xe4/0x1f8) [<0000014b75e7b758>] apmask_store+0x68/0x140 [<0000014b75679196>] kernfs_fop_write_iter+0x14e/0x1e8 [<0000014b75598524>] vfs_write+0x1b4/0x448 [<0000014b7559894c>] ksys_write+0x74/0x100 [<0000014b7618a440>] __do_syscall+0x268/0x328 [<0000014b761a3558>] system_call+0x70/0x98 INFO: lockdep is turned off. Last Breaking-Event-Address: [<0000014b75e7b636>] ap_parse_bitmap_str+0x13e/0x1f8 Kernel panic - not syncing: Fatal exception: panic_on_oops occured when /sys/bus/ap/a[pq]mask was updated with a relative mask value (like +0x10-0x12,+60,-90) with one of the numeric values exceeding INT_MAX. The fix is simple: use unsigned long values for the internal variables. The correct checks are already in place in the function but a simple int for the internal variables was used with the possibility to overflow. | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: blk-cgroup: fix list corruption from resetting io stat Since commit 3b8cc6298724 ("blk-cgroup: Optimize blkcg_rstat_flush()"), each iostat instance is added to blkcg percpu list, so blkcg_reset_stats() can't reset the stat instance by memset(), otherwise the llist may be corrupted. Fix the issue by only resetting the counter part. | 2024-06-24 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: ext4: fix mb_cache_entry's e_refcnt leak in ext4_xattr_block_cache_find() Syzbot reports a warning as follows: ============================================ WARNING: CPU: 0 PID: 5075 at fs/mbcache.c:419 mb_cache_destroy+0x224/0x290 Modules linked in: CPU: 0 PID: 5075 Comm: syz-executor199 Not tainted 6.9.0-rc6-gb947cc5bf6d7 RIP: 0010:mb_cache_destroy+0x224/0x290 fs/mbcache.c:419 Call Trace: <TASK> ext4_put_super+0x6d4/0xcd0 fs/ext4/super.c:1375 generic_shutdown_super+0x136/0x2d0 fs/super.c:641 kill_block_super+0x44/0x90 fs/super.c:1675 ext4_kill_sb+0x68/0xa0 fs/ext4/super.c:7327 [...] ============================================ This is because when finding an entry in ext4_xattr_block_cache_find(), if ext4_sb_bread() returns -ENOMEM, the ce's e_refcnt, which has already grown in the __entry_find(), won't be put away, and eventually trigger the above issue in mb_cache_destroy() due to reference count leakage. So call mb_cache_entry_put() on the -ENOMEM error branch as a quick fix. | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: Revert "xsk: Support redirect to any socket bound to the same umem" This reverts commit 2863d665ea41282379f108e4da6c8a2366ba66db. This patch introduced a potential kernel crash when multiple napi instances redirect to the same AF_XDP socket. By removing the queue_index check, it is possible for multiple napi instances to access the Rx ring at the same time, which will result in a corrupted ring state which can lead to a crash when flushing the rings in __xsk_flush(). This can happen when the linked list of sockets to flush gets corrupted by concurrent accesses. A quick and small fix is not possible, so let us revert this for now. | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: bonding: fix oops during rmmod "rmmod bonding" causes an oops ever since commit cc317ea3d927 ("bonding: remove redundant NULL check in debugfs function"). Here are the relevant functions being called: bonding_exit() bond_destroy_debugfs() debugfs_remove_recursive(bonding_debug_root); bonding_debug_root = NULL; <--------- SET TO NULL HERE bond_netlink_fini() rtnl_link_unregister() __rtnl_link_unregister() unregister_netdevice_many_notify() bond_uninit() bond_debug_unregister() (commit removed check for bonding_debug_root == NULL) debugfs_remove() simple_recursive_removal() down_write() -> OOPS However, reverting the bad commit does not solve the problem completely because the original code contains a race that could cause the same oops, although it was much less likely to be triggered unintentionally: CPU1 rmmod bonding bonding_exit() bond_destroy_debugfs() debugfs_remove_recursive(bonding_debug_root); CPU2 echo -bond0 > /sys/class/net/bonding_masters bond_uninit() bond_debug_unregister() if (!bonding_debug_root) CPU1 bonding_debug_root = NULL; So do NOT revert the bad commit (since the removed checks were racy anyway), and instead change the order of actions taken during module removal. The same oops can also happen if there is an error during module init, so apply the same fix there. | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: mm/memory-failure: fix handling of dissolved but not taken off from buddy pages When I did memory failure tests recently, below panic occurs: page: refcount:0 mapcount:0 mapping:0000000000000000 index:0x0 pfn:0x8cee00 flags: 0x6fffe0000000000(node=1|zone=2|lastcpupid=0x7fff) raw: 06fffe0000000000 dead000000000100 dead000000000122 0000000000000000 raw: 0000000000000000 0000000000000009 00000000ffffffff 0000000000000000 page dumped because: VM_BUG_ON_PAGE(!PageBuddy(page)) ------------[ cut here ]------------ kernel BUG at include/linux/page-flags.h:1009! invalid opcode: 0000 [#1] PREEMPT SMP NOPTI RIP: 0010:__del_page_from_free_list+0x151/0x180 RSP: 0018:ffffa49c90437998 EFLAGS: 00000046 RAX: 0000000000000035 RBX: 0000000000000009 RCX: ffff8dd8dfd1c9c8 RDX: 0000000000000000 RSI: 0000000000000027 RDI: ffff8dd8dfd1c9c0 RBP: ffffd901233b8000 R08: ffffffffab5511f8 R09: 0000000000008c69 R10: 0000000000003c15 R11: ffffffffab5511f8 R12: ffff8dd8fffc0c80 R13: 0000000000000001 R14: ffff8dd8fffc0c80 R15: 0000000000000009 FS: 00007ff916304740(0000) GS:ffff8dd8dfd00000(0000) knlGS:0000000000000000 CS: 0010 DS: 0000 ES: 0000 CR0: 0000000080050033 CR2: 000055eae50124c8 CR3: 00000008479e0000 CR4: 00000000000006f0 Call Trace: <TASK> __rmqueue_pcplist+0x23b/0x520 get_page_from_freelist+0x26b/0xe40 __alloc_pages_noprof+0x113/0x1120 __folio_alloc_noprof+0x11/0xb0 alloc_buddy_hugetlb_folio.isra.0+0x5a/0x130 __alloc_fresh_hugetlb_folio+0xe7/0x140 alloc_pool_huge_folio+0x68/0x100 set_max_huge_pages+0x13d/0x340 hugetlb_sysctl_handler_common+0xe8/0x110 proc_sys_call_handler+0x194/0x280 vfs_write+0x387/0x550 ksys_write+0x64/0xe0 do_syscall_64+0xc2/0x1d0 entry_SYSCALL_64_after_hwframe+0x77/0x7f RIP: 0033:0x7ff916114887 RSP: 002b:00007ffec8a2fd78 EFLAGS: 00000246 ORIG_RAX: 0000000000000001 RAX: ffffffffffffffda RBX: 000055eae500e350 RCX: 00007ff916114887 RDX: 0000000000000004 RSI: 000055eae500e390 RDI: 0000000000000003 RBP: 000055eae50104c0 R08: 0000000000000000 R09: 000055eae50104c0 R10: 0000000000000077 R11: 0000000000000246 R12: 0000000000000004 R13: 0000000000000004 R14: 00007ff916216b80 R15: 00007ff916216a00 </TASK> Modules linked in: mce_inject hwpoison_inject ---[ end trace 0000000000000000 ]--- And before the panic, there had an warning about bad page state: BUG: Bad page state in process page-types pfn:8cee00 page: refcount:0 mapcount:0 mapping:0000000000000000 index:0x0 pfn:0x8cee00 flags: 0x6fffe0000000000(node=1|zone=2|lastcpupid=0x7fff) page_type: 0xffffff7f(buddy) raw: 06fffe0000000000 ffffd901241c0008 ffffd901240f8008 0000000000000000 raw: 0000000000000000 0000000000000009 00000000ffffff7f 0000000000000000 page dumped because: nonzero mapcount Modules linked in: mce_inject hwpoison_inject CPU: 8 PID: 154211 Comm: page-types Not tainted 6.9.0-rc4-00499-g5544ec3178e2-dirty #22 Call Trace: <TASK> dump_stack_lvl+0x83/0xa0 bad_page+0x63/0xf0 free_unref_page+0x36e/0x5c0 unpoison_memory+0x50b/0x630 simple_attr_write_xsigned.constprop.0.isra.0+0xb3/0x110 debugfs_attr_write+0x42/0x60 full_proxy_write+0x5b/0x80 vfs_write+0xcd/0x550 ksys_write+0x64/0xe0 do_syscall_64+0xc2/0x1d0 entry_SYSCALL_64_after_hwframe+0x77/0x7f RIP: 0033:0x7f189a514887 RSP: 002b:00007ffdcd899718 EFLAGS: 00000246 ORIG_RAX: 0000000000000001 RAX: ffffffffffffffda RBX: 0000000000000000 RCX: 00007f189a514887 RDX: 0000000000000009 RSI: 00007ffdcd899730 RDI: 0000000000000003 RBP: 00007ffdcd8997a0 R08: 0000000000000000 R09: 00007ffdcd8994b2 R10: 0000000000000000 R11: 0000000000000246 R12: 00007ffdcda199a8 R13: 0000000000404af1 R14: 000000000040ad78 R15: 00007f189a7a5040 </TASK> The root cause should be the below race: memory_failure try_memory_failure_hugetlb me_huge_page __page_handle_poison dissolve_free_hugetlb_folio drain_all_pages -- Buddy page can be isolated e.g. for compaction. take_page_off_buddy -- Failed as page is not in the ---truncated--- | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: net/9p: fix uninit-value in p9_client_rpc() Syzbot with the help of KMSAN reported the following error: BUG: KMSAN: uninit-value in trace_9p_client_res include/trace/events/9p.h:146 [inline] BUG: KMSAN: uninit-value in p9_client_rpc+0x1314/0x1340 net/9p/client.c:754 trace_9p_client_res include/trace/events/9p.h:146 [inline] p9_client_rpc+0x1314/0x1340 net/9p/client.c:754 p9_client_create+0x1551/0x1ff0 net/9p/client.c:1031 v9fs_session_init+0x1b9/0x28e0 fs/9p/v9fs.c:410 v9fs_mount+0xe2/0x12b0 fs/9p/vfs_super.c:122 legacy_get_tree+0x114/0x290 fs/fs_context.c:662 vfs_get_tree+0xa7/0x570 fs/super.c:1797 do_new_mount+0x71f/0x15e0 fs/namespace.c:3352 path_mount+0x742/0x1f20 fs/namespace.c:3679 do_mount fs/namespace.c:3692 [inline] __do_sys_mount fs/namespace.c:3898 [inline] __se_sys_mount+0x725/0x810 fs/namespace.c:3875 __x64_sys_mount+0xe4/0x150 fs/namespace.c:3875 do_syscall_64+0xd5/0x1f0 entry_SYSCALL_64_after_hwframe+0x6d/0x75 Uninit was created at: __alloc_pages+0x9d6/0xe70 mm/page_alloc.c:4598 __alloc_pages_node include/linux/gfp.h:238 [inline] alloc_pages_node include/linux/gfp.h:261 [inline] alloc_slab_page mm/slub.c:2175 [inline] allocate_slab mm/slub.c:2338 [inline] new_slab+0x2de/0x1400 mm/slub.c:2391 ___slab_alloc+0x1184/0x33d0 mm/slub.c:3525 __slab_alloc mm/slub.c:3610 [inline] __slab_alloc_node mm/slub.c:3663 [inline] slab_alloc_node mm/slub.c:3835 [inline] kmem_cache_alloc+0x6d3/0xbe0 mm/slub.c:3852 p9_tag_alloc net/9p/client.c:278 [inline] p9_client_prepare_req+0x20a/0x1770 net/9p/client.c:641 p9_client_rpc+0x27e/0x1340 net/9p/client.c:688 p9_client_create+0x1551/0x1ff0 net/9p/client.c:1031 v9fs_session_init+0x1b9/0x28e0 fs/9p/v9fs.c:410 v9fs_mount+0xe2/0x12b0 fs/9p/vfs_super.c:122 legacy_get_tree+0x114/0x290 fs/fs_context.c:662 vfs_get_tree+0xa7/0x570 fs/super.c:1797 do_new_mount+0x71f/0x15e0 fs/namespace.c:3352 path_mount+0x742/0x1f20 fs/namespace.c:3679 do_mount fs/namespace.c:3692 [inline] __do_sys_mount fs/namespace.c:3898 [inline] __se_sys_mount+0x725/0x810 fs/namespace.c:3875 __x64_sys_mount+0xe4/0x150 fs/namespace.c:3875 do_syscall_64+0xd5/0x1f0 entry_SYSCALL_64_after_hwframe+0x6d/0x75 If p9_check_errors() fails early in p9_client_rpc(), req->rc.tag will not be properly initialized. However, trace_9p_client_res() ends up trying to print it out anyway before p9_client_rpc() finishes. Fix this issue by assigning default values to p9_fcall fields such as 'tag' and (just in case KMSAN unearths something new) 'id' during the tag allocation stage. | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: i2c: acpi: Unbind mux adapters before delete There is an issue with ACPI overlay table removal specifically related to I2C multiplexers. Consider an ACPI SSDT Overlay that defines a PCA9548 I2C mux on an existing I2C bus. When this table is loaded we see the creation of a device for the overall PCA9548 chip and 8 further devices - one i2c_adapter each for the mux channels. These are all bound to their ACPI equivalents via an eventual invocation of acpi_bind_one(). When we unload the SSDT overlay we run into the problem. The ACPI devices are deleted as normal via acpi_device_del_work_fn() and the acpi_device_del_list. However, the following warning and stack trace is output as the deletion does not go smoothly: ------------[ cut here ]------------ kernfs: can not remove 'physical_node', no directory WARNING: CPU: 1 PID: 11 at fs/kernfs/dir.c:1674 kernfs_remove_by_name_ns+0xb9/0xc0 Modules linked in: CPU: 1 PID: 11 Comm: kworker/u128:0 Not tainted 6.8.0-rc6+ #1 Hardware name: congatec AG conga-B7E3/conga-B7E3, BIOS 5.13 05/16/2023 Workqueue: kacpi_hotplug acpi_device_del_work_fn RIP: 0010:kernfs_remove_by_name_ns+0xb9/0xc0 Code: e4 00 48 89 ef e8 07 71 db ff 5b b8 fe ff ff ff 5d 41 5c 41 5d e9 a7 55 e4 00 0f 0b eb a6 48 c7 c7 f0 38 0d 9d e8 97 0a d5 ff <0f> 0b eb dc 0f 1f 00 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 RSP: 0018:ffff9f864008fb28 EFLAGS: 00010286 RAX: 0000000000000000 RBX: ffff8ef90a8d4940 RCX: 0000000000000000 RDX: ffff8f000e267d10 RSI: ffff8f000e25c780 RDI: ffff8f000e25c780 RBP: ffff8ef9186f9870 R08: 0000000000013ffb R09: 00000000ffffbfff R10: 00000000ffffbfff R11: ffff8f000e0a0000 R12: ffff9f864008fb50 R13: ffff8ef90c93dd60 R14: ffff8ef9010d0958 R15: ffff8ef9186f98c8 FS: 0000000000000000(0000) GS:ffff8f000e240000(0000) knlGS:0000000000000000 CS: 0010 DS: 0000 ES: 0000 CR0: 0000000080050033 CR2: 00007f48f5253a08 CR3: 00000003cb82e000 CR4: 00000000003506f0 Call Trace: <TASK> ? kernfs_remove_by_name_ns+0xb9/0xc0 ? __warn+0x7c/0x130 ? kernfs_remove_by_name_ns+0xb9/0xc0 ? report_bug+0x171/0x1a0 ? handle_bug+0x3c/0x70 ? exc_invalid_op+0x17/0x70 ? asm_exc_invalid_op+0x1a/0x20 ? kernfs_remove_by_name_ns+0xb9/0xc0 ? kernfs_remove_by_name_ns+0xb9/0xc0 acpi_unbind_one+0x108/0x180 device_del+0x18b/0x490 ? srso_return_thunk+0x5/0x5f ? srso_return_thunk+0x5/0x5f device_unregister+0xd/0x30 i2c_del_adapter.part.0+0x1bf/0x250 i2c_mux_del_adapters+0xa1/0xe0 i2c_device_remove+0x1e/0x80 device_release_driver_internal+0x19a/0x200 bus_remove_device+0xbf/0x100 device_del+0x157/0x490 ? __pfx_device_match_fwnode+0x10/0x10 ? srso_return_thunk+0x5/0x5f device_unregister+0xd/0x30 i2c_acpi_notify+0x10f/0x140 notifier_call_chain+0x58/0xd0 blocking_notifier_call_chain+0x3a/0x60 acpi_device_del_work_fn+0x85/0x1d0 process_one_work+0x134/0x2f0 worker_thread+0x2f0/0x410 ? __pfx_worker_thread+0x10/0x10 kthread+0xe3/0x110 ? __pfx_kthread+0x10/0x10 ret_from_fork+0x2f/0x50 ? __pfx_kthread+0x10/0x10 ret_from_fork_asm+0x1b/0x30 </TASK> ---[ end trace 0000000000000000 ]--- ... repeated 7 more times, 1 for each channel of the mux ... The issue is that the binding of the ACPI devices to their peer I2C adapters is not correctly cleaned up. Digging deeper into the issue we see that the deletion order is such that the ACPI devices matching the mux channel i2c adapters are deleted first during the SSDT overlay removal. For each of the channels we see a call to i2c_acpi_notify() with ACPI_RECONFIG_DEVICE_REMOVE but, because these devices are not actually i2c_clients, nothing is done for them. Later on, after each of the mux channels has been dealt with, we come to delete the i2c_client representing the PCA9548 device. This is the call stack we see above, whereby the kernel cleans up the i2c_client including destruction of the mux and its channel adapters. At this point we do attempt to unbind from the ACPI peers but those peers ---truncated--- | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: io_uring: check for non-NULL file pointer in io_file_can_poll() In earlier kernels, it was possible to trigger a NULL pointer dereference off the forced async preparation path, if no file had been assigned. The trace leading to that looks as follows: BUG: kernel NULL pointer dereference, address: 00000000000000b0 PGD 0 P4D 0 Oops: 0000 [#1] PREEMPT SMP CPU: 67 PID: 1633 Comm: buf-ring-invali Not tainted 6.8.0-rc3+ #1 Hardware name: QEMU Standard PC (i440FX + PIIX, 1996), BIOS unknown 2/2/2022 RIP: 0010:io_buffer_select+0xc3/0x210 Code: 00 00 48 39 d1 0f 82 ae 00 00 00 48 81 4b 48 00 00 01 00 48 89 73 70 0f b7 50 0c 66 89 53 42 85 ed 0f 85 d2 00 00 00 48 8b 13 <48> 8b 92 b0 00 00 00 48 83 7a 40 00 0f 84 21 01 00 00 4c 8b 20 5b RSP: 0018:ffffb7bec38c7d88 EFLAGS: 00010246 RAX: ffff97af2be61000 RBX: ffff97af234f1700 RCX: 0000000000000040 RDX: 0000000000000000 RSI: ffff97aecfb04820 RDI: ffff97af234f1700 RBP: 0000000000000000 R08: 0000000000200030 R09: 0000000000000020 R10: ffffb7bec38c7dc8 R11: 000000000000c000 R12: ffffb7bec38c7db8 R13: ffff97aecfb05800 R14: ffff97aecfb05800 R15: ffff97af2be5e000 FS: 00007f852f74b740(0000) GS:ffff97b1eeec0000(0000) knlGS:0000000000000000 CS: 0010 DS: 0000 ES: 0000 CR0: 0000000080050033 CR2: 00000000000000b0 CR3: 000000016deab005 CR4: 0000000000370ef0 Call Trace: <TASK> ? __die+0x1f/0x60 ? page_fault_oops+0x14d/0x420 ? do_user_addr_fault+0x61/0x6a0 ? exc_page_fault+0x6c/0x150 ? asm_exc_page_fault+0x22/0x30 ? io_buffer_select+0xc3/0x210 __io_import_iovec+0xb5/0x120 io_readv_prep_async+0x36/0x70 io_queue_sqe_fallback+0x20/0x260 io_submit_sqes+0x314/0x630 __do_sys_io_uring_enter+0x339/0xbc0 ? __do_sys_io_uring_register+0x11b/0xc50 ? vm_mmap_pgoff+0xce/0x160 do_syscall_64+0x5f/0x180 entry_SYSCALL_64_after_hwframe+0x46/0x4e RIP: 0033:0x55e0a110a67e Code: ba cc 00 00 00 45 31 c0 44 0f b6 92 d0 00 00 00 31 d2 41 b9 08 00 00 00 41 83 e2 01 41 c1 e2 04 41 09 c2 b8 aa 01 00 00 0f 05 <c3> 90 89 30 eb a9 0f 1f 40 00 48 8b 42 20 8b 00 a8 06 75 af 85 f6 because the request is marked forced ASYNC and has a bad file fd, and hence takes the forced async prep path. Current kernels with the request async prep cleaned up can no longer hit this issue, but for ease of backporting, let's add this safety check in here too as it really doesn't hurt. For both cases, this will inevitably end with a CQE posted with -EBADF. | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: clk: bcm: rpi: Assign ->num before accessing ->hws Commit f316cdff8d67 ("clk: Annotate struct clk_hw_onecell_data with __counted_by") annotated the hws member of 'struct clk_hw_onecell_data' with __counted_by, which informs the bounds sanitizer about the number of elements in hws, so that it can warn when hws is accessed out of bounds. As noted in that change, the __counted_by member must be initialized with the number of elements before the first array access happens, otherwise there will be a warning from each access prior to the initialization because the number of elements is zero. This occurs in raspberrypi_discover_clocks() due to ->num being assigned after ->hws has been accessed: UBSAN: array-index-out-of-bounds in drivers/clk/bcm/clk-raspberrypi.c:374:4 index 3 is out of range for type 'struct clk_hw *[] __counted_by(num)' (aka 'struct clk_hw *[]') Move the ->num initialization to before the first access of ->hws, which clears up the warning. | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: clk: bcm: dvp: Assign ->num before accessing ->hws Commit f316cdff8d67 ("clk: Annotate struct clk_hw_onecell_data with __counted_by") annotated the hws member of 'struct clk_hw_onecell_data' with __counted_by, which informs the bounds sanitizer about the number of elements in hws, so that it can warn when hws is accessed out of bounds. As noted in that change, the __counted_by member must be initialized with the number of elements before the first array access happens, otherwise there will be a warning from each access prior to the initialization because the number of elements is zero. This occurs in clk_dvp_probe() due to ->num being assigned after ->hws has been accessed: UBSAN: array-index-out-of-bounds in drivers/clk/bcm/clk-bcm2711-dvp.c:59:2 index 0 is out of range for type 'struct clk_hw *[] __counted_by(num)' (aka 'struct clk_hw *[]') Move the ->num initialization to before the first access of ->hws, which clears up the warning. | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: 9p: add missing locking around taking dentry fid list Fix a use-after-free on dentry's d_fsdata fid list when a thread looks up a fid through dentry while another thread unlinks it: UAF thread: refcount_t: addition on 0; use-after-free. p9_fid_get linux/./include/net/9p/client.h:262 v9fs_fid_find+0x236/0x280 linux/fs/9p/fid.c:129 v9fs_fid_lookup_with_uid linux/fs/9p/fid.c:181 v9fs_fid_lookup+0xbf/0xc20 linux/fs/9p/fid.c:314 v9fs_vfs_getattr_dotl+0xf9/0x360 linux/fs/9p/vfs_inode_dotl.c:400 vfs_statx+0xdd/0x4d0 linux/fs/stat.c:248 Freed by: p9_fid_destroy (inlined) p9_client_clunk+0xb0/0xe0 linux/net/9p/client.c:1456 p9_fid_put linux/./include/net/9p/client.h:278 v9fs_dentry_release+0xb5/0x140 linux/fs/9p/vfs_dentry.c:55 v9fs_remove+0x38f/0x620 linux/fs/9p/vfs_inode.c:518 vfs_unlink+0x29a/0x810 linux/fs/namei.c:4335 The problem is that d_fsdata was not accessed under d_lock, because d_release() normally is only called once the dentry is otherwise no longer accessible but since we also call it explicitly in v9fs_remove that lock is required: move the hlist out of the dentry under lock then unref its fids once they are no longer accessible. | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: media: v4l: async: Fix notifier list entry init struct v4l2_async_notifier has several list_head members, but only waiting_list and done_list are initialized. notifier_entry was kept 'zeroed' leading to an uninitialized list_head. This results in a NULL-pointer dereference if csi2_async_register() fails, e.g. node for remote endpoint is disabled, and returns -ENOTCONN. The following calls to v4l2_async_nf_unregister() results in a NULL pointer dereference. Add the missing list head initializer. | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: media: mgb4: Fix double debugfs remove Fixes an error where debugfs_remove_recursive() is called first on a parent directory and then again on a child which causes a kernel panic. [hverkuil: added Fixes/Cc tags] | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: thermal/drivers/qcom/lmh: Check for SCM availability at probe Up until now, the necessary scm availability check has not been performed, leading to possible null pointer dereferences (which did happen for me on RB1). Fix that. | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: f2fs: fix to do sanity check on i_xattr_nid in sanity_check_inode() syzbot reports a kernel bug as below: F2FS-fs (loop0): Mounted with checkpoint version = 48b305e4 ================================================================== BUG: KASAN: slab-out-of-bounds in f2fs_test_bit fs/f2fs/f2fs.h:2933 [inline] BUG: KASAN: slab-out-of-bounds in current_nat_addr fs/f2fs/node.h:213 [inline] BUG: KASAN: slab-out-of-bounds in f2fs_get_node_info+0xece/0x1200 fs/f2fs/node.c:600 Read of size 1 at addr ffff88807a58c76c by task syz-executor280/5076 CPU: 1 PID: 5076 Comm: syz-executor280 Not tainted 6.9.0-rc5-syzkaller #0 Hardware name: Google Google Compute Engine/Google Compute Engine, BIOS Google 03/27/2024 Call Trace: <TASK> __dump_stack lib/dump_stack.c:88 [inline] dump_stack_lvl+0x241/0x360 lib/dump_stack.c:114 print_address_description mm/kasan/report.c:377 [inline] print_report+0x169/0x550 mm/kasan/report.c:488 kasan_report+0x143/0x180 mm/kasan/report.c:601 f2fs_test_bit fs/f2fs/f2fs.h:2933 [inline] current_nat_addr fs/f2fs/node.h:213 [inline] f2fs_get_node_info+0xece/0x1200 fs/f2fs/node.c:600 f2fs_xattr_fiemap fs/f2fs/data.c:1848 [inline] f2fs_fiemap+0x55d/0x1ee0 fs/f2fs/data.c:1925 ioctl_fiemap fs/ioctl.c:220 [inline] do_vfs_ioctl+0x1c07/0x2e50 fs/ioctl.c:838 __do_sys_ioctl fs/ioctl.c:902 [inline] __se_sys_ioctl+0x81/0x170 fs/ioctl.c:890 do_syscall_x64 arch/x86/entry/common.c:52 [inline] do_syscall_64+0xf5/0x240 arch/x86/entry/common.c:83 entry_SYSCALL_64_after_hwframe+0x77/0x7f The root cause is we missed to do sanity check on i_xattr_nid during f2fs_iget(), so that in fiemap() path, current_nat_addr() will access nat_bitmap w/ offset from invalid i_xattr_nid, result in triggering kasan bug report, fix it. | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: smb: client: fix deadlock in smb2_find_smb_tcon() Unlock cifs_tcp_ses_lock before calling cifs_put_smb_ses() to avoid such deadlock. | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: nilfs2: fix nilfs_empty_dir() misjudgment and long loop on I/O errors The error handling in nilfs_empty_dir() when a directory folio/page read fails is incorrect, as in the old ext2 implementation, and if the folio/page cannot be read or nilfs_check_folio() fails, it will falsely determine the directory as empty and corrupt the file system. In addition, since nilfs_empty_dir() does not immediately return on a failed folio/page read, but continues to loop, this can cause a long loop with I/O if i_size of the directory's inode is also corrupted, causing the log writer thread to wait and hang, as reported by syzbot. Fix these issues by making nilfs_empty_dir() immediately return a false value (0) if it fails to get a directory folio/page. | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: eventfs: Fix a possible null pointer dereference in eventfs_find_events() In function eventfs_find_events,there is a potential null pointer that may be caused by calling update_events_attr which will perform some operations on the members of the ei struct when ei is NULL. Hence,When ei->is_freed is set,return NULL directly. | 2024-06-25 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: drm/amdgpu: add error handle to avoid out-of-bounds if the sdma_v4_0_irq_id_to_seq return -EINVAL, the process should be stop to avoid out-of-bounds read, so directly return -EINVAL. | 2024-06-25 | not yet calculated | |
| lunary-ai--lunary-ai/lunary | In lunary-ai/lunary version 1.2.4, an improper access control vulnerability allows members with team management permissions to manipulate project identifiers in requests, enabling them to invite users to projects in other organizations, change members to projects in other organizations with escalated privileges, and change members from other organizations to their own or other projects, also with escalated privileges. This vulnerability is due to the backend's failure to validate project identifiers against the current user's organization ID and projects belonging to it, as well as a misconfiguration in attribute naming (`org_id` should be `orgId`) that prevents proper user organization validation. As a result, attackers can cause inconsistencies on the platform for affected users and organizations, including unauthorized privilege escalation. The issue is present in the backend API endpoints for user invitation and modification, specifically in the handling of project IDs in requests. | 2024-06-27 | not yet calculated | |
| lunary-ai--lunary-ai/lunary | In lunary-ai/lunary versions <=v1.2.11, an attacker can bypass email validation by using a dot character ('.') in the email address. This allows the creation of multiple accounts with essentially the same email address (e.g., '[email protected]' and '[email protected]'), leading to incorrect synchronization and potential security issues. | 2024-06-27 | not yet calculated | |
| lunary-ai--lunary-ai/lunary | In version 1.2.7 of lunary-ai/lunary, any authenticated user, regardless of their role, can change the name of an organization due to improper access control. The function checkAccess() is not implemented, allowing users with the lowest privileges, such as the 'Prompt Editor' role, to modify organization attributes without proper authorization. | 2024-06-27 | not yet calculated | |
| marKoni--Markoni-D (Compact) FM Transmitters | TELSAT marKoni FM Transmitters are vulnerable to a command injection vulnerability through the manipulation of settings and could allow an attacker to gain unauthorized access to the system with administrative privileges. | 2024-06-27 | not yet calculated | |
| marKoni--Markoni-D (Compact) FM Transmitters | TELSAT marKoni FM Transmitters are vulnerable to an attacker exploiting a hidden admin account that can be accessed through the use of hard-coded credentials. | 2024-06-27 | not yet calculated | |
| marKoni--Markoni-D (Compact) FM Transmitters | TELSAT marKoni FM Transmitters are vulnerable to an attacker bypassing authentication and gaining administrator privileges. | 2024-06-27 | not yet calculated | |
| marKoni--Markoni-D (Compact) FM Transmitters | TELSAT marKoni FM Transmitters are vulnerable to users gaining unauthorized access to sensitive information or performing actions beyond their designated permissions. | 2024-06-27 | not yet calculated | |
| mintplex-labs--mintplex-labs/anything-llm | A vulnerability in mintplex-labs/anything-llm allows for a Denial of Service (DoS) condition due to uncontrolled resource consumption. Specifically, the issue arises from the application's failure to limit the size of usernames, enabling attackers to create users with excessively bulky texts in the username field. This exploit results in the user management panel becoming unresponsive, preventing administrators from performing critical user management actions such as editing, suspending, or deleting users. The impact of this vulnerability includes administrative paralysis, compromised security, and operational disruption, as it allows malicious users to perpetuate their presence within the system indefinitely, undermines the system's security posture, and degrades overall system performance. | 2024-06-25 | not yet calculated | |
| mudler--mudler/localai | A command injection vulnerability exists in the mudler/localai version 2.14.0. The vulnerability arises from the application's handling of the backend parameter in the configuration file, which is used in the name of the initialized process. An attacker can exploit this vulnerability by manipulating the path of the vulnerable binary file specified in the backend parameter, allowing the execution of arbitrary code on the system. This issue is due to improper neutralization of special elements used in an OS command, leading to potential full control over the affected system. | 2024-06-26 | not yet calculated | |
| n/a--n/a | In the Linux kernel before 4.8, usb_parse_endpoint in drivers/usb/core/config.c does not validate the wMaxPacketSize field of an endpoint descriptor. NOTE: This vulnerability only affects products that are no longer supported by the supplier. | 2024-06-27 | not yet calculated | |
| n/a--n/a | parseWildcardRules in Gin-Gonic CORS middleware before 1.6.0 mishandles a wildcard at the end of an origin string, e.g., https://example.community/* is allowed when the intention is that only https://example.com/* should be allowed, and http://localhost.example.com/* is allowed when the intention is that only http://localhost/* should be allowed. | 2024-06-29 | not yet calculated | |
| n/a--n/a | File upload vulnerability found in Softexpert Excellence Suite v.2.1 allows attackers to execute arbitrary code via a .php file upload to the form/efms_exec_html/file_upload_parser.php endpoint. | 2024-06-26 | not yet calculated | |
| n/a--n/a | PHP Injection vulnerability in the module "M4 PDF Extensions" (m4pdf) up to version 3.3.2 from PrestaAddons for PrestaShop allows attackers to run arbitrary code via the M4PDF::saveTemplate() method. | 2024-06-24 | not yet calculated | |
| n/a--n/a | In phpseclib before 1.0.22, 2.x before 2.0.46, and 3.x before 3.0.33, some characters in Subject Alternative Name fields in TLS certificates are incorrectly allowed to have a special meaning in regular expressions (such as a + wildcard), leading to name confusion in X.509 certificate host verification. | 2024-06-27 | not yet calculated | |
| n/a--n/a | Geehy APM32F103CCT6, APM32F103RCT6, APM32F103RCT7, and APM32F103VCT6 devices have Incorrect Access Control. | 2024-06-25 | not yet calculated | |
| n/a--n/a | Artery AT32F415CBT7 and AT32F421C8T7 devices have Incorrect Access Control. | 2024-06-25 | not yet calculated | |
| n/a--n/a | GigaDevice GD32E103C8T6 devices have Incorrect Access Control. | 2024-06-25 | not yet calculated | |
| n/a--n/a | An issue was discovered on HMS Anybus X-Gateway AB7832-F 3 devices. The gateway exposes an unidentified service on port 7412 on the network. All the network services of the gateway become unresponsive after sending 85 requests to this port. The content and length of the frame does not matter. The device needs to be restarted to resume operations. | 2024-06-26 | not yet calculated | |
| n/a--n/a | An issue was discovered on HMS Anybus X-Gateway AB7832-F 3 devices. The gateway exposes a web interface on port 80. An unauthenticated GET request to a specific URL triggers the reboot of the Anybus gateway (or at least most of its modules). An attacker can use this feature to carry out a denial of service attack by continuously sending GET requests to that URL. | 2024-06-26 | not yet calculated | |
| n/a--n/a | An issue was discovered on HMS Anybus X-Gateway AB7832-F firmware version 3. The HICP protocol allows unauthenticated changes to a device's network configurations. | 2024-06-26 | not yet calculated | |
| n/a--n/a | Buffer Overflow vulnerability in DCMTK v.3.6.8 allows an attacker to execute arbitrary code via the EctEnhancedCT method component. | 2024-06-28 | not yet calculated | |
| n/a--n/a | An issue in dc2niix before v.1.0.20240202 allows a local attacker to execute arbitrary code via the generated file name is not properly escaped and injected into a system call when certain types of compression are used. | 2024-06-28 | not yet calculated | |
| n/a--n/a | Buffer overflow in the extract_openvpn_cr function in openvpn-cr.c in openvpn-auth-ldap (aka the Three Rings Auth-LDAP plugin for OpenVPN) 2.0.4 allows attackers with a valid LDAP username and who can control the challenge/response password field to pass a string with more than 14 colons into this field and cause a buffer overflow. | 2024-06-27 | not yet calculated | |
| n/a--n/a | Stored Cross Site Scripting vulnerability in Emby Media Server Emby Media Server 4.8.3.0 allows a remote attacker to escalate privileges via the notifications.html component. | 2024-06-25 | not yet calculated | |
| n/a--n/a | DESIGNA ABACUS v.18 and before allows an attacker to bypass the payment process via a crafted QR code. | 2024-06-27 | not yet calculated | |
| n/a--n/a | Buffer Overflow vulnerability in ASUS router RT-AX88U with firmware versions v3.0.0.4.388_24198 allows a remote attacker to execute arbitrary code via the connection_state_machine due to improper length validation for the cookie field. | 2024-06-24 | not yet calculated | |
| n/a--n/a | A cross-site scripting (XSS) vulnerability in the component XsltResultControllerHtml.jsp of Lumisxp v15.0.x to v16.1.x allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into the lumPageID parameter. | 2024-06-26 | not yet calculated | |
| n/a--n/a | A cross-site scripting (XSS) vulnerability in the component UrlAccessibilityEvaluation.jsp of Lumisxp v15.0.x to v16.1.x allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into the contentHtml parameter. | 2024-06-26 | not yet calculated | |
| n/a--n/a | A cross-site scripting (XSS) vulnerability in the component main.jsp of Lumisxp v15.0.x to v16.1.x allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into the pageId parameter. | 2024-06-26 | not yet calculated | |
| n/a--n/a | A hardcoded privileged ID within Lumisxp v15.0.x to v16.1.x allows attackers to bypass authentication and access internal pages and other sensitive information. | 2024-06-26 | not yet calculated | |
| n/a--n/a | Axiros AXESS Auto Configuration Server (ACS) 4.x and 5.0.0 has Incorrect Access Control. An authorization bypass allows remote attackers to achieve unauthenticated remote code execution. | 2024-06-24 | not yet calculated | |
| n/a--n/a | Virtual Programming Lab for Moodle up to v4.2.3 was discovered to contain a cross-site scripting (XSS) vulnerability via the component vplide.js. | 2024-06-24 | not yet calculated | |
| n/a--n/a | An issue in VPL Jail System up to v4.0.2 allows attackers to execute a directory traversal via a crafted request to a public endpoint. | 2024-06-24 | not yet calculated | |
| n/a--n/a | An issue was discovered in VirtoSoftware Virto Kanban Board Web Part before 5.3.5.1 for SharePoint 2019. There is /_layouts/15/Virto.KanbanTaskManager/api/KanbanData.ashx LinkTitle2 XSS. | 2024-06-25 | not yet calculated | |
| n/a--n/a | Apache XML Security for C++ through 2.0.4 implements the XML Signature Syntax and Processing (XMLDsig) specification without protection against an SSRF payload in a KeyInfo element. NOTE: the supplier disputes this CVE Record on the grounds that they are implementing the specification "correctly" and are not "at fault." | 2024-06-26 | not yet calculated | |
| n/a--n/a | The W3C XML Signature Syntax and Processing (XMLDsig) specification, starting with 1.0, was originally published with a "RetrievalMethod is a URI ... that may be used to obtain key and/or certificate information" statement and no accompanying information about SSRF risks, and this may have contributed to vulnerable implementations such as those discussed in CVE-2023-36661 and CVE-2024-21893. NOTE: this was mitigated in 1.1 and 2.0 via a directly referenced Best Practices document that calls on implementers to be wary of SSRF. | 2024-06-26 | not yet calculated | |
| n/a--n/a | SQL injection vulnerability in the module "Complete for Create a Quote in Frontend + Backend Pro" (askforaquotemodul) <= 1.0.51 from Buy Addons for PrestaShop allows attackers to view sensitive information and cause other impacts via methods `AskforaquotemodulcustomernewquoteModuleFrontController::run()`, `AskforaquotemoduladdproductnewquoteModuleFrontController::run()`, `AskforaquotemodulCouponcodeModuleFrontController::run()`, `AskforaquotemodulgetshippingcostModuleFrontController::run()`, `AskforaquotemodulgetstateModuleFrontController::run().` | 2024-06-24 | not yet calculated | |
| n/a--n/a | In the module "Axepta" (axepta) before 1.3.4 from Quadra Informatique for PrestaShop, a guest can download partial credit card information (expiry date) / postal address / email / etc. without restriction due to a lack of permissions control. | 2024-06-24 | not yet calculated | |
| n/a--n/a | SQL Injection vulnerability in the module "Help Desk - Customer Support Management System" (helpdesk) up to version 2.4.0 from FME Modules for PrestaShop allows attackers to obtain sensitive information and cause other impacts via 'Tickets::getsearchedtickets()' | 2024-06-24 | not yet calculated | |
| n/a--n/a | An issue in Daemon PTY Limited FarCry Core framework before 7.2.14 allows attackers to access sensitive information in the /facade directory. | 2024-06-25 | not yet calculated | |
| n/a--n/a | An arbitrary file upload vulnerability in /fileupload/upload.cfm in Daemon PTY Limited FarCry Core framework before 7.2.14 allows attackers to execute arbitrary code via uploading a crafted .cfm file. | 2024-06-25 | not yet calculated | |
| n/a--n/a | MAP-OS v4.45.0 and earlier was discovered to contain a cross-site scripting (XSS) vulnerability. | 2024-06-26 | not yet calculated | |
| n/a--n/a | Directory Traversal vulnerability in Kalkitech ASE ASE61850 IEDSmart upto and including version 2.3.5 allows attackers to read/write arbitrary files via the IEC61850 File Transfer protocol. | 2024-06-27 | not yet calculated | |
| n/a--n/a | Netwrix CoSoSys Endpoint Protector through 5.9.3 and CoSoSys Unify through 7.0.6 contain a remote code execution vulnerability in the logging component of the Endpoint Protector and Unify server application which allows an unauthenticated remote attacker to send a malicious request, resulting in the ability to execute system commands with root privileges. | 2024-06-27 | not yet calculated | |
| n/a--n/a | Netwrix CoSoSys Endpoint Protector through 5.9.3 and CoSoSys Unify through 7.0.6 contain a remote code execution vulnerability in the shadowing component of the Endpoint Protector and Unify agent which allows an attacker with administrative access to the Endpoint Protector or Unify server to overwrite sensitive configuration and subsequently execute system commands with SYSTEM/root privileges on a chosen client endpoint. | 2024-06-27 | not yet calculated | |
| n/a--n/a | Netwrix CoSoSys Endpoint Protector through 5.9.3 and CoSoSys Unify through 7.0.6 contain a remote code execution vulnerability in the Endpoint Protector and Unify agent in the way that the EasyLock dependency is acquired from the server. An attacker with administrative access to the Endpoint Protector or Unify server can cause a client to acquire and execute a malicious file resulting in remote code execution. | 2024-06-27 | not yet calculated | |
| n/a--n/a | Netwrix CoSoSys Endpoint Protector through 5.9.3 and CoSoSys Unify through 7.0.6 contain a remote code execution vulnerability in the application configuration component of the Endpoint Protector and Unify agent which allows a remote, unauthenticated attacker to manipulate the configuration of either their own or another client endpoint resulting in the bypass of certain configuration options. Manipulation of the application configuration can result in local policy bypass and in some scenarios remote code execution. | 2024-06-27 | not yet calculated | |
| n/a--n/a | SQL Injection vulnerability in the module "Isotope" (pk_isotope) <=1.7.3 from Promokit.eu for PrestaShop allows attackers to obtain sensitive information and cause other impacts via `pk_isotope::saveData` and `pk_isotope::removeData` methods. | 2024-06-24 | not yet calculated | |
| n/a--n/a | In the module "Theme settings" (pk_themesettings) <= 1.8.8 from Promokit.eu for PrestaShop, a guest can download all email collected while SHOP is in maintenance mode. Due to a lack of permissions control, a guest can access the txt file which collect email when maintenance is enable which can lead to leak of personal information. | 2024-06-24 | not yet calculated | |
| n/a--n/a | SQL injection vulnerability in the module "Products Alert" (productsalert) before 1.7.4 from Smart Modules for PrestaShop allows attackers to obtain sensitive information and cause other impacts via the ProductsAlertAjaxProcessModuleFrontController::initContent method. | 2024-06-24 | not yet calculated | |
| n/a--n/a | D-Link DIR-1950 up to v1.11B03 does not validate SSL certificates when requesting the latest firmware version and downloading URL. This can allow attackers to downgrade the firmware version or change the downloading URL via a man-in-the-middle attack. | 2024-06-27 | not yet calculated | |
| n/a--n/a | MAP-OS 4.45.0 and earlier is vulnerable to Cross-Site Scripting (XSS). This vulnerability allows malicious users to insert a malicious payload into the "Client Name" input. When a service order from this client is created, the malicious payload is displayed on the administrator and employee dashboards, resulting in unauthorized script execution whenever the dashboard is loaded. | 2024-06-25 | not yet calculated | |
| n/a--n/a | Incorrect access control in Teldat M1 v11.00.05.50.01 allows attackers to obtain sensitive information via a crafted query string. | 2024-06-26 | not yet calculated | |
| n/a--n/a | In MIT Kerberos 5 (aka krb5) before 1.21.3, an attacker can modify the plaintext Extra Count field of a confidential GSS krb5 wrap token, causing the unwrapped token to appear truncated to the application. | 2024-06-28 | not yet calculated | |
| n/a--n/a | In MIT Kerberos 5 (aka krb5) before 1.21.3, an attacker can cause invalid memory reads during GSS message token handling by sending message tokens with invalid length fields. | 2024-06-28 | not yet calculated | |
| n/a--n/a | Buffer Overflow vulnerability in SAS Broker 9.2 build 1495 allows attackers to cause denial of service or obtain sensitive information via crafted payload to the '_debug' parameter. | 2024-06-26 | not yet calculated | |
| n/a--n/a | Cross Site Scripting vulnerability in Hangzhou Meisoft Information Technology Co., Ltd. Finesoft v.8.0 and before allows a remote attacker to execute arbitrary code via a crafted script. | 2024-06-24 | not yet calculated | |
| n/a--n/a | An issue the background management system of Shanxi Internet Chuangxiang Technology Co., Ltd v1.0.1 allows a remote attacker to cause a denial of service via the index.html component. | 2024-06-24 | not yet calculated | |
| n/a--n/a | An issue in OpenEMR 7.0.2 allows a remote attacker to escalate privileges viaa crafted POST request using the noteid parameter. | 2024-06-26 | not yet calculated | |
| n/a--n/a | OpenPLC 3 through 9cd8f1b allows XSS via an SVG document as a profile picture. | 2024-06-28 | not yet calculated | |
| n/a--n/a | Insecure Access Control in Safe Exam Browser (SEB) = 3.5.0 on Windows. The vulnerability allows an attacker to share clipboard data between the SEB kiosk mode and the underlying system, compromising exam integrity. By exploiting this flaw, an attacker can bypass exam controls and gain an unfair advantage during exams. | 2024-06-25 | not yet calculated | |
| n/a--n/a | DataGear v5.0.0 and earlier was discovered to contain a SpEL (Spring Expression Language) expression injection vulnerability via the Data Viewing interface. | 2024-06-24 | not yet calculated | |
| n/a--n/a | A nil pointer dereference in PingCAP TiDB v8.2.0-alpha-216-gfe5858b allows attackers to crash the application via expression.inferCollation. | 2024-06-25 | not yet calculated | |
| n/a--n/a | An issue in EnvisionWare Computer Access & Reservation Control SelfCheck v1.0 (fixed in OneStop 3.2.0.27184 Hotfix May 2024) allows unauthenticated attackers on the same network to perform a directory traversal. | 2024-06-24 | not yet calculated | |
| n/a--n/a | Craft CMS up to v3.7.31 was discovered to contain a SQL injection vulnerability via the GraphQL API endpoint. | 2024-06-25 | not yet calculated | |
| n/a--n/a | An issue in Nepstech Wifi Router xpon (terminal) NTPL-Xpon1GFEVN, hardware verstion 1.0 firmware 2.0.1 allows a remote attacker to execute arbitrary code via the router's Telnet port 2345 without requiring authentication credentials. | 2024-06-25 | not yet calculated | |
| n/a--n/a | An issue in Wavlink WN551K1 allows a remote attacker to obtain sensitive information via the ExportAllSettings.sh component. | 2024-06-24 | not yet calculated | |
| n/a--n/a | WAVLINK WN551K1 found a command injection vulnerability through the IP parameter of /cgi-bin/touchlist_sync.cgi. | 2024-06-24 | not yet calculated | |
| n/a--n/a | WAVLINK WN551K1'live_mfg.shtml enables attackers to obtain sensitive router information. | 2024-06-24 | not yet calculated | |
| n/a--n/a | WAVLINK WN551K1 found a command injection vulnerability through the start_hour parameter of /cgi-bin/nightled.cgi. | 2024-06-24 | not yet calculated | |
| n/a--n/a | WAVLINK WN551K1'live_check.shtml enables attackers to obtain sensitive router information. | 2024-06-24 | not yet calculated | |
| n/a--n/a | H3C Magic R230 V100R002 was discovered to contain a hardcoded password vulnerability in /etc/shadow, which allows attackers to log in as root. | 2024-06-24 | not yet calculated | |
| n/a--n/a | H3C Magic R230 V100R002's udpserver opens port 9034, allowing attackers to execute arbitrary commands. | 2024-06-24 | not yet calculated | |
| n/a--n/a | Heap Buffer Overflow vulnerability in Libde265 v1.0.15 allows attackers to crash the application via crafted payload to display444as420 function at sdl.cc | 2024-06-26 | not yet calculated | |
| n/a--n/a | Heap Buffer Overflow vulnerability in Libde265 v1.0.15 allows attackers to crash the application via crafted payload to __interceptor_memcpy function. | 2024-06-26 | not yet calculated | |
| n/a--n/a | A buffer overflow in PX4-Autopilot v1.12.3 allows attackers to cause a Denial of Service (DoS) via a crafted MavLink message. | 2024-06-25 | not yet calculated | |
| n/a--n/a | PX4-Autopilot v1.14.3 was discovered to contain a buffer overflow via the topic_name parameter at /logger/logged_topics.cpp. | 2024-06-25 | not yet calculated | |
| n/a--n/a | Heap Buffer Overflow vulnerability in DumpTS v0.1.0-nightly allows attackers to cause a denial of service via the function PushTSBuf() at /src/PayloadBuf.cpp. | 2024-06-27 | not yet calculated | |
| n/a--n/a | A NULL Pointer Dereference discovered in DumpTS v0.1.0-nightly allows attackers to cause a denial of service via the function DumpOneStream() at /src/DumpStream.cpp. | 2024-06-27 | not yet calculated | |
| n/a--n/a | A NULL Pointer Dereference vulnerability in DumpTS v0.1.0-nightly allows attackers to cause a denial of service via the function VerifyCommandLine() at /src/DumpTS.cpp. | 2024-06-27 | not yet calculated | |
| n/a--n/a | Heap Buffer Overflow vulnerability in zziplib v0.13.77 allows attackers to cause a denial of service via the __zzip_parse_root_directory() function at /zzip/zip.c. | 2024-06-27 | not yet calculated | |
| n/a--n/a | A Stack Buffer Overflow vulnerability in zziplibv 0.13.77 allows attackers to cause a denial of service via the __zzip_fetch_disk_trailer() function at /zzip/zip.c. | 2024-06-27 | not yet calculated | |
| n/a--n/a | idccms v1.35 was discovered to contain a Cross-Site Request Forgery (CSRF) via the component /admin/info_deal.php?mudi=del&dataType=news&dataTypeCN. | 2024-06-27 | not yet calculated | |
| n/a--n/a | idccms v1.35 was discovered to contain a Cross-Site Request Forgery (CSRF) via the component /admin/keyWord_deal.php?mudi=del&dataType=word&dataTypeCN. | 2024-06-27 | not yet calculated | |
| n/a--n/a | idccms v1.35 was discovered to contain a Cross-Site Request Forgery (CSRF) via the component /admin/ipRecord_deal.php?mudi=add. | 2024-06-27 | not yet calculated | |
| n/a--n/a | idccms v1.35 was discovered to contain a Cross-Site Request Forgery (CSRF) via the component /admin/keyWord_deal.php?mudi=add. | 2024-06-27 | not yet calculated | |
| n/a--n/a | idccms v1.35 was discovered to contain a Cross-Site Request Forgery (CSRF) via the component /admin/ipRecord_deal.php?mudi=del&dataType=&dataID=1. | 2024-06-27 | not yet calculated | |
| n/a--n/a | idccms v1.35 was discovered to contain a Cross-Site Request Forgery (CSRF) via the component /admin/userSys_deal.php?mudi=infoSet. | 2024-06-27 | not yet calculated | |
| n/a--n/a | lua-shmem v1.0-1 was discovered to contain a buffer overflow via the shmem_write function. | 2024-06-27 | not yet calculated | |
| n/a--n/a | luci-app-lucky v2.8.3 was discovered to contain hardcoded credentials. | 2024-06-27 | not yet calculated | |
| n/a--n/a | luci-app-sms-tool v1.9-6 was discovered to contain a command injection vulnerability via the score parameter. | 2024-06-27 | not yet calculated | |
| n/a--n/a | Cross Site Scripting (XSS) vulnerability in skycaiji 2.8 allows attackers to run arbitrary code via /admin/tool/preview. | 2024-06-26 | not yet calculated | |
| n/a--n/a | A cross-site scripting (XSS) vulnerability in skycaiji v2.8 allows attackers to execute arbitrary web scripts or HTML via a crafted payload using eval(String.fromCharCode()). | 2024-06-26 | not yet calculated | |
| n/a--n/a | An issue discovered in skycaiji 2.8 allows attackers to run arbitrary code via crafted POST request to /index.php?s=/admin/develop/editor_save. | 2024-06-26 | not yet calculated | |
| n/a--n/a | Click Studios Passwordstate Core before 9.8 build 9858 allows Authentication Bypass. | 2024-06-24 | not yet calculated | |
| n/a--n/a | In the Console in Soffid IAM before 3.5.39, necessary checks were not applied to some Java objects. A malicious agent could possibly execute arbitrary code in the Sync Server and compromise security. | 2024-06-27 | not yet calculated | |
| n/a--n/a | Soft Circle French-Bread Melty Blood: Actress Again: Current Code through 1.07 Rev. 1.4.0 allows a remote attacker to execute arbitrary code on a client's machine via a crafted packet on TCP port 46318. | 2024-06-28 | not yet calculated | |
| n/a--n/a | NLTK through 3.8.1 allows remote code execution if untrusted packages have pickled Python code, and the integrated data package download functionality is used. This affects, for example, averaged_perceptron_tagger and punkt. | 2024-06-27 | not yet calculated | |
| n/a--n/a | R74n Sandboxels 1.9 through 1.9.5 allows XSS via a message in a modified saved-game file. This was fixed in a hotfix to 1.9.5 on 2024-06-29. | 2024-06-28 | not yet calculated | |
| n/a--n/a | Factorio before 1.1.101 allows a crafted server to execute arbitrary code on clients via a custom map that leverages the ability of certain Lua base module functions to execute bytecode and generate fake objects. | 2024-06-29 | not yet calculated | |
| n/a--n/a | NewPass before 1.2.0 stores passwords (rather than password hashes) directly, which makes it easier to obtain unauthorized access to sensitive information. NOTE: in each case, data at rest is encrypted, but is decrypted within process memory during use. | 2024-06-29 | not yet calculated | |
| n/a--n/a | Internet2 Grouper before 5.6 allows authentication bypass when LDAP authentication is used in certain ways. This is related to internet2.middleware.grouper.ws.security.WsGrouperLdapAuthentication and the use of the UyY29r password for the M3vwHr account. This also affects "Grouper for Web Services" before 4.13.1. | 2024-06-29 | not yet calculated | |
| Nikola Vasilijevski--AdmirorFrames | Full Path Disclosure vulnerability in AdmirorFrames Joomla! extension in afHelper.php script allows an unauthorised attacker to retrieve location of web root folder. This issue affects AdmirorFrames: before 5.0. | 2024-06-28 | not yet calculated | |
| Nikola Vasilijevski--AdmirorFrames | Server Side Request Forgery (SSRF) vulnerability in AdmirorFrames Joomla! extension in afGdStream.php script allows to access local files or server pages available only from localhost. This issue affects AdmirorFrames: before 5.0. | 2024-06-28 | not yet calculated | |
| Nikola Vasilijevski--AdmirorFrames | Script afGdStream.php in AdmirorFrames Joomla! extension doesn't specify a content type and as a result default (text/html) is used. An attacker may embed HTML tags directly in image data which is rendered by a webpage as HTML. This issue affects AdmirorFrames: before 5.0. | 2024-06-28 | not yet calculated | |
| OpenSSL--OpenSSL | Issue summary: Calling the OpenSSL API function SSL_select_next_proto with an empty supported client protocols buffer may cause a crash or memory contents to be sent to the peer. Impact summary: A buffer overread can have a range of potential consequences such as unexpected application beahviour or a crash. In particular this issue could result in up to 255 bytes of arbitrary private data from memory being sent to the peer leading to a loss of confidentiality. However, only applications that directly call the SSL_select_next_proto function with a 0 length list of supported client protocols are affected by this issue. This would normally never be a valid scenario and is typically not under attacker control but may occur by accident in the case of a configuration or programming error in the calling application. The OpenSSL API function SSL_select_next_proto is typically used by TLS applications that support ALPN (Application Layer Protocol Negotiation) or NPN (Next Protocol Negotiation). NPN is older, was never standardised and is deprecated in favour of ALPN. We believe that ALPN is significantly more widely deployed than NPN. The SSL_select_next_proto function accepts a list of protocols from the server and a list of protocols from the client and returns the first protocol that appears in the server list that also appears in the client list. In the case of no overlap between the two lists it returns the first item in the client list. In either case it will signal whether an overlap between the two lists was found. In the case where SSL_select_next_proto is called with a zero length client list it fails to notice this condition and returns the memory immediately following the client list pointer (and reports that there was no overlap in the lists). This function is typically called from a server side application callback for ALPN or a client side application callback for NPN. In the case of ALPN the list of protocols supplied by the client is guaranteed by libssl to never be zero in length. The list of server protocols comes from the application and should never normally be expected to be of zero length. In this case if the SSL_select_next_proto function has been called as expected (with the list supplied by the client passed in the client/client_len parameters), then the application will not be vulnerable to this issue. If the application has accidentally been configured with a zero length server list, and has accidentally passed that zero length server list in the client/client_len parameters, and has additionally failed to correctly handle a "no overlap" response (which would normally result in a handshake failure in ALPN) then it will be vulnerable to this problem. In the case of NPN, the protocol permits the client to opportunistically select a protocol when there is no overlap. OpenSSL returns the first client protocol in the no overlap case in support of this. The list of client protocols comes from the application and should never normally be expected to be of zero length. However if the SSL_select_next_proto function is accidentally called with a client_len of 0 then an invalid memory pointer will be returned instead. If the application uses this output as the opportunistic protocol then the loss of confidentiality will occur. This issue has been assessed as Low severity because applications are most likely to be vulnerable if they are using NPN instead of ALPN - but NPN is not widely used. It also requires an application configuration or programming error. Finally, this issue would not typically be under attacker control making active exploitation unlikely. The FIPS modules in 3.3, 3.2, 3.1 and 3.0 are not affected by this issue. Due to the low severity of this issue we are not issuing new releases of OpenSSL at this time. The fix will be included in the next releases when they become available. | 2024-06-27 | not yet calculated | |
| parisneo--parisneo/lollms-webui | A Path Traversal and Remote File Inclusion (RFI) vulnerability exists in the parisneo/lollms-webui application, affecting versions v9.7 to the latest. The vulnerability arises from insufficient input validation in the `/apply_settings` function, allowing an attacker to manipulate the `discussion_db_name` parameter to traverse the file system and include arbitrary files. This issue is compounded by the bypass of input filtering in the `install_binding`, `reinstall_binding`, and `unInstall_binding` endpoints, despite the presence of a `sanitize_path_from_endpoint(data.name)` filter. Successful exploitation enables an attacker to upload and execute malicious code on the victim's system, leading to Remote Code Execution (RCE). | 2024-06-25 | not yet calculated | |
| parisneo--parisneo/lollms-webui | A Cross-Site Request Forgery (CSRF) vulnerability exists in the 'Servers Configurations' function of the parisneo/lollms-webui, versions 9.6 to the latest. The affected functions include Elastic search Service (under construction), XTTS service, Petals service, vLLM service, and Motion Ctrl service, which lack CSRF protection. This vulnerability allows attackers to deceive users into unwittingly installing the XTTS service among other packages by submitting a malicious installation request. Successful exploitation results in attackers tricking users into performing actions without their consent. | 2024-06-24 | not yet calculated | |
| parisneo--parisneo/lollms-webui | A Cross-site Scripting (XSS) vulnerability exists in the chat functionality of parisneo/lollms-webui in the latest version. This vulnerability allows an attacker to inject malicious scripts via chat messages, which are then executed in the context of the user's browser. | 2024-06-27 | not yet calculated | |
| parisneo--parisneo/lollms-webui | An absolute path traversal vulnerability exists in parisneo/lollms-webui v9.6, specifically in the `open_file` endpoint of `lollms_advanced.py`. The `sanitize_path` function with `allow_absolute_path=True` allows an attacker to access arbitrary files and directories on a Windows system. This vulnerability can be exploited to read any file and list arbitrary directories on the affected system. | 2024-06-27 | not yet calculated | |
| parisneo--parisneo/lollms | A remote code execution vulnerability exists in the create_conda_env function of the parisneo/lollms repository, version 5.9.0. The vulnerability arises from the use of shell=True in the subprocess.Popen function, which allows an attacker to inject arbitrary commands by manipulating the env_name and python_version parameters. This issue could lead to a serious security breach as demonstrated by the ability to execute the 'whoami' command among potentially other harmful commands. | 2024-06-24 | not yet calculated | |
| parisneo--parisneo/lollms | A Cross-Site Request Forgery (CSRF) vulnerability exists in the XTTS server of parisneo/lollms version 9.6 due to a lax CORS policy. The vulnerability allows attackers to perform unauthorized actions by tricking a user into visiting a malicious webpage, which can then trigger arbitrary LoLLMS-XTTS API requests. This issue can lead to the reading and writing of audio files and, when combined with other vulnerabilities, could allow for the reading of arbitrary files on the system and writing files outside the permitted audio file location. | 2024-06-24 | not yet calculated | |
| parisneo--parisneo/lollms | A path traversal vulnerability in the `/set_personality_config` endpoint of parisneo/lollms version 9.4.0 allows an attacker to overwrite the `configs/config.yaml` file. This can lead to remote code execution by changing server configuration properties such as `force_accept_remote_access` and `turn_on_code_validation`. | 2024-06-27 | not yet calculated | |
| parisneo--parisneo/lollms | A path traversal vulnerability exists in the XTTS server included in the lollms package, version v9.6. This vulnerability arises from the ability to perform an unauthenticated root folder settings change. Although the read file endpoint is protected against path traversals, this protection can be bypassed by changing the root folder to '/'. This allows attackers to read arbitrary files on the system. Additionally, the output folders can be changed to write arbitrary audio files to any location on the system. | 2024-06-27 | not yet calculated | |
| parisneo--parisneo/lollms | A path traversal vulnerability exists in the XTTS server of the parisneo/lollms package version v9.6. This vulnerability allows an attacker to write audio files to arbitrary locations on the system and enumerate file paths. The issue arises from improper validation of user-provided file paths in the `tts_to_file` endpoint. | 2024-06-27 | not yet calculated | |
| Perforce--Helix ALM | In Helix ALM versions prior to 2024.2.0, a local command injection was identified. Reported by Bryan Riggins. | 2024-06-28 | not yet calculated | |
| Phloc--Webscopes | An information disclosure vulnerability in Phloc Webscopes 7.0.0 allows local attackers with access to the log files to view logged HTTP requests that contain user passwords or other sensitive information. | 2024-06-25 | not yet calculated | |
| Python Software Foundation--CPython | CPython 3.9 and earlier doesn't disallow configuring an empty list ("[]") for SSLContext.set_npn_protocols() which is an invalid value for the underlying OpenSSL API. This results in a buffer over-read when NPN is used (see CVE-2024-5535 for OpenSSL). This vulnerability is of low severity due to NPN being not widely used and specifying an empty list likely being uncommon in-practice (typically a protocol name would be configured). | 2024-06-27 | not yet calculated | |
| Rockwell Automation--ThinManager ThinServer | Due to an improper input validation, an unauthenticated threat actor can send a malicious message to invoke a local or remote executable and cause a remote code execution condition on the Rockwell Automation ThinManager® ThinServer™. | 2024-06-25 | not yet calculated | |
| Rockwell Automation--ThinManager ThinServer | Due to an improper input validation, an unauthenticated threat actor can send a malicious message to invoke SQL injection into the program and cause a remote code execution condition on the Rockwell Automation ThinManager® ThinServer™. | 2024-06-25 | not yet calculated | |
| Rockwell Automation--ThinManager ThinServer | Due to an improper input validation, an unauthenticated threat actor can send a malicious message to a monitor thread within Rockwell Automation ThinServerâ„¢ and cause a denial-of-service condition on the affected device. | 2024-06-25 | not yet calculated | |
| SDG Technologies--PnPSCADA | SDG Technologies PnPSCADA allows a remote attacker to attach various entities without requiring system authentication. This breach could potentially lead to unauthorized control, data manipulation, and access to sensitive information within the SCADA system. | 2024-06-27 | not yet calculated | |
| SoftMaker Software GmbH--Office | An issue was discovered in SoftMaker Office 2024 / NX before revision 1214 and SoftMaker FreeOffice 2014 before revision 1215. FreeOffice 2021 is also affected, but won't be fixed. The SoftMaker Office and FreeOffice MSI installer files were found to produce a visible conhost.exe window running as the SYSTEM user when using the repair function of msiexec.exe. This allows a local, low-privileged attacker to use a chain of actions, to open a fully functional cmd.exe with the privileges of the SYSTEM user. | 2024-06-27 | not yet calculated | |
| stangirard--stangirard/quivr | stangirard/quivr version 0.0.236 contains a Server-Side Request Forgery (SSRF) vulnerability. The application does not provide sufficient controls when crawling a website, allowing an attacker to access applications on the local network. This vulnerability could allow a malicious user to gain access to internal servers, the AWS metadata endpoint, and capture Supabase data. | 2024-06-27 | not yet calculated | |
| stitionai--stitionai/devika | External Control of File Name or Path in GitHub repository stitionai/devika prior to -. | 2024-06-27 | not yet calculated | |
| stitionai--stitionai/devika | Relative Path Traversal in GitHub repository stitionai/devika prior to -. | 2024-06-27 | not yet calculated | |
| stitionai--stitionai/devika | Path Traversal in GitHub repository stitionai/devika prior to -. | 2024-06-27 | not yet calculated | |
| stitionai--stitionai/devika | Cross-Site Request Forgery (CSRF) in stitionai/devika | 2024-06-28 | not yet calculated | |
| stitionai--stitionai/devika | Missing Authorization in stitionai/devika | 2024-06-27 | not yet calculated | |
| The Document Foundation--LibreOffice | Improper Certificate Validation vulnerability in LibreOffice "LibreOfficeKit" mode disables TLS certification verification LibreOfficeKit can be used for accessing LibreOffice functionality through C/C++. Typically this is used by third party components to reuse LibreOffice as a library to convert, view or otherwise interact with documents. LibreOffice internally makes use of "curl" to fetch remote resources such as images hosted on webservers. In affected versions of LibreOffice, when used in LibreOfficeKit mode only, then curl's TLS certification verification was disabled (CURLOPT_SSL_VERIFYPEER of false) In the fixed versions curl operates in LibreOfficeKit mode the same as in standard mode with CURLOPT_SSL_VERIFYPEER of true. This issue affects LibreOffice before version 24.2.4. | 2024-06-25 | not yet calculated | |
| Unknown--Animated AL List | The Animated AL List WordPress plugin through 1.0.6 does not sanitise and escape a parameter before outputting it back in the page, leading to a Reflected Cross-Site Scripting which could be used against high privilege users such as admin | 2024-06-28 | not yet calculated | |
| Unknown--Bookster | The Bookster WordPress plugin through 1.1.0 allows adding sensitive parameters when validating appointments allowing attackers to manipulate the data sent when booking an appointment (the request body) to change its status from pending to approved. | 2024-06-26 | not yet calculated | |
| Unknown--Easy Table of Contents | The Easy Table of Contents WordPress plugin before 2.0.66 does not sanitise and escape some of its settings, which could allow high privilege users such as editors to perform Cross-Site Scripting attacks even when unfiltered_html is disallowed | 2024-06-26 | not yet calculated | |
| Unknown--Frontend Checklist | The Frontend Checklist WordPress plugin through 2.3.2 does not sanitise and escape some of its settings, which could allow high privilege users such as admin to perform Stored Cross-Site Scripting attacks even when the unfiltered_html capability is disallowed (for example in multisite setup) | 2024-06-26 | not yet calculated | |
| Unknown--Frontend Checklist | The Frontend Checklist WordPress plugin through 2.3.2 does not sanitise and escape some of its settings, which could allow high privilege users such as admin to perform Stored Cross-Site Scripting attacks even when the unfiltered_html capability is disallowed (for example in multisite setup) | 2024-06-26 | not yet calculated | |
| Unknown--Logo Manager For Enamad | The Logo Manager For Enamad WordPress plugin through 0.7.0 does not have CSRF check in some places, and is missing sanitisation as well as escaping, which could allow attackers to make logged in admin add Stored XSS payloads via a CSRF attack | 2024-06-25 | not yet calculated | |
| Unknown--Mime Types Extended | The Mime Types Extended WordPress plugin through 0.11 does not sanitise uploaded SVG files, which could allow users with a role as low as Author to upload a malicious SVG containing XSS payloads. | 2024-06-25 | not yet calculated | |
| Unknown--Muslim Prayer Time BD | The Muslim Prayer Time BD WordPress plugin through 2.4 does not have CSRF check in place when reseting its settings, which could allow attackers to make a logged in admin reset them via a CSRF attack | 2024-06-26 | not yet calculated | |
| Unknown--Pagerank tools | The Pagerank tools WordPress plugin through 1.1.5 does not sanitise and escape a parameter before outputting it back in the page, leading to a Reflected Cross-Site Scripting which could be used against high privilege users such as admin | 2024-06-28 | not yet calculated | |
| Unknown--SEOPress | The SEOPress WordPress plugin before 7.8 does not sanitise and escape some of its Post settings, which could allow high privilege users such as contributor to perform Stored Cross-Site Scripting attacks. | 2024-06-24 | not yet calculated | |
| Unknown--SEOPress | The SEOPress WordPress plugin before 7.8 does not validate and escape one of its Post settings, which could allow contributor and above role to perform Open redirect attacks against any user viewing a malicious post | 2024-06-24 | not yet calculated | |
| Unknown--Simple AL Slider | The Simple AL Slider WordPress plugin through 1.2.10 does not sanitise and escape a parameter before outputting it back in the page, leading to a Reflected Cross-Site Scripting which could be used against high privilege users such as admin | 2024-06-28 | not yet calculated | |
| Unknown--Simple Photoswipe | The Simple Photoswipe WordPress plugin through 0.1 does not sanitise and escape some of its settings, which could allow high privilege users such as admin to perform Stored Cross-Site Scripting attacks even when the unfiltered_html capability is disallowed (for example in multisite setup). | 2024-06-26 | not yet calculated | |
| Unknown--Simple Photoswipe | The Simple Photoswipe WordPress plugin through 0.1 does not have authorisation check when updating its settings, which could allow any authenticated users, such as subscriber to update them | 2024-06-28 | not yet calculated | |
| Unknown--Spotify Play Button | The Spotify Play Button WordPress plugin through 1.0 does not validate and escape some of its shortcode attributes before outputting them back in a page/post where the shortcode is embed, which could allow users with the contributor role and above to perform Stored Cross-Site Scripting attacks. | 2024-06-26 | not yet calculated | |
| Unknown--Video Widget | The Video Widget WordPress plugin through 1.2.3 does not sanitise and escape some of its settings, which could allow high privilege users such as admin to perform Stored Cross-Site Scripting attacks even when the unfiltered_html capability is disallowed (for example in multisite setup) | 2024-06-26 | not yet calculated | |
| Unknown--WebP & SVG Support | The WebP & SVG Support WordPress plugin through 1.4.0 does not sanitise uploaded SVG files, which could allow users with a role as low as Author to upload a malicious SVG containing XSS payloads. | 2024-06-26 | not yet calculated | |
| Unknown--Widget4Call | The Widget4Call WordPress plugin through 1.0.7 does not sanitise and escape a parameter before outputting it back in the page, leading to a Reflected Cross-Site Scripting which could be used against high privilege users such as admin | 2024-06-28 | not yet calculated | |
| vanna-ai--vanna-ai/vanna | In the latest version of vanna-ai/vanna, the `vanna.ask` function is vulnerable to remote code execution due to prompt injection. The root cause is the lack of a sandbox when executing LLM-generated code, allowing an attacker to manipulate the code executed by the `exec` function in `src/vanna/base/base.py`. This vulnerability can be exploited by an attacker to achieve remote code execution on the app backend server, potentially gaining full control of the server. | 2024-06-27 | not yet calculated | |
| vanna-ai--vanna-ai/vanna | Vanna v0.3.4 is vulnerable to SQL injection in its DuckDB integration exposed to its Flask Web APIs. Attackers can inject malicious SQL training data and generate corresponding queries to write arbitrary files on the victim's file system, such as backdoor.php with contents `<?php system($_GET[0]); ?>`. This can lead to command execution or the creation of backdoors. | 2024-06-28 | not yet calculated | |
| Western Digital--My Cloud Home web app | A Cross-Site Scripting (XSS) vulnerability on the My Cloud, My Cloud Home, SanDisk ibi, and WD Cloud web apps was found which could allow an attacker to redirect the user to a crafted domain and reset their credentials, or to execute arbitrary client-side code in the user's browser session to carry out malicious activities.The web apps for these devices have been automatically updated to resolve this vulnerability and improve the security of your devices and data. | 2024-06-24 | not yet calculated | |
| zenml-io--zenml-io/zenml | A denial of service (DoS) vulnerability exists in zenml-io/zenml version 0.56.3 due to improper handling of line feed (`\n`) characters in component names. When a low-privileged user adds a component through the API endpoint `api/v1/workspaces/default/components` with a name containing a `\n` character, it leads to uncontrolled resource consumption. This vulnerability results in the inability of users to add new components in certain categories (e.g., 'Image Builder') and to register new stacks through the UI, thereby degrading the user experience and potentially rendering the ZenML Dashboard unusable. The issue does not affect component addition through the Web UI, as `\n` characters are properly escaped in that context. The vulnerability was tested on ZenML running in Docker, and it was observed in both Firefox and Chrome browsers. | 2024-06-24 | not yet calculated | |
Please share your thoughts
We recently updated our anonymous product survey ; we’d welcome your feedback.

IMAGES
VIDEO
COMMENTS
The Celery distributed task queue is the most commonly used Python library for handling asynchronous tasks and scheduling. The RQ (Redis Queue) is a simple Python library for queueing jobs and processing them in the background with workers. RQ is backed by Redis and is designed to have a low barrier to entry. Taskmaster is a lightweight simple ...
Download and install Redis if you do not already have it installed. Then, install the Python interface: (env)$ pip install redis==4 .5.5. We'll break the logic up into four files: redis_queue.py creates new queues and tasks via the SimpleQueue and SimpleTask classes, respectively.
Part Four: Implement a Redis task queue to handle the text processing. (current) Part Five: Set up Angular on the front-end to continuously poll the back-end to see if the request is done processing. Part Six: Push to the staging server on Heroku - setting up Redis and detailing how to run two processes (web and worker) on a single Dyno.
Taskiq is an asynchronous distributed task queue for python. This project takes inspiration from big projects such as Celery and Dramatiq . But taskiq can send and run both the sync and async functions, has integration with popular async frameworks, such as FastAPI and AioHTTP. Also, we use PEP-612 to provide the best autosuggestions possible.
The count of unfinished tasks goes up whenever an item is added to the queue. The count goes down whenever a consumer thread calls task_done() to indicate that the item was retrieved and all work on it is complete. When the count of unfinished tasks drops to zero, join() unblocks. Example of how to wait for enqueued tasks to be completed:
The task queues are not all compatible with Python but ones that work with it are tagged with the "Python" keyword. Why Task Queues is a presentation for what task queues are and why they are needed. Flask by Example Implementing a Redis Task Queue provides a detailed walkthrough of setting up workers to use RQ with Redis.
RQ ( Redis Queue) is a simple Python library for queueing jobs and processing them in the background with workers. It is backed by Redis and it is designed to have a low barrier to entry. It can be integrated in your web stack easily. RQ requires Redis >= 3.0.0.
Order Queue is a task queue in Celery. A Task Queue is queue of tasks to be executed by workers. NOTE : Celery uses a Message Broker and it's Messaging Queue for it's operations.
RQ ( Redis Queue) is a simple Python library for queueing jobs and processing them in the background with workers. It is backed by Redis and it is designed to have a low barrier to entry. It should be integrated in your web stack easily. RQ requires Redis >= 3.0.0. Full documentation can be found here.
Install python-rq: Create the task which will be actioned by our workers, in our case it will just be a simple function that adds all the numbers from a given string to a list, then adds them up and return the total value. This is however a very basic task, but its just for demonstration. Our tasks.py: return total.
huey is: a task queue ( 2019-04-01: version 2.0 released) written in python (2.7+, 3.4+) clean and simple API. redis, sqlite, or in-memory storage. example code. huey supports: multi-process, multi-thread or greenlet task execution models. schedule tasks to execute at a given time, or after a given delay.
A TaskTiger object keeps track of TaskTiger's settings and is used to decorate and queue tasks. The constructor takes the following arguments: connection. Redis connection object. The connection should be initialized with decode_responses=True to avoid encoding problems on Python 3. config.
Start up the virtual environment again with the command source venv/bin/activate. Then type python app.py to run the project. Go back to the tab that is running rq worker --with-scheduler. Wait 5 more seconds after the first task is executed to see the next task.
Dask and Celery compares Dask.distributed with Celery for Python projects. The post gives code examples to show how to execute tasks with either task queue. Python+Celery: Chaining jobs? explains that Celery tasks should be dependent upon each other using Celery chains, not direct dependencies between tasks. Celery with web frameworks
Now that we are familiar with the Queue.task_done() and Queue.join() functions, let's look at some worked examples. Free Python Threading Course Download your FREE threading PDF cheat sheet and get BONUS access to my free 7-day crash course on the threading API.
First let's create a new directory, create all the files necessary for the project, and then initialize the virtual environment. mkdir celery-python && cd $_. touch __init__.py. touch tasks.py. touch docker-compose.yaml. touch requirements.txt. # create & activate the virtualenv. python -m venv env.
1. Celery is a simple, flexible, and reliable distributed system to process vast amounts of messages, while providing operations with the tools required to maintain such a system. 2. It's a task ...
python-task-queue. A client and system for generating, uploading, leasing, and executing dependency free tasks both locally and in the cloud using AWS SQS or on a single machine or cluster with a common file system using file based queues. ... This first example shows how you might use the queue in the most naive fashion. The tasks list takes a ...
Learn how to implement and use priority queues in Python with this step-by-step tutorial. Discover practical code examples and advanced operations using `heapq` and `queue.PriorityQueue`.
If the queue is full, wait until a free slot is available before adding the item. put_nowait (item) ¶ Put an item into the queue without blocking. If no free slot is immediately available, raise QueueFull. qsize ¶ Return the number of items in the queue. task_done ¶ Indicate that a formerly enqueued task is complete. Used by queue consumers.
Relatively speaking, the performance hit of introducing managers in your code will be noticeable. Firstly, when using Manager.Queue(), everything is pickled/unpickled twice instead of once with a normal queue (once to send to/from manager process and another to retrieve/put object on queue).Secondly, every method call on a managed object takes 1000x more time to resolve before the method is ...
I am looking for a python library / framework that manages task distribution (e.g. a task queue). However, tasks will require specialized workers: Worker A can only handle tasks of type a, workers B and C only of type b etc. Also, these workers will run on different computers and cannot share the same codebase (since, like in a fabrication line, each task is bound to controlling specific ...
I would use method 1; if you need more power you could make a small Python process that monitors the DB queue and starts new processes to handle the tasks. answered Aug 9, 2010 at 10:17. Katriel. 122k 19 137 170. You can leak ressources (forget to close files opened in global namespace etc), but memory doesn't really leak.
Extracting text from an HTML file is a common task in web scraping and data extraction. Python provides powerful libraries such as BeautifulSoup that make this task straightforward. In this article we will explore the process of extracting text from an HTML file using Python. Use the below command to install the BeautifulSoup library:
Queue.task_done lets workers say when a task is done. Someone waiting for all the work to be done with Queue.join will wait until enough task_done calls have been made, not when the queue is empty. eigenfield points out in the comments that it seems really weird for a queue to have task_done / join methods. That's true, but it's really a naming ...
In a Silicon Labs multi-protocol gateway, a corrupt pointer to buffered data on a multi-protocol radio co-processor (RCP) causes the OpenThread Border Router(OTBR) application task running on the host platform to crash, allowing an attacker to cause a temporary denial-of-service. 2024-06-27: 6.5: CVE-2024-3017 [email protected]